Detecting, Deterring, and Disrupting Foreign Interference
The DTEX i³ Team has issued a new Insider Threat Advisory with Potential Risk Indicators and behavioral insights for countering the threat of foreign interference and IP theft.

Zoom ‘Screen share and Control’: A Third-Party Security Risk
Mitigations for countering the third-party security risks associated with common video conferencing applications.
Mitigating Living off the Land Attacks, C2 Abuse with Insider Risk Monitoring
Featuring mitigations for malicious insiders that might weaponize trusted workspace applications to exfiltrate data and evade detection.
Detecting the Use of Multiple Identities
Breaking down the risks associated with the use of ChatGPT and other AI chat tools, plus steps for early detection and mitigation.
Insecure Web Apps Creating High Risk for Insider Abuse
This Threat Advisory lists common web application categories prone to exploitation by malicious insiders.
TOP INSIDER RISK RESOURCES
AS RECOMMENDED BY DTEX i³
-
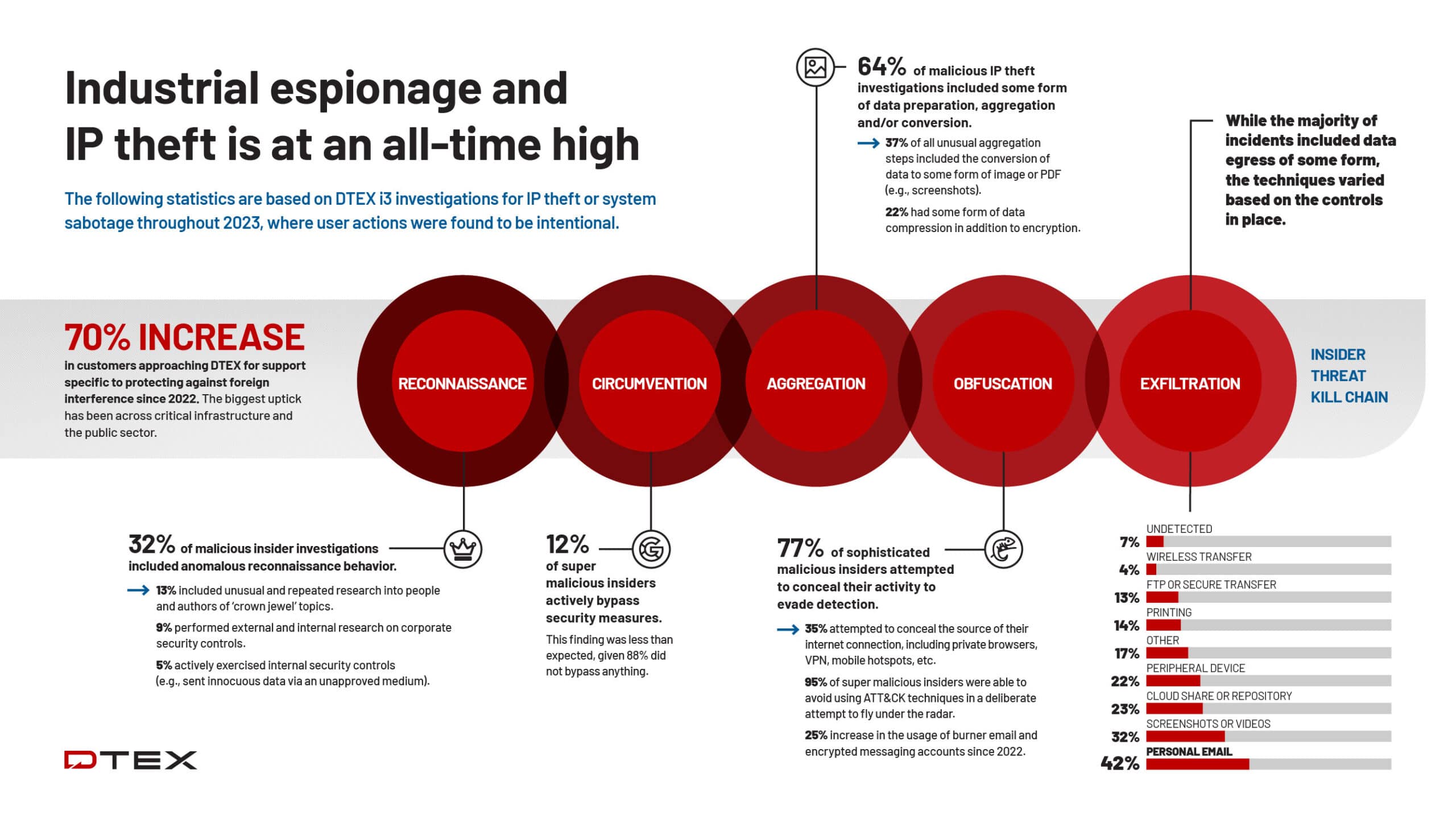
2024 Insider Risk Investigations Report - Foreign Interference: Special Edition
DTEX i³
-
Guiding Principles for Insider Threat
MITRE Corporation
-
Insider Threat Kill Chain: Behavioral Insights of Malicious and Super Malicious Insiders
DTEX i³
-
Insider Threat Toolkit
Center for Development of Security Excellence, Defense Counterintelligence and Security Agency
-
Behavioral Risk Model for Early Insider Risk Detection and Mitigation
DTEX i³
-
Insider Threat Program Maturity Framework
National Insider Threat Taskforce
-
2023 Cost of Insider Risks Global Report
Ponemon Institute and DTEX Systems
-
Common Sense Guide to Mitigating Insider Threats
Software Engineering Institute, Carnegie Mellon University
-
Insider Risk Mitigation Framework
National Protective Security Authority
-
Legal Considerations for Employee IT Monitoring
National Protective Security Authority
-
Insider Risk Mitigation Program Evaluation (IRMPE)
Cybersecurity and Infrastructure Security Agency
-
HR’s Role in Preventing Insider Threats
Cybersecurity and Infrastructure Security Agency
-
Insider Threat: The Theft of Intellectual Property in Windows 10
SANS Institute
-
Seven (Science-Based) Commandments for Understanding and Countering Insider Threats
Eric L. Lang
Conversations from the Inside
The go-to podcast for insider risk management, hosted by Christopher Burgess, brought to you by DTEX Systems. Follow our conversation on Spotify.
Actionable Insights and Assets
Popular Insider Risk Insights
About DTEX i³
Powering Next Generation
Insider Risk Management

DTEX i3 enables enterprise and federal entities to uplift their insider risk capability maturity to detect and prevent the most sophisticated insider risks from materializing into data loss events. The team offers a comprehensive set of insider risk services, including investigation support, insider risk assessments, emerging risk insights, reporting, and more. Download the i3 Solution Brief to view the full set of services.
To talk to a member of the i3 team about the latest research or early warning indicators, request a Threat Briefing.
Request a Threat BriefingOUT NOW ...
2024 Insider Risk Investigations Report
DTEX i³ has released its annual Insider Risk Investigations Report.
This year’s report reveals groundbreaking insights into the behavioral indicators of both malicious and super malicious insiders at every stage of the insider threat kill chain. The report also reveals the growing threat and complexity of foreign interference, and how to proactively mitigate risks associated with advanced social engineering against a backdrop of geopolitical tension and technological disruption.
Download your copy to stay one step ahead.
Download Report