WORKFORCE CYBER
INTELLLIGENCE
RESOURCES
A Human-Centric Approach to Operational Awareness and Risk Management

THE LATEST ON WORKFORCE CYBER INTELLIGENCE

Insider Risk Management and the Department of of Defense Zero Trust Strategy Guide
Aligned with the Department of Defense’s (DoD) strategic goals to achieve its vision for Zero Trust through culture, adoption, and…
Read More
DTEX Guide to Generative AI
The possibilities with AI are endless, but so are the security risks. Update your data protection strategies today.
Read More
Proactive Insider Risk Management for the Public Sector
The National Insider Threat Task Force and Directive 504 from the Committee on National Security Systems (CNSSD 504) prescribes minimum…
Read More
Bridging Zero Trust and Insider Risk Management: A Critical Journey for Federal Security
As federal agencies adhere to the Zero Trust (ZT) mandate, the incorporation of Insider Risk Management (IRM) within its framework…
Read More
The Insider Risk Guide to AI
The possibilities with AI are endless, but so are the security risks. It won’t just be cybercriminals and nation-states looking…
Read More
Conversations From the Inside, Episode 9: Navigating the Convergence of Insider and External Threats in Government
Amid rising geopolitical conflicts and advanced technological disruptions, the lines between internal and external security threats are increasingly converging. Join…
Watch Now
DTEX Data Privacy and Protection
DTEX helps hundreds of organizations worldwide better understand their workforce, make effective security investments, and comply with regulatory requirements while…
Read More
Transform Cyber Defense Operations Through Proactive Insider Risk Management
DTEX and Mandiant have partnered to meet the increasing demand for insider risk management (IRM) solutions. Together, DTEX and Mandiant…
Read More
Conversations from the Inside, Episode 8: 2024 Insider Risk Investigations Report, The Rise of Foreign Interference
DTEX’s frontline investigators Rajan Koo, Armaan Mahbod and Lynsey Wolf join host Christopher Burgess to unpack the latest findings. Whether…
Read More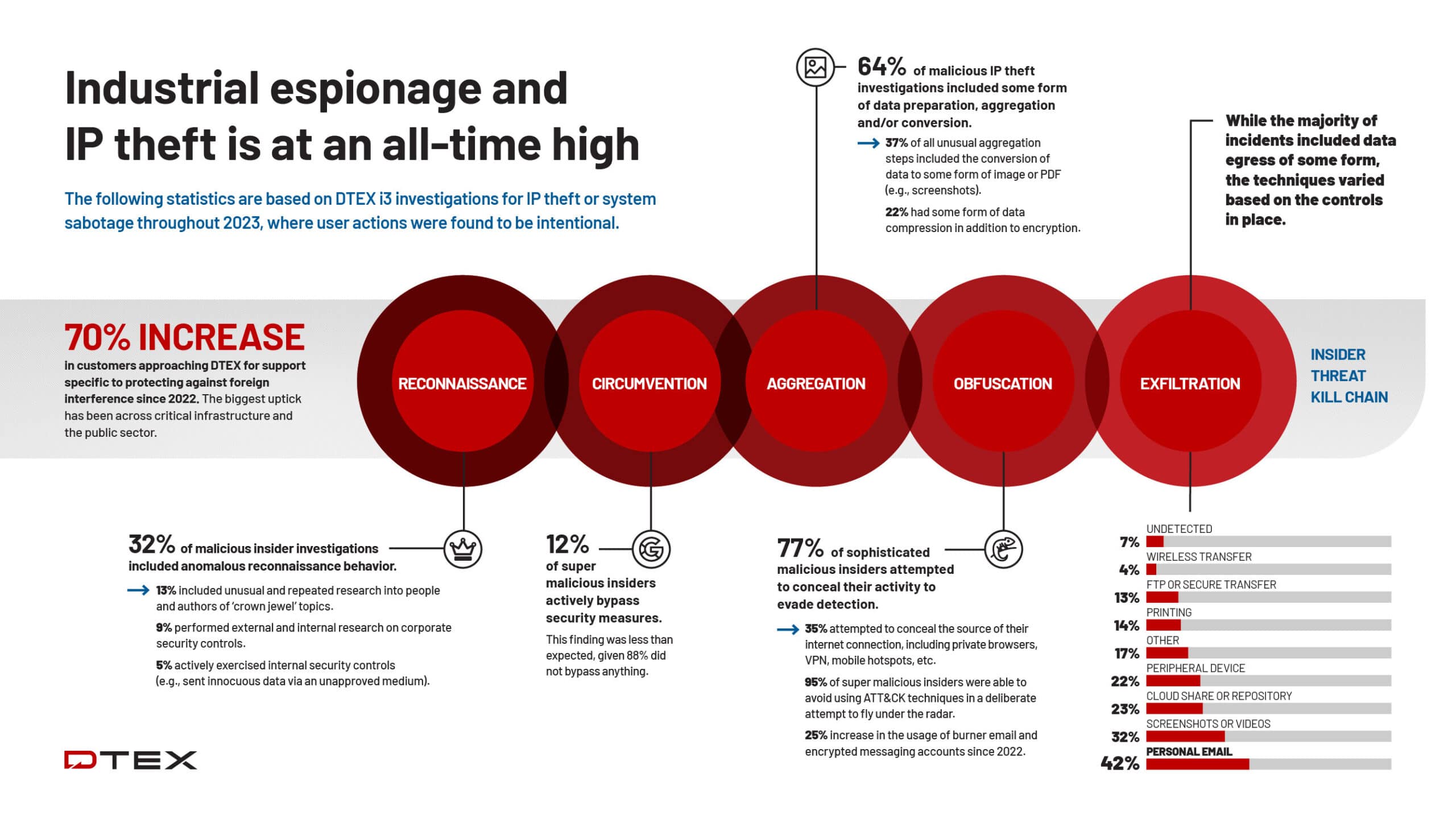
DTEX Insider Threat Kill Chain: Behavioral Insights of Malicious Insiders
The following statistics are based on DTEX i3 investigations for IP theft or system sabotage throughout 2023, where user actions…
Read More
DTEX Behavioral Risk Model
A reference guide for a behavioral risk model for the early detection of insider risks.
Read More
2024 DTEX i3 Insider Risk Investigations Report Foreign Interference, Special Edition
Featuring critical insights for combating foreign interference plus behavioral indicators for malicious and super malicious insiders at every stage of…
Read More