In the race to detect insider threats before they escalate, speed is critical—but it’s only half the battle. The real game-changer isn’t artificial intelligence alone; it’s the quality of data that powers it. Insider risk detection is fundamentally a human challenge, requiring rich, contextual insights that go beyond cyber signals. More data isn’t always better—too much of the wrong data can erode trust and cloud judgment. Instead, high-fidelity signals spanning human, organizational, and cyber behaviors are key to early detection. By prioritizing quality over quantity, organizations can uncover real risks while minimizing noise and false positives.
Insider Risk Detection: Start with ‘Why’
In the context of insider risk management, early detection is the holy grail. Preceding risk management and exfiltration, it’s as far ‘left of boom’ as you can get and affords the benefit of time to course correct before an incident occurs.
Detecting insider risks early demands the understanding and acceptance that insider risk management is fundamentally a human challenge that cannot be addressed with a cyber-only solution.
This is why context is so important – and this starts with ‘Why’. In other words, risk analysts need to be able to understand why certain actions or behaviors deviate from a measured baseline, whether against their peer group or themselves.
Consider the following scenario. Three employees – User A, User B, and User C– upload the same file to Dropbox. A traditional Data Loss Prevention (DLP) tool might flag all three employees as insider risks, which might compel an analyst to take the same action against each employee. However, what the DLP tool fails to determine is why each user uploaded the file in the first place.
Say User A obfuscated the file and then went out of his way to conceal his behaviors before uploading the file to Dropbox. This tells a markedly different story to User B, who was simply trying to make a collaboration document accessible to the company’s marketing agency or User C, who fell asleep when her credentials were compromised by a threat actor trying to steal data.
With context, an analyst can determine a mitigation response that is proportionate to each risk; where heightened monitoring might be justified in User A’s case, security awareness training and tighter security controls might suffice for Users B and C.
A Behavioral Risk Model for Contextualizing Insider Risk
To build context, analysts must have access to data that spans human, organizational, cyber and physical sensors. The following Behavioral Risk Model (which is also available to download) highlights how key data points, when correlated, can form indicators (also known as Potential Risk Indicators) that can be used to build context to better understand insider risks.
For clarity, signals are single data points. Observations are a collection of signals that meet a pre-defined criteria associated with insider risk. Observations can also be a single behavioral signal, if the signal meets the pre-defined criteria (for instance, if an employee reports another employee for suspicious behavior).

DTEX DMAP+: Raising Contextual Awareness through Collection, Correlation and Analytics
DTEX builds on the Behavioral Risk Model with its patented DMAP+ Technology™, upon which its InTERCEPT™ platform is built. DMAP+ – which stands for Data, Machines, Applications and People – is an elastic metadata collection, correlation and analytics engine that captures and delivers a continuous audit trail of endpoint metadata (Enterprise Telemetry per the illustration below) that translates to 5000 signals per user per day.
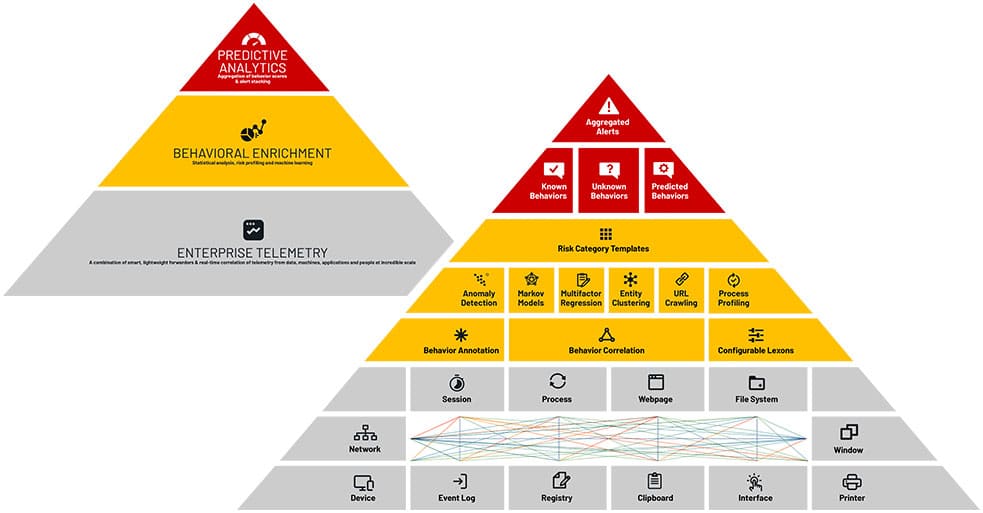
The metadata includes actions and activities of data, machines applications, and people (DMAP) on and off the network and is used to surface dynamic behavioral risk indicators.
Uniquely, DTEX does not rely on content inspection, instead, ensuring a privacy by design approach through its patented Pseudonymization technique which tokenizes personally identifiable information.
This is important because more data is not necessarily better for improving early insider risk detection. In fact, capturing more data at the expense of employee privacy can have a counter effect, introducing risk by eroding trust and breaking bidirectional loyalty. In addition, too much of the wrong data has the potential to impact genuine investigations by diverting an analysts’ attention to risks that don’t exist.
What matters is the quality of data and the extent to which it can be used to inform decision making.
Only by having the right high-fidelity signals and observations can analysts gain context to detect insider risks against false positives and insider threats that might otherwise slip through the cracks.
Ai3: Accelerating Insider Risk Detection with Context-Rich Insights
Ai3 is DTEX’s dedicated AI insider risk assistant designed specifically for insider risk management, providing analysts with deeper behavioral insights to enhance detection and decision-making. Rather than simply automating tasks, Ai3 democratizes complex data analysis, helping security teams identify meaningful patterns and anomalies that could indicate potential risks.
What sets Ai3 apart is its foundation—high-quality, enriched data. By analyzing behavioral baselines and deviations across human, organizational, and cyber activity, Ai3 provides the critical context needed to differentiate between normal activity and genuine threats. This ensures that analysts focus on real risks rather than false positives, improving detection accuracy while maintaining employee trust.
Case in Point: Bringing Context to Malicious Insiders
Where DTEX InTERCEPT brings contextual awareness to data, Ai3 provides the simplicity and speed to detect and resolve insider risk investigations in a matter of minutes.
The following case study demonstrates how an analyst might leverage DTEX Ai3 Risk Assistant in InTERCEPT to guide and fast-track an investigation.
Step 1: Answering ‘Who’
The analyst starts by asking: “Who are the riskiest malicious users in my organization.” Based on the data available, Ai3 surfaces the top malicious users, highlighting the number of malicious activities per user as well as their most recent risk score.
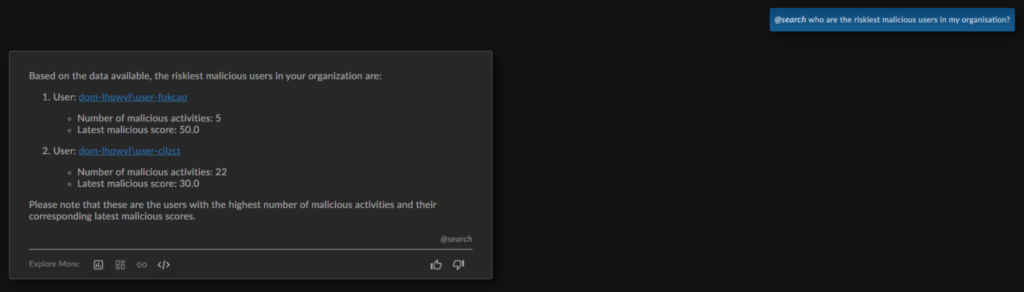
Step 2: Answering ‘Why’
The analyst wants to know why the top user has the score they do, so asks “Why is user dom-lhqwyl\user-fpkcao risky?”
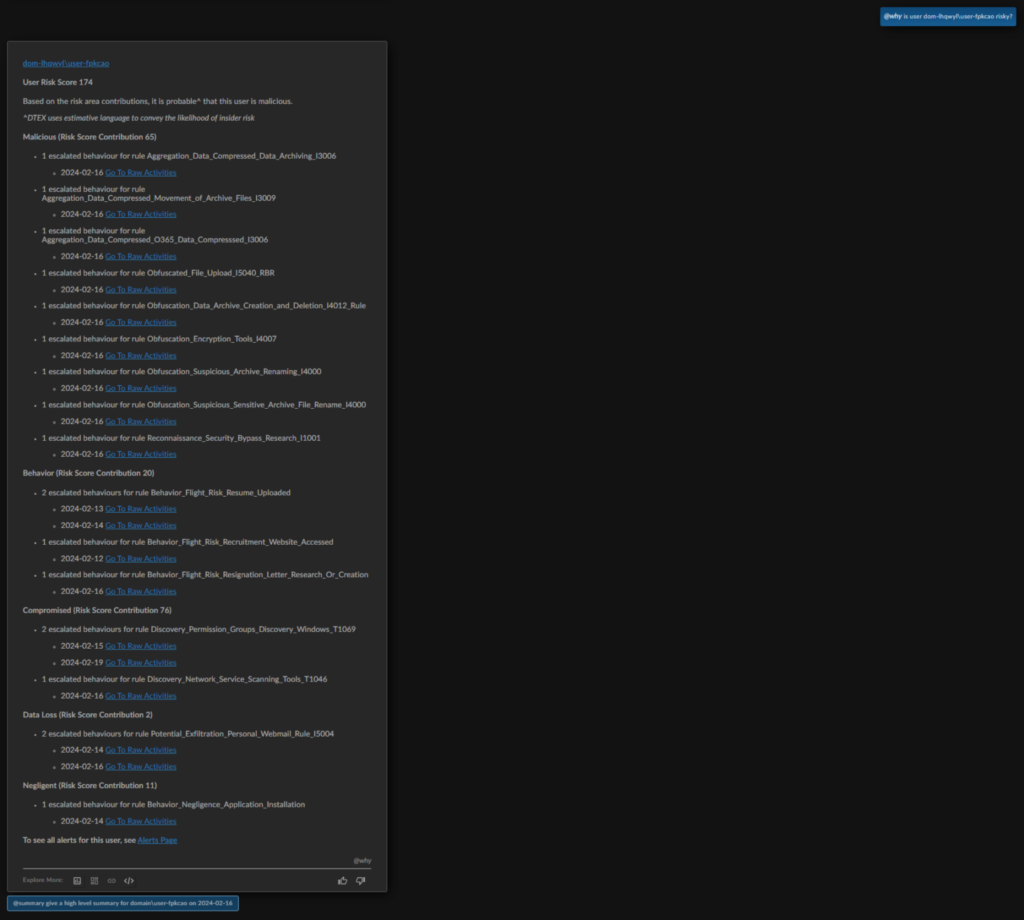
Ai3 surfaces critical insights into the malicious user, including the assessment that “it’s probable^ that this user is malicious” based on the combination of risk score contributions from the behavioral categories. From this summary, the analyst can see that all the malicious activity occurs on February 16, indicating that this was a concentrated event encompassing a lot of concerning behaviors.
Luckily, Ai3 has already selected that date as a potential interest for the analyst to run an “@summary” analysis to summarize the annotated activities on that date. By clicking on Ai3’s suggested prompt, the analyst can see a high-level summary for the activities of interest.
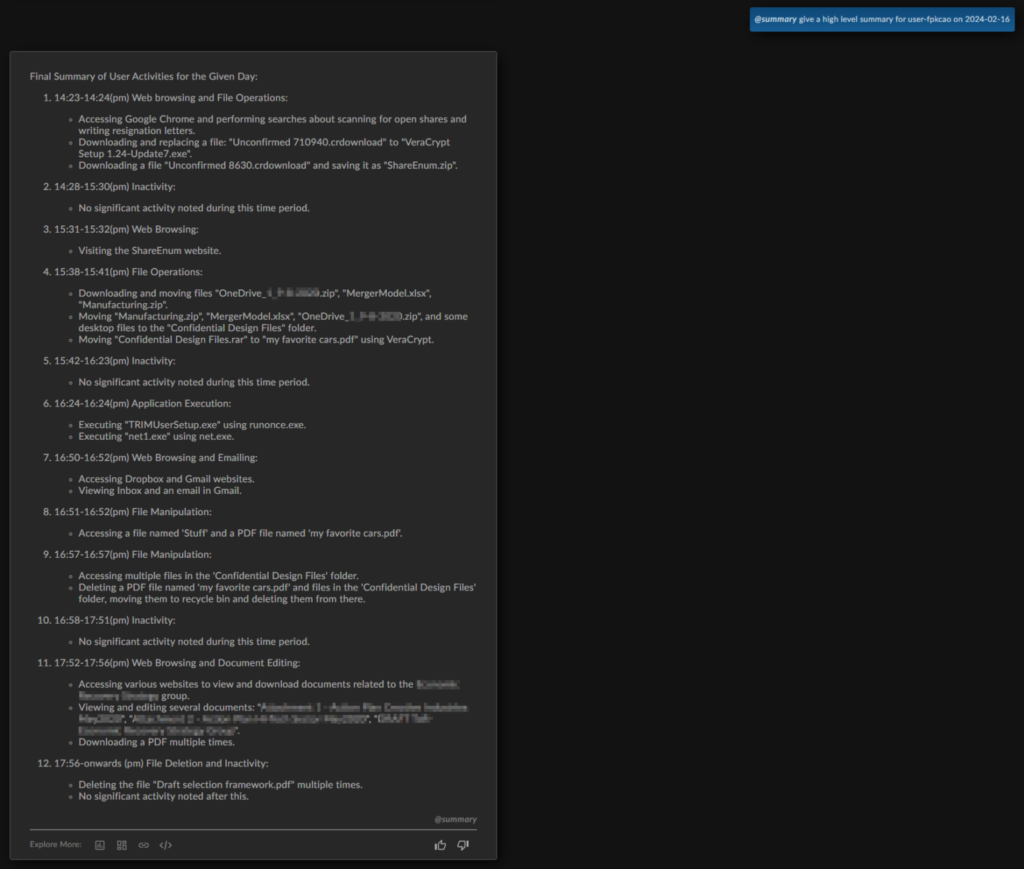
The summary shows that the user centralized a collection of important files into a “Confidential Design Files” folder that they then used VeraCrypt to encrypt into “my favorite cars.pdf”. The analyst can see that this is highly suspicious behavior indicative of a user trying to obfuscate the contents and nature of these files.
Step 3: Answering ‘What’
Now that a degree of intent has been established, the analyst wants to investigate potential exfiltration, so types: “@search show me all the exfiltration events for user dom-lhqwyl\user-fpkcao.”
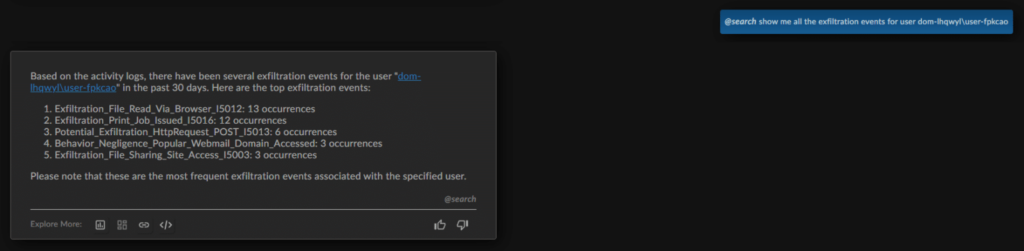
Ai3 brings up the count of annotated activities per tag. From here, the analyst can pivot into the user’s timeline to see the high-level sequences of escalated behaviors for further context.
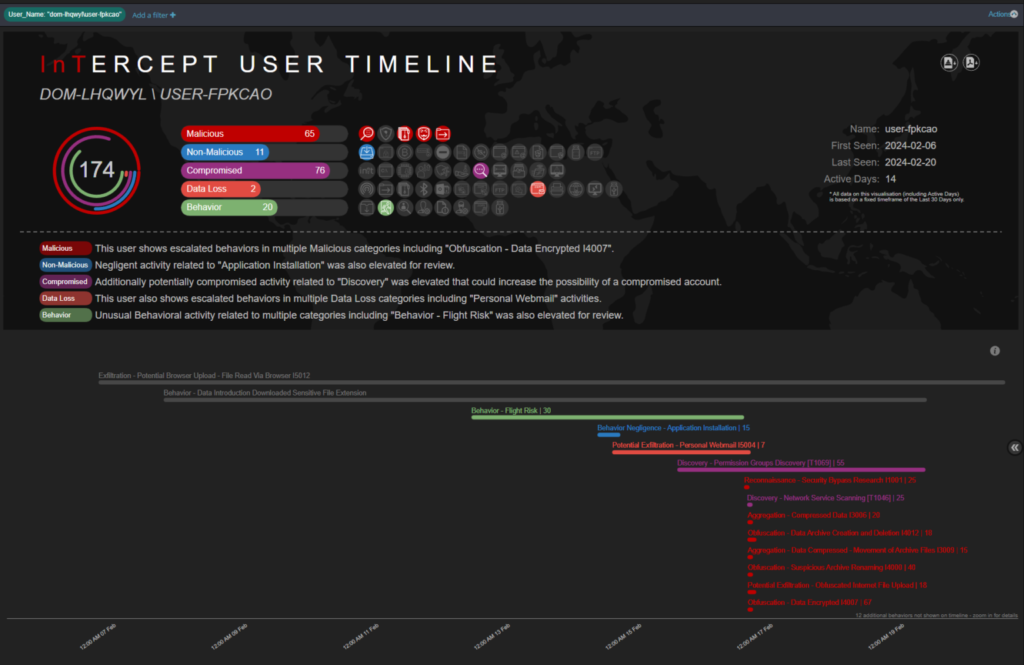
The analyst can also drop into the raw activities for the exfiltration events. Here, the analyst can see that the “my favorite cars.pdf” was uploaded via Chrome, which confirms exfiltration has occurred. The investigation needs to be escalated.
The analyst can go a step further by downloading the raw activities with the fields they need to compile evidence for further investigation.
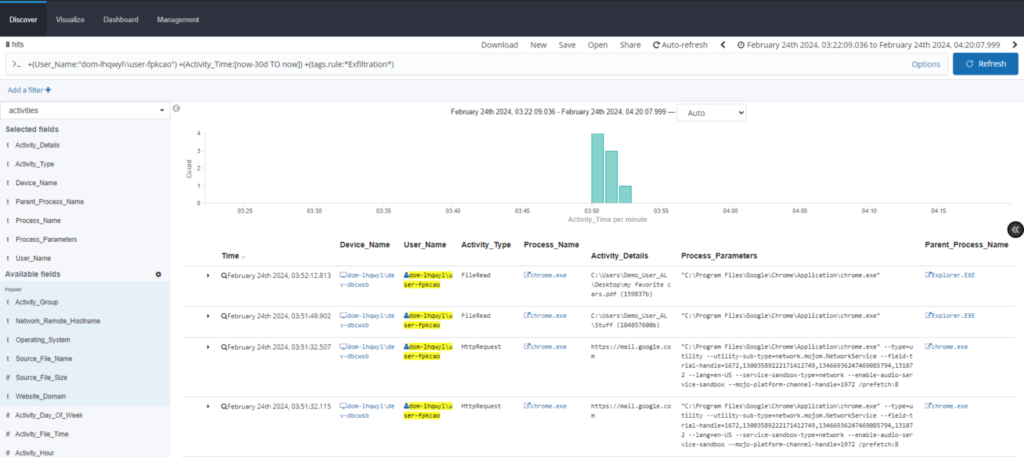
From here, the analyst will want to understand where in Chrome the file was uploaded, and what other users have interacted with the encrypted files. This will shed more context on the situation and how best to manage risk.
DTEX Ai3 Cuts to the Chase
The above case study demonstrates how Ai3 democratizes complex behavioral data analysis. By knowing what questions to ask at the right time, Ai3 helps guide analysts to the information they need, when they need it, bypassing complex data wrangling that takes away from the mission at hand.
“What sets Ai³ apart isn’t artificial intelligence, but the data science upon which it is built. DTEX’s innovative approach to data collection, underscored by behavioral enrichment, means sophisticated insider risks no longer fall through the cracks,” DTEX Systems CEO Marshall Heilman.
DTEX enables enterprise and federal entities to detect and prevent the most sophisticated insider risks from materializing into data breaches. Request a demo to understand how InTERCEPT and Ai3 work in synergy to identify early warning indicators and accelerate insider investigations.
Topics
Subscribe today to stay informed and get regular updates from DTEX Systems






