WORKFORCE CYBER
INTELLLIGENCE
RESOURCES
A Human-Centric Approach to Operational Awareness and Risk Management

THE LATEST ON WORKFORCE CYBER INTELLIGENCE

Conversations from the Inside, Episode 8: 2024 Insider Risk Investigations Report, The Rise of Foreign Interference
DTEX’s frontline investigators Rajan Koo, Armaan Mahbod and Lynsey Wolf join host Christopher Burgess to unpack the latest findings. Whether…
Read More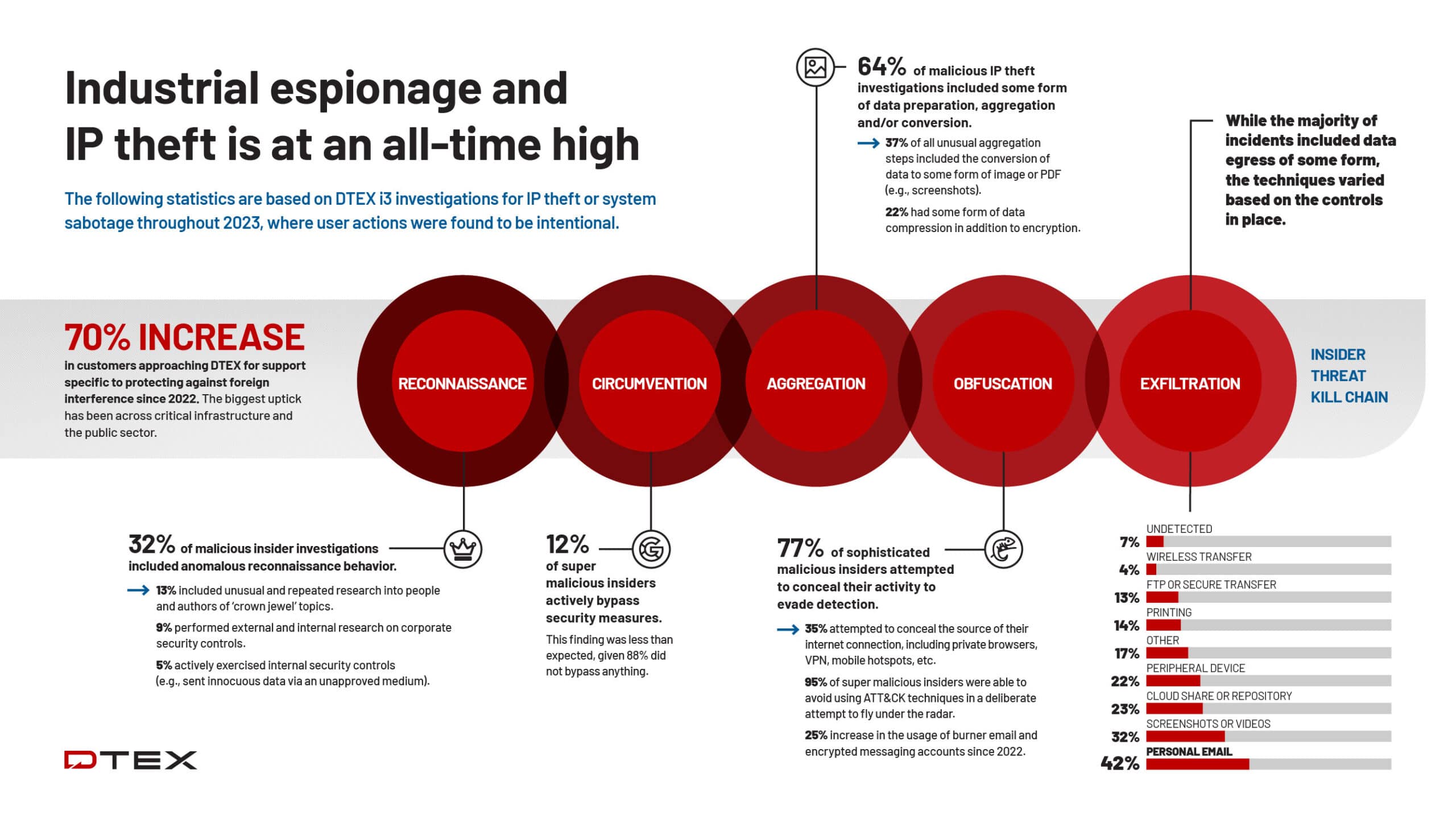
DTEX Insider Threat Kill Chain: Behavioral Insights of Malicious Insiders
The following statistics are based on DTEX i3 investigations for IP theft or system sabotage throughout 2023, where user actions…
Read More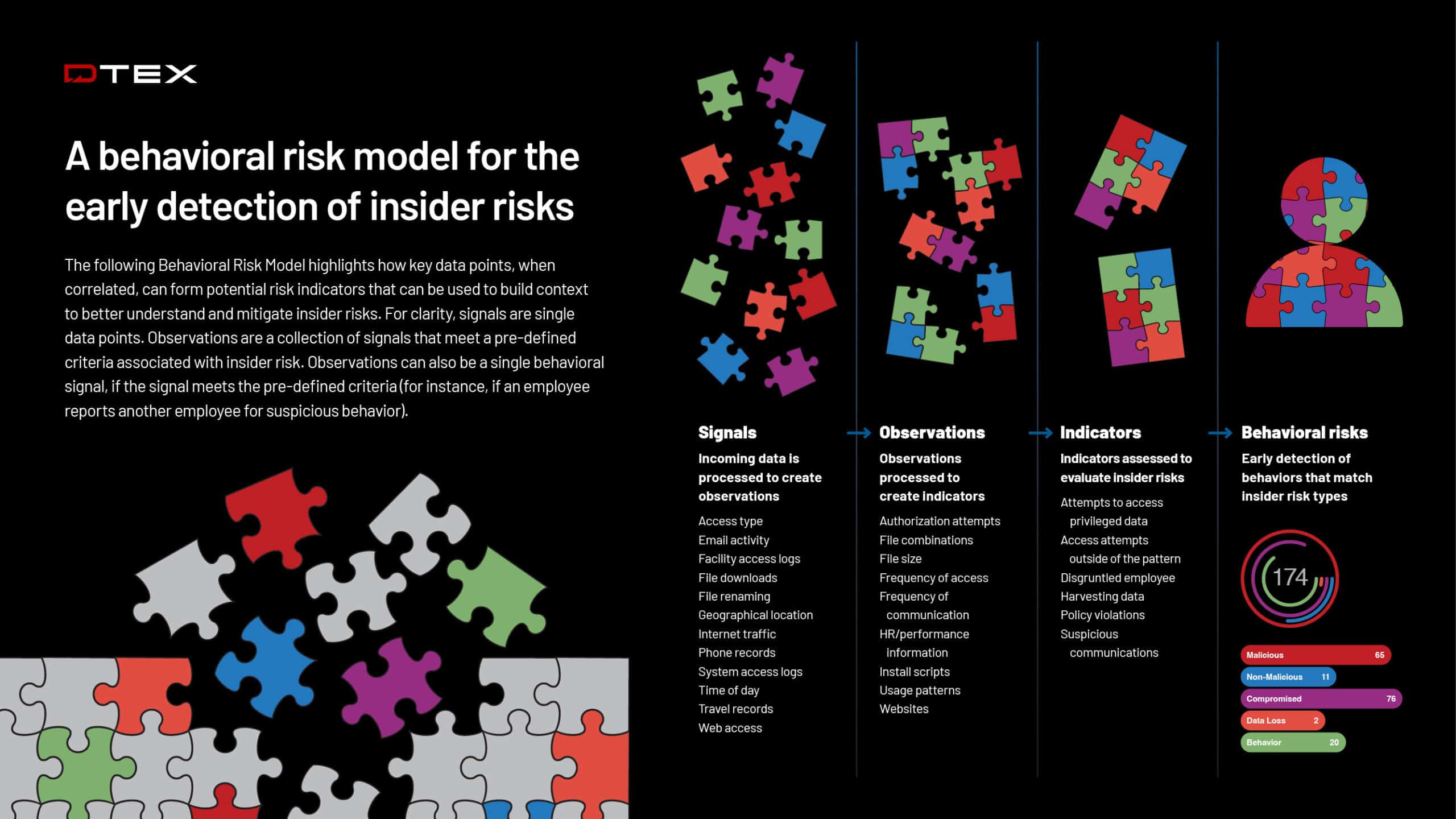
DTEX Behavioral Risk Model
A reference guide for a behavioral risk model for the early detection of insider risks.
Read More
2024 DTEX i3 Insider Risk Investigations Report Foreign Interference, Special Edition
Featuring critical insights for combating foreign interference plus behavioral indicators for malicious and super malicious insiders at every stage of…
Read More
Conversations from the Inside, Episode 7: The Evolving Role of UEBA in Insider Threat Prevention
GigaOm CTO Howard Holton and DTEX Systems Co-Founder and President Mohan Koo unpack the latest GigaOm Radar Report for UEBA,…
Read More
i³ Threat Advisory: Detecting the Use of Multiple Identities
The DTEX i³ Team has issued a new Insider Threat Advisory following recent investigations linking the use of multiple personal…
Read More
Proactive Insider Risk Management for the Public Sector
Proactive insider risk management for the public sector and federal agencies.
Read More
Conversations from the Inside, Episode 6: Dissecting the 4Ps of Insider Risk Management
DTEX CEO Marshall Heilman joins Christopher Burgess for a critical discussion on how organizations can shift the needle from reactive…
Read More
i³ Threat Advisory: Insecure Web Apps Creating High Risk for Insider Abuse
This Threat Advisory lists common web application categories prone to exploitation by malicious insiders.
Read More
i³ Threat Advisory: MSDT Exploit Detection, CVE-2022-30190
Based on the experience of the DTEX i³ team, old servers are either currently being used as file servers or…
Read More
i³ Threat Advisory: People's Republic of China - Volt Typhoon
iTA-23-03 highlights Volt Typhoon and the detection capability within DTEX InTERCEPT to uncover behaviors of users.
Read More
i³ Threat Advisory: MOVEit - CVE-2023-34362
DTEX advises customers to run the provided queries in this Threat Advisory within the DTEX InTERCEPT platform.
Read More