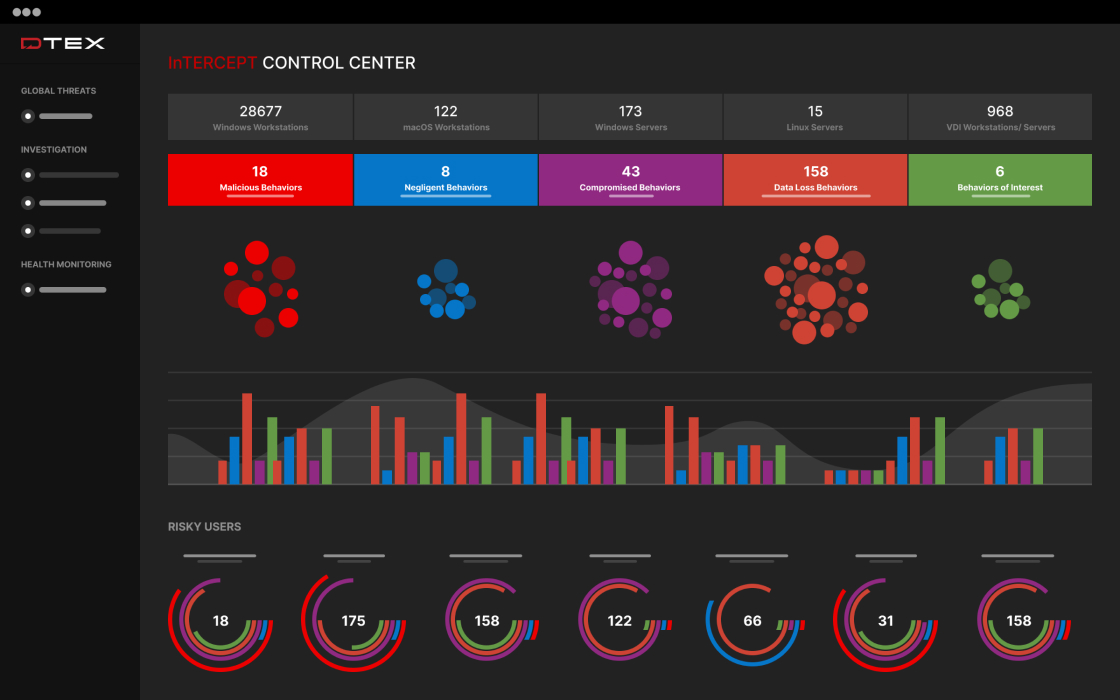
Simplify your security stack with one insider risk management platform powered by AI
DTEX InTERCEPT integrates the best of DLP, UEBA, and UAM, addressing the limitations of these tools individually.
Purpose-built for insider risk management, DTEX InTERCEPT offers powerful data insights and early warning indicators to detect and mitigate threats before incidents occur.
Get ahead of threats with an AI driven solution to insider risk
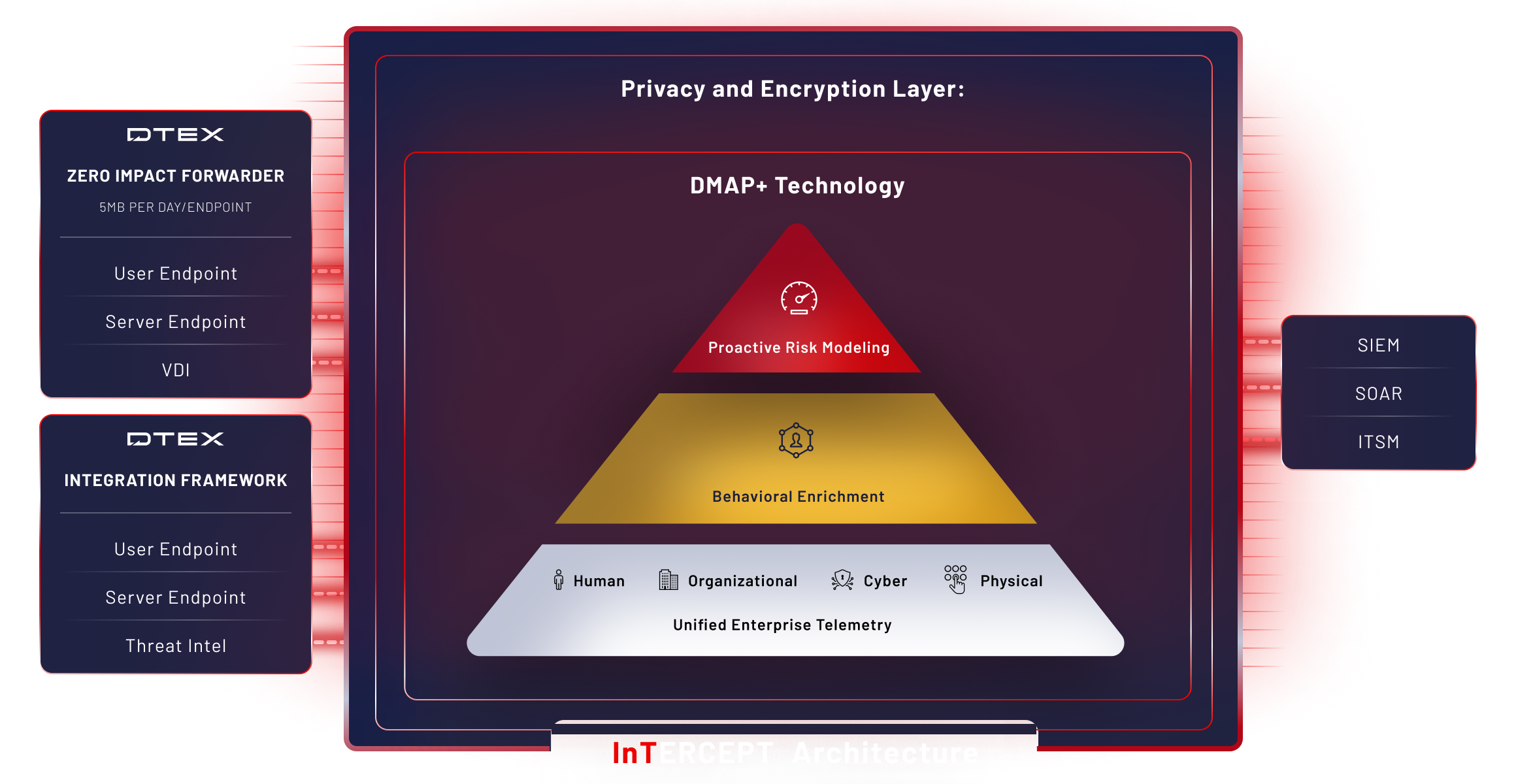
Zero impact to endpoints at enterprise scale
Zero impact to endpoints at enterprise scale
Lightweight DTEX forwarder collects only <5MB per endpoint per day, enabling InTERCEPT to scale to over half a million endpoints in a single implementation.
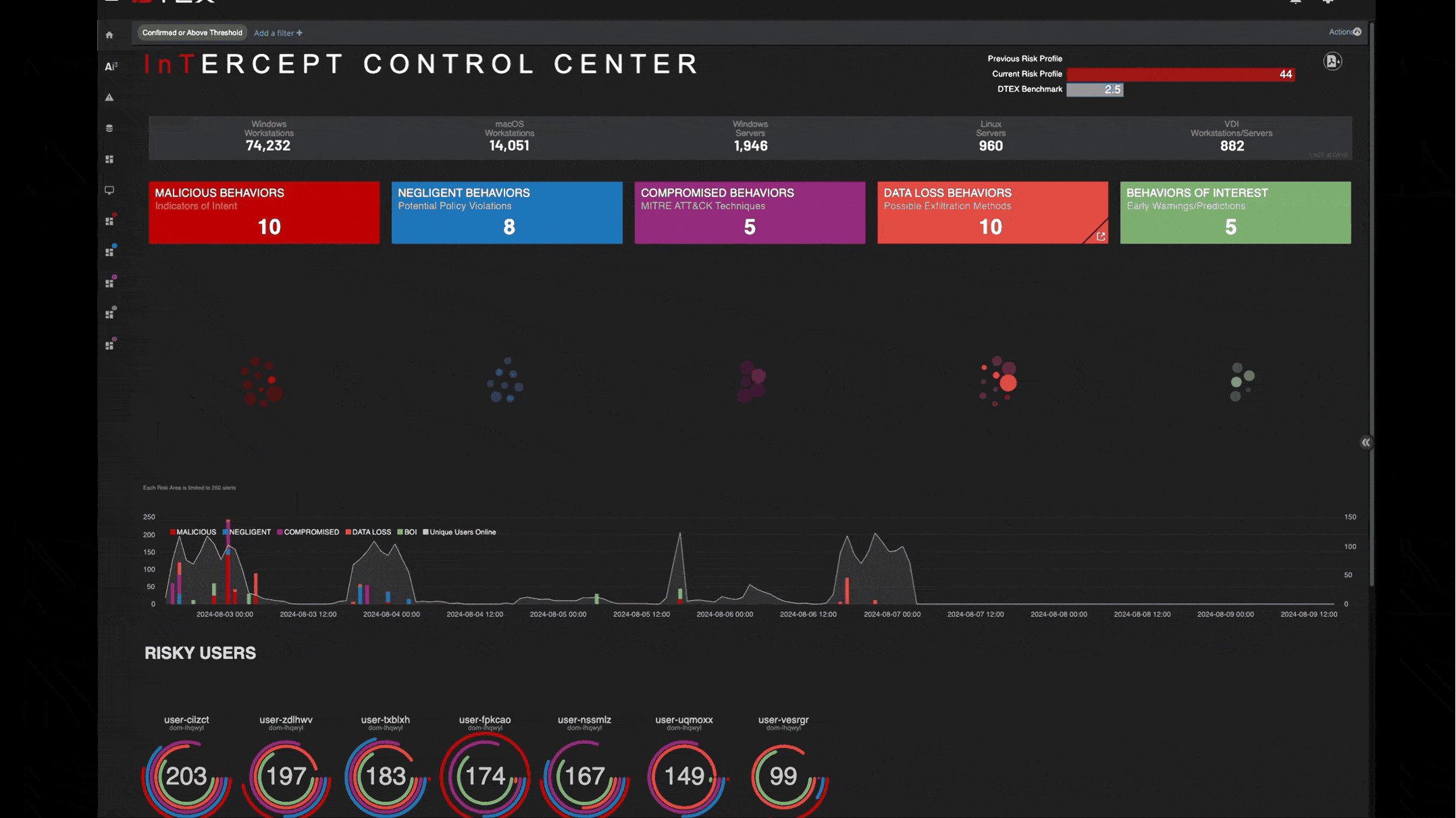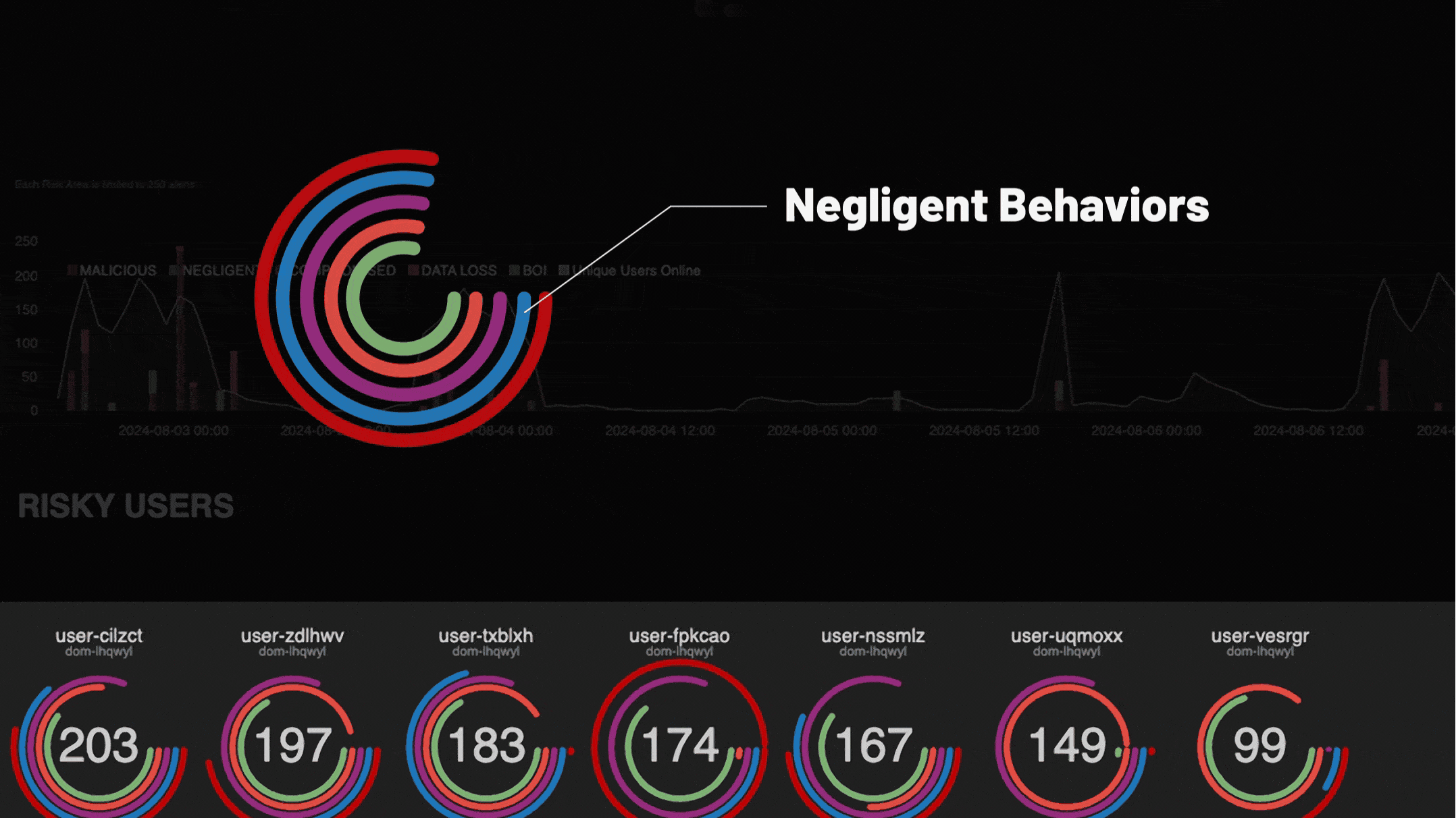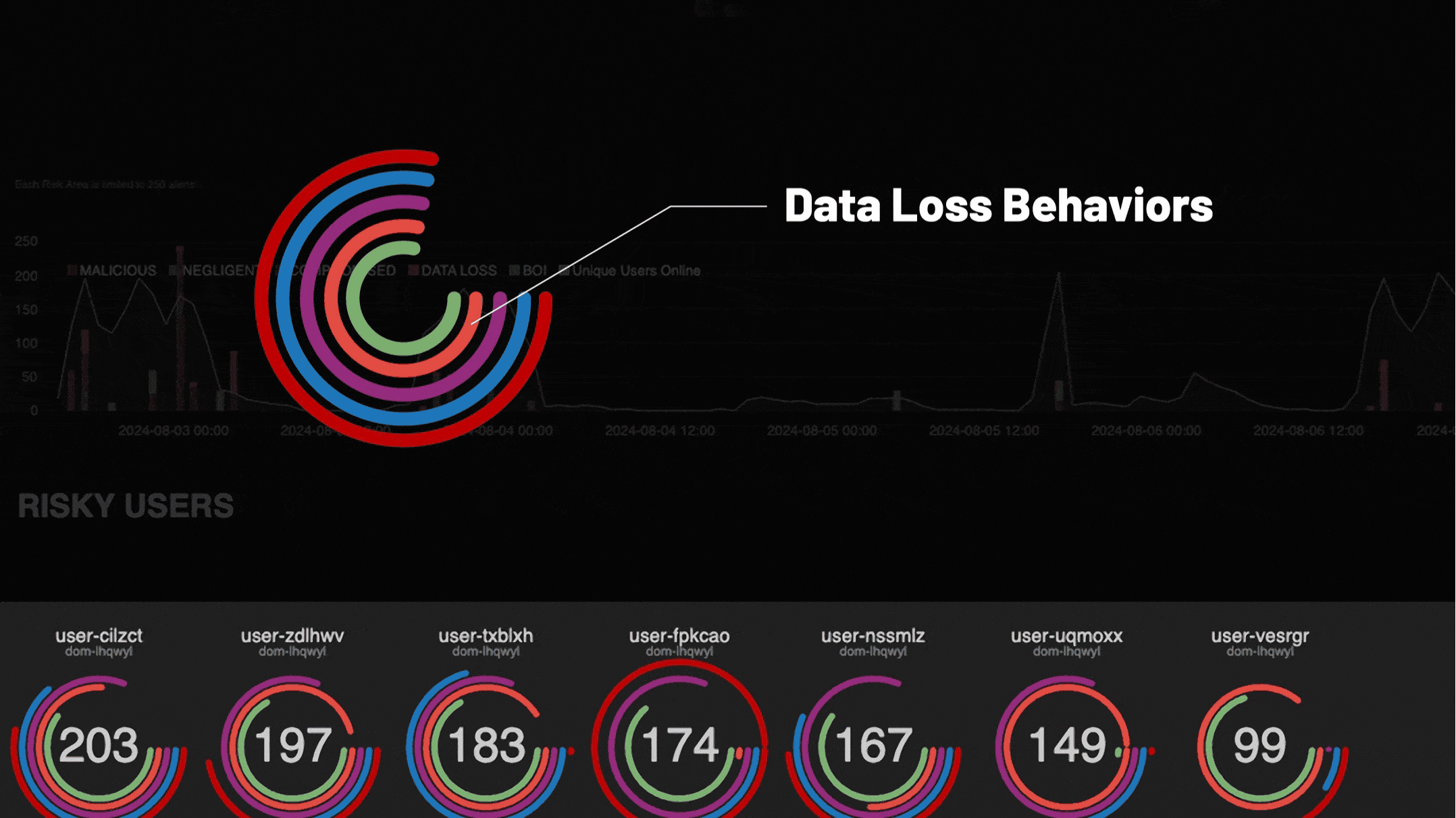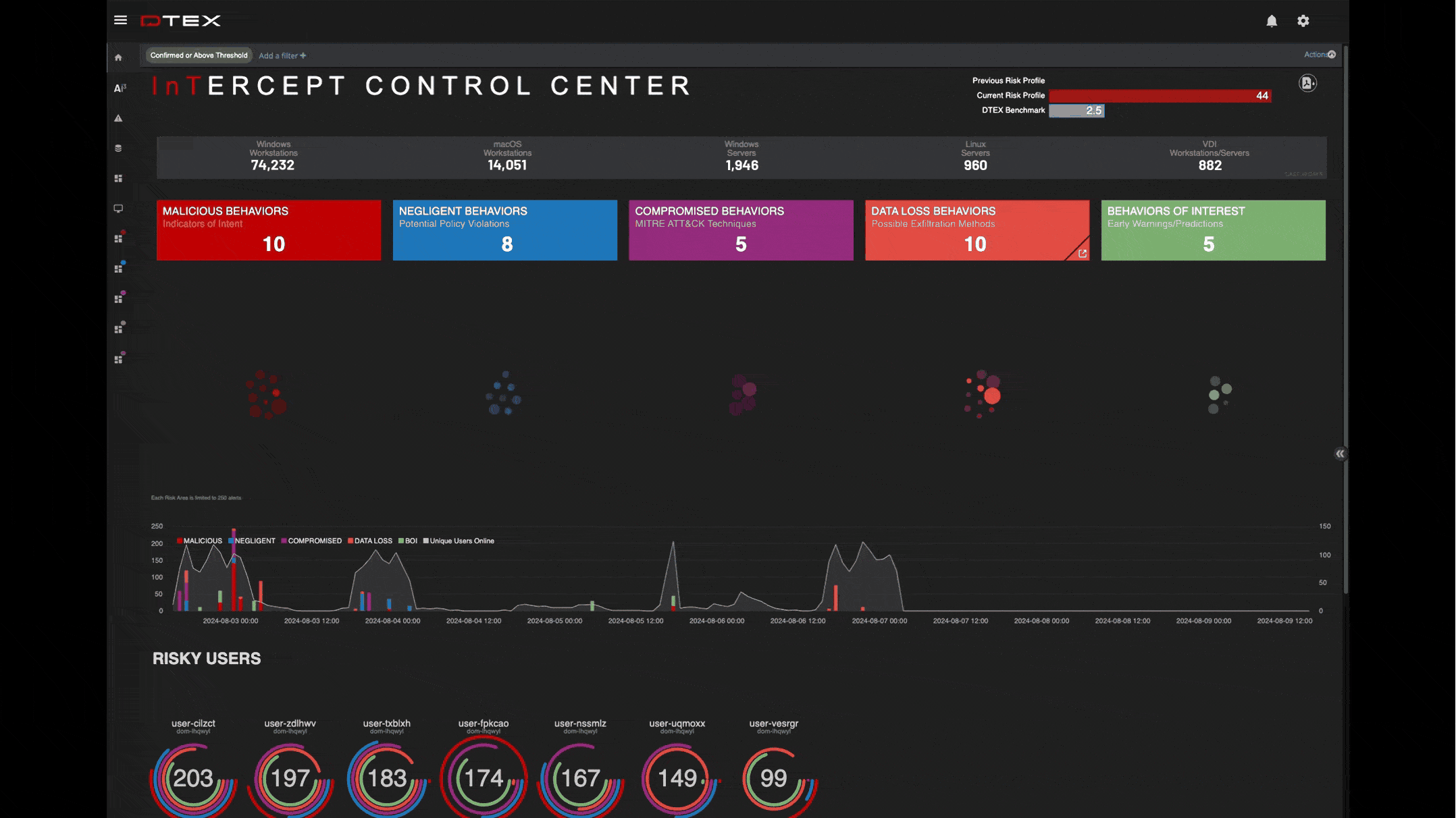
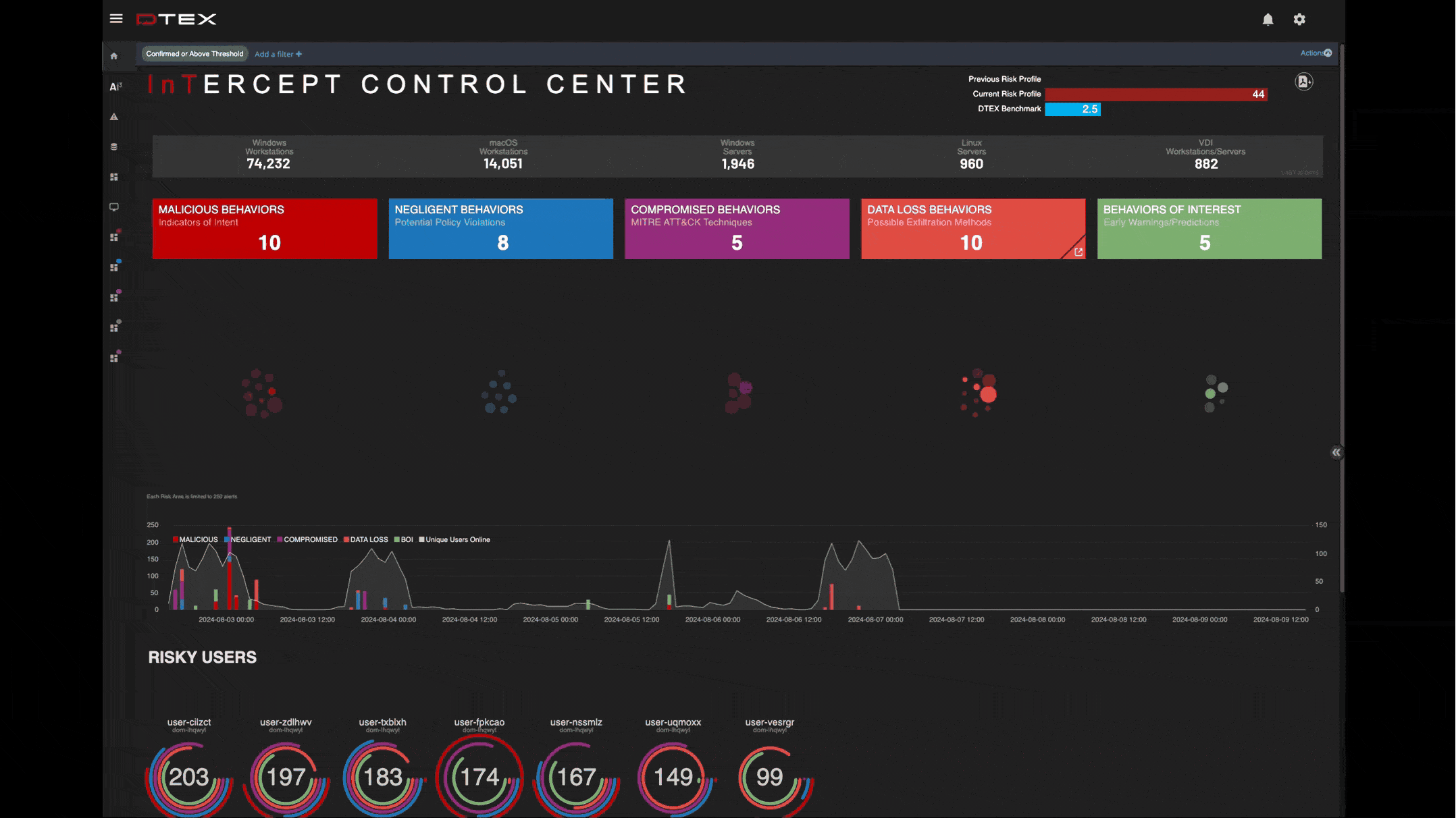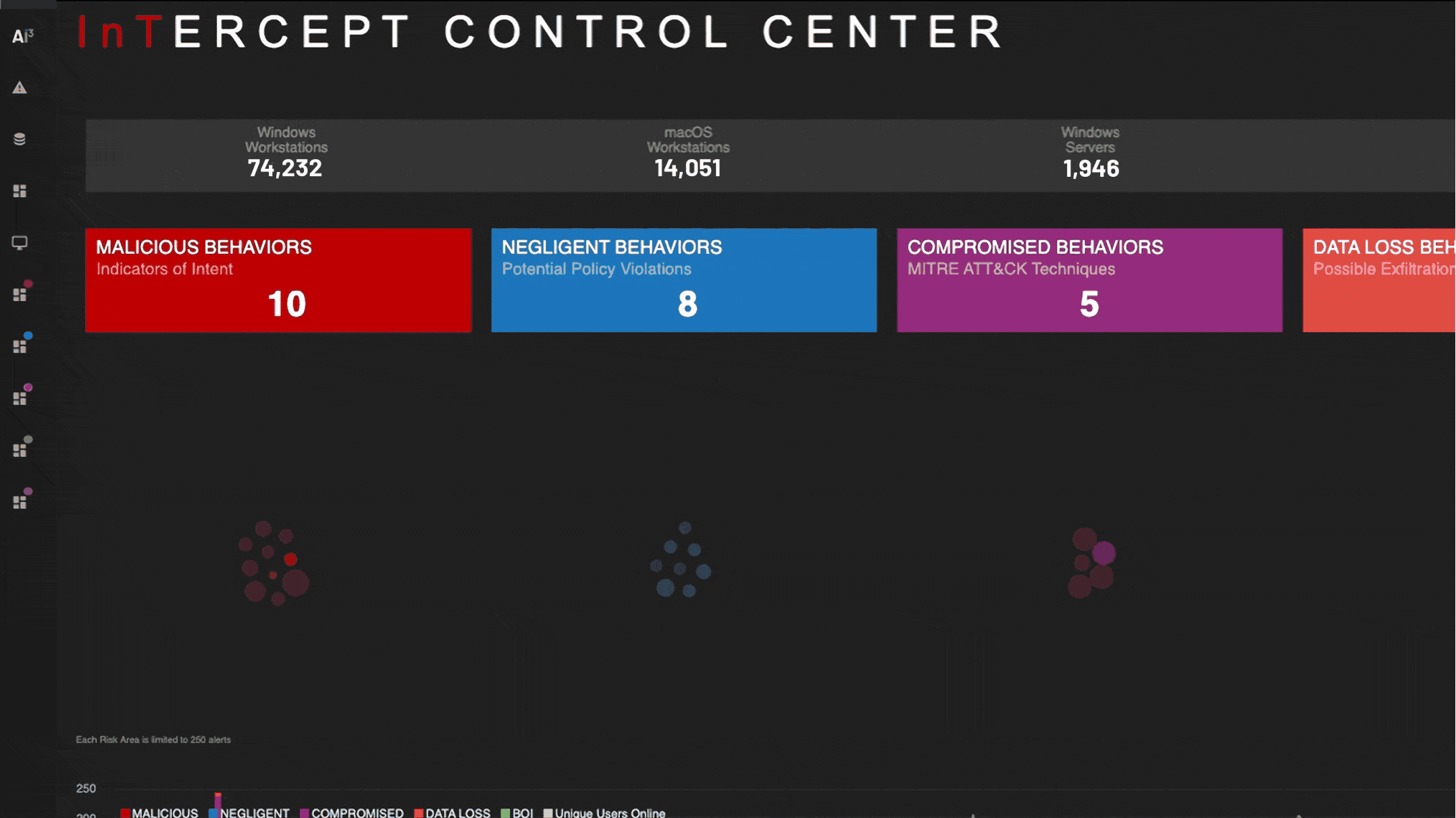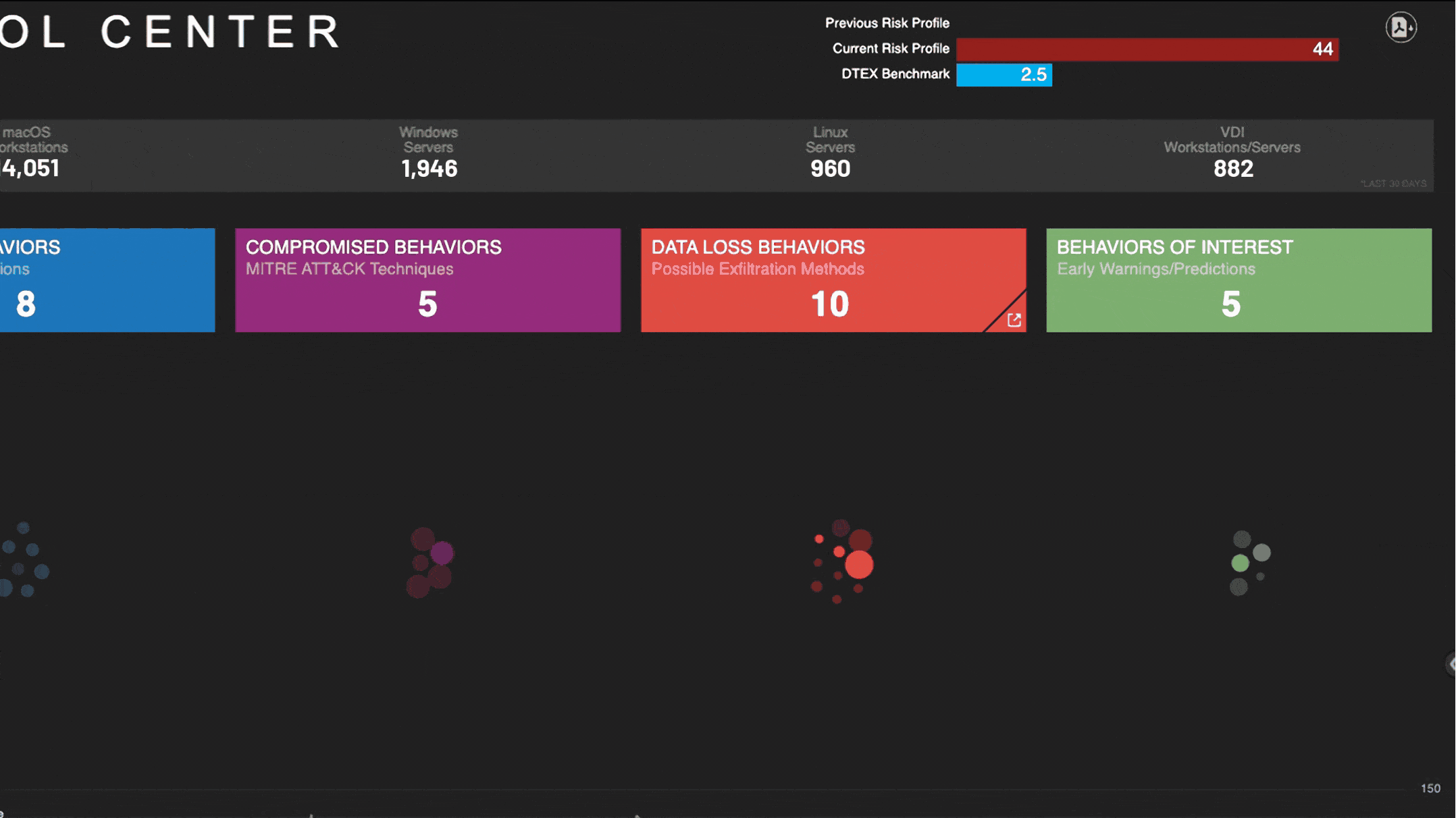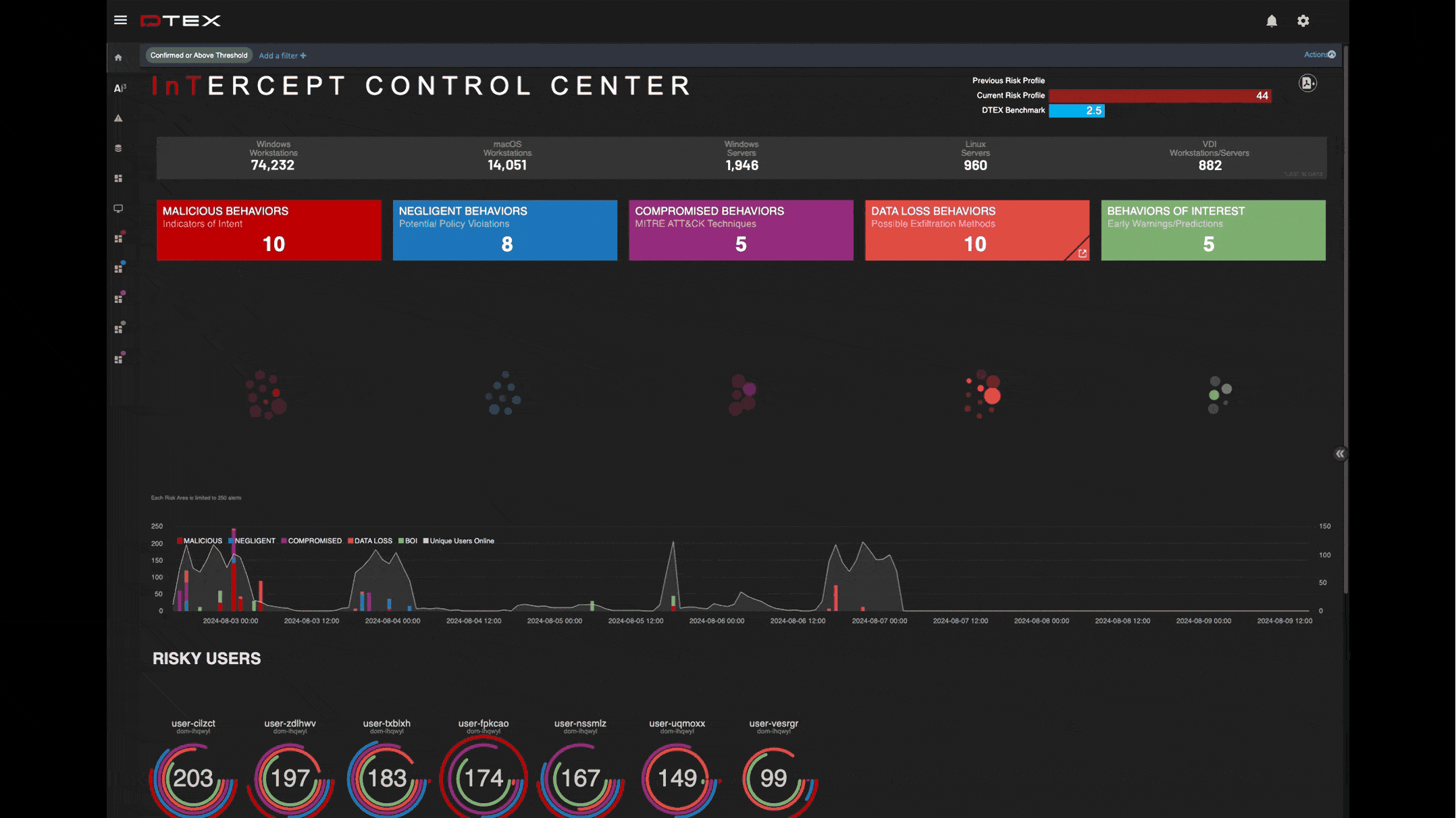
Early warnings of suspicious events
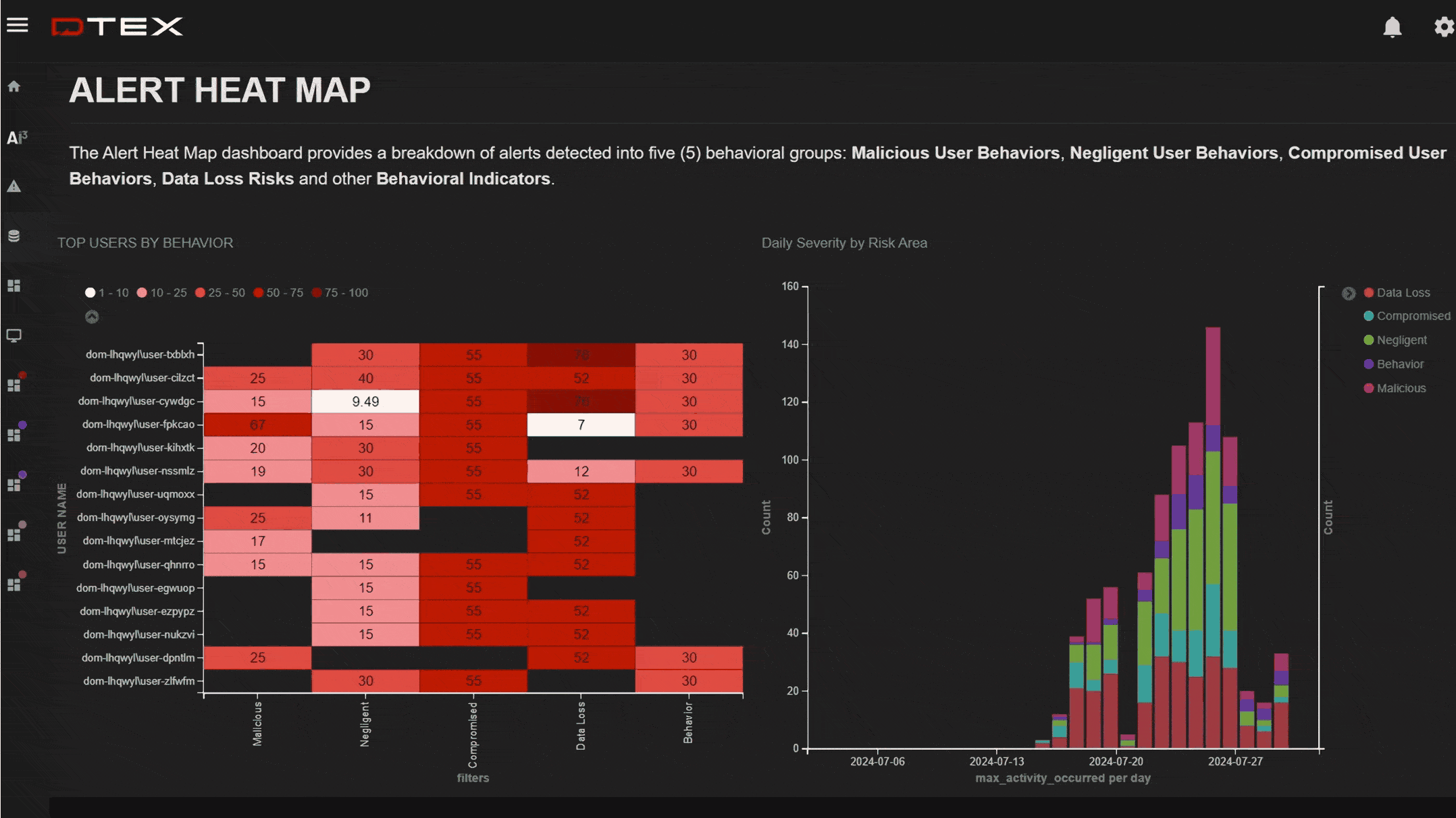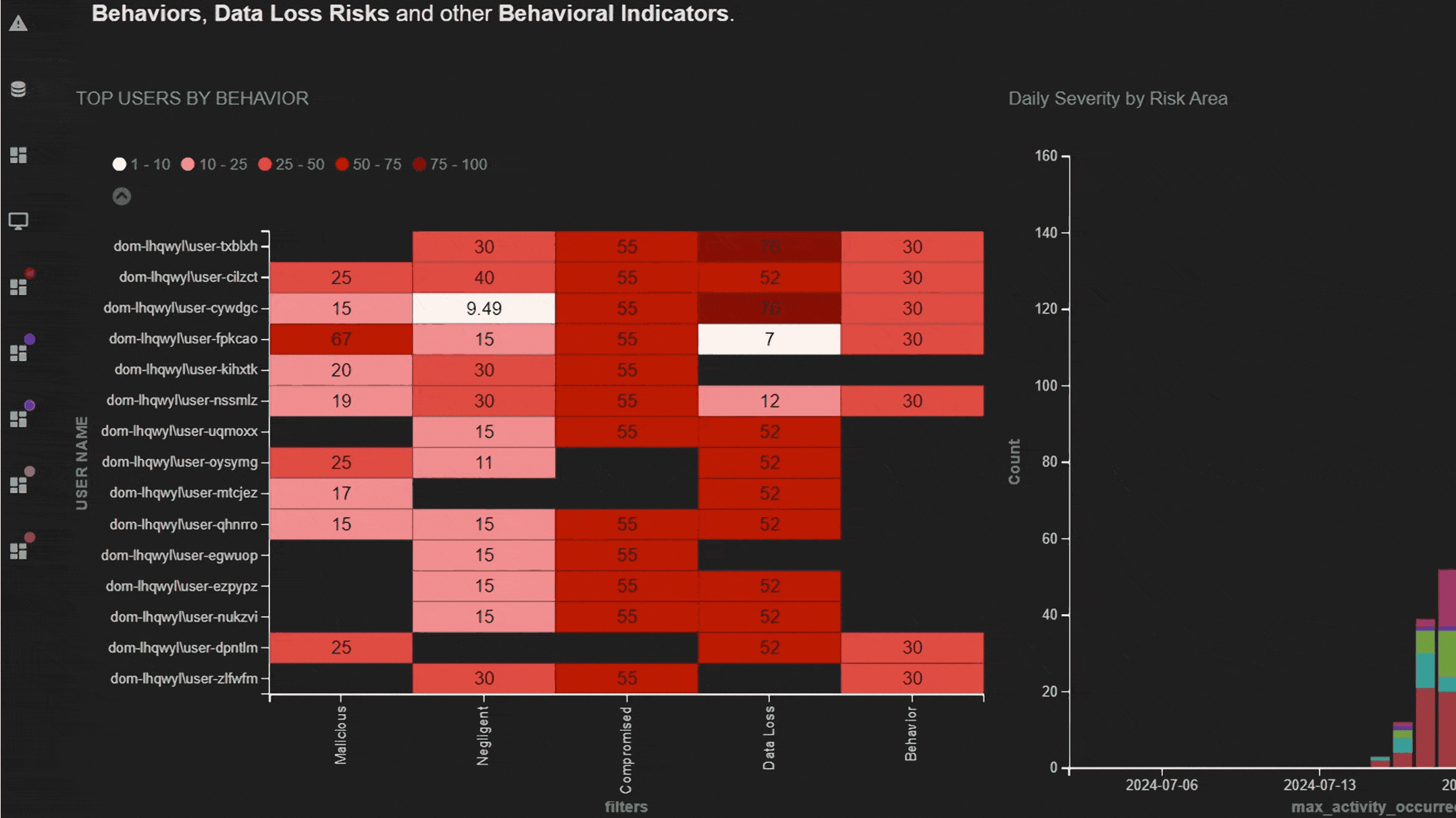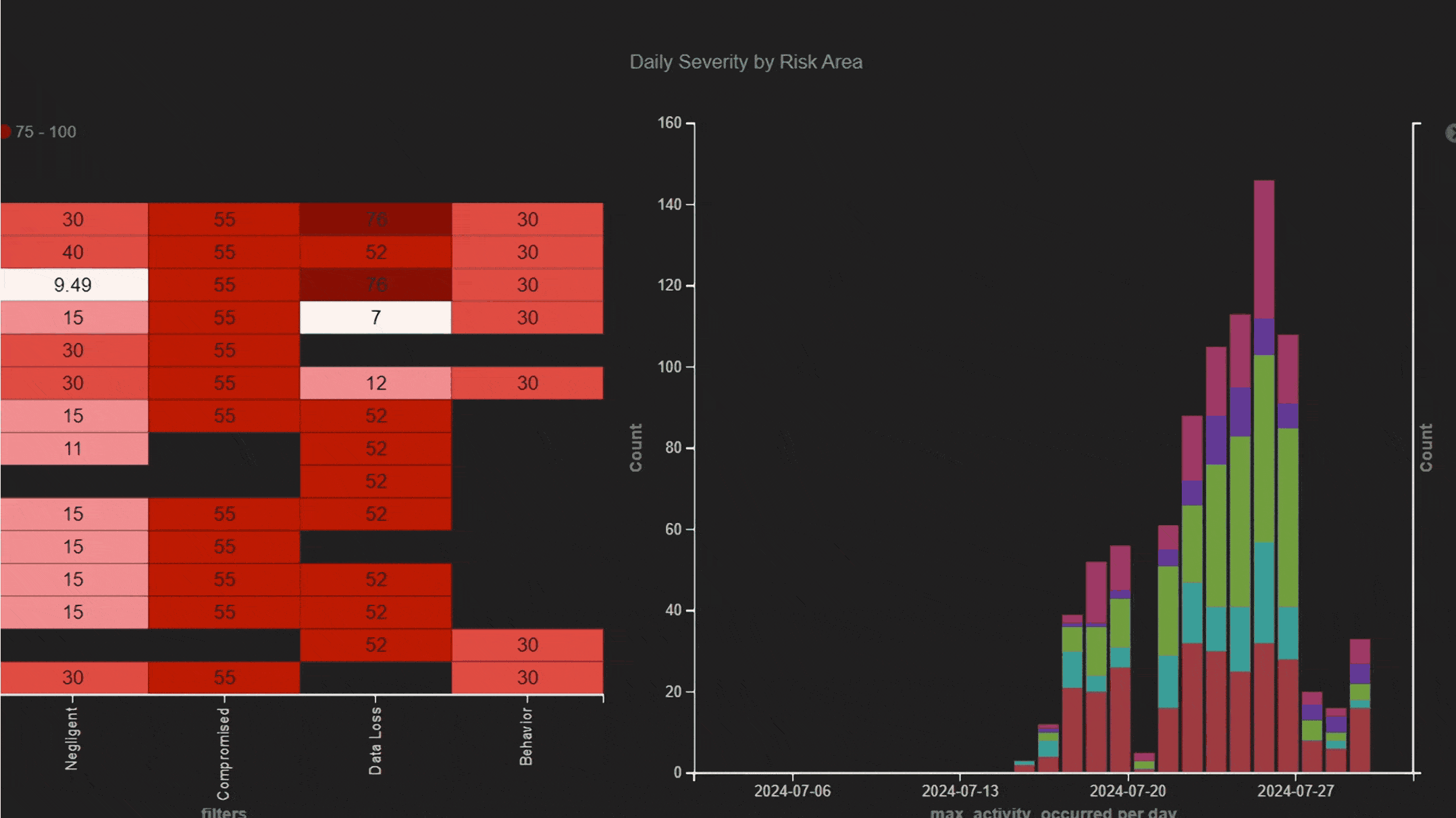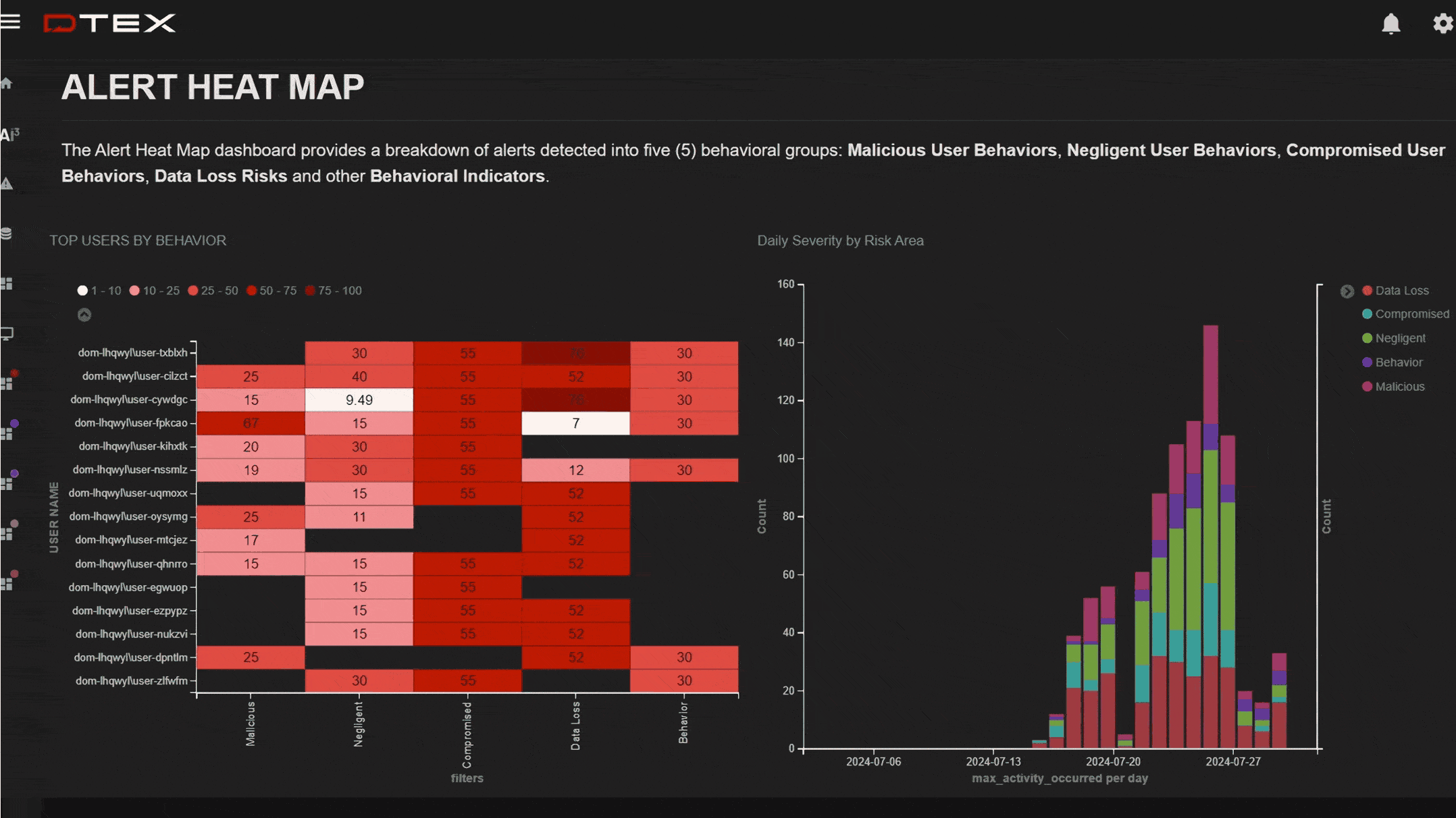
Early warnings of suspicious events
Get ahead of suspicious activity with elevated indicators of intent before a data breach can occur.
Fast, AI-guided insider investigations
Fast, AI-guided insider investigations
Lean on AI-guided investigations that drive pointed questions about sensitive data, who is accessing it, and most importantly, why.
A trusted partner during an insider incident

A trusted partner during an insider incident
Rely on our elite team of i3 insider threat investigators for support during an insider incident.
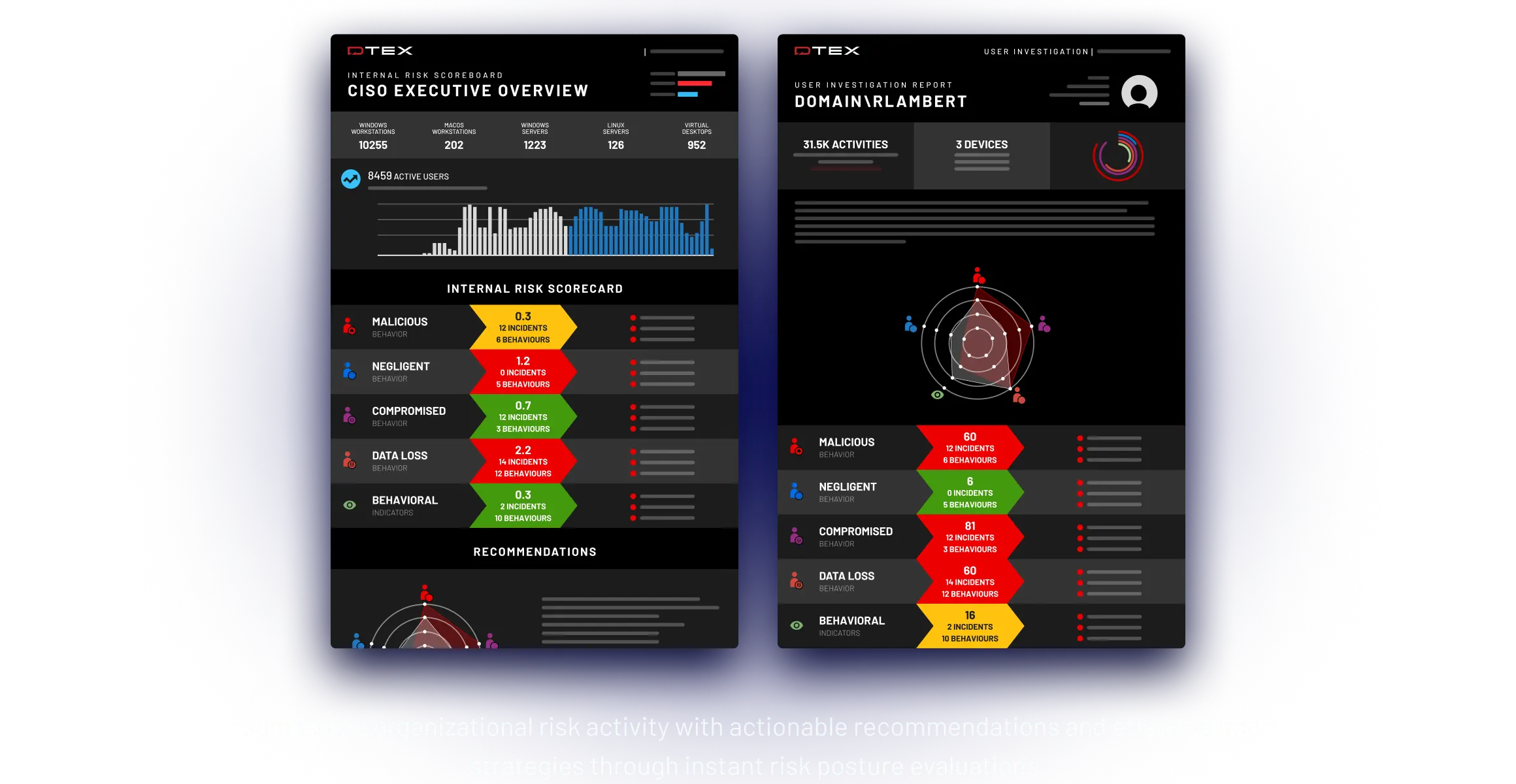
Simple, one-click role-based reporting
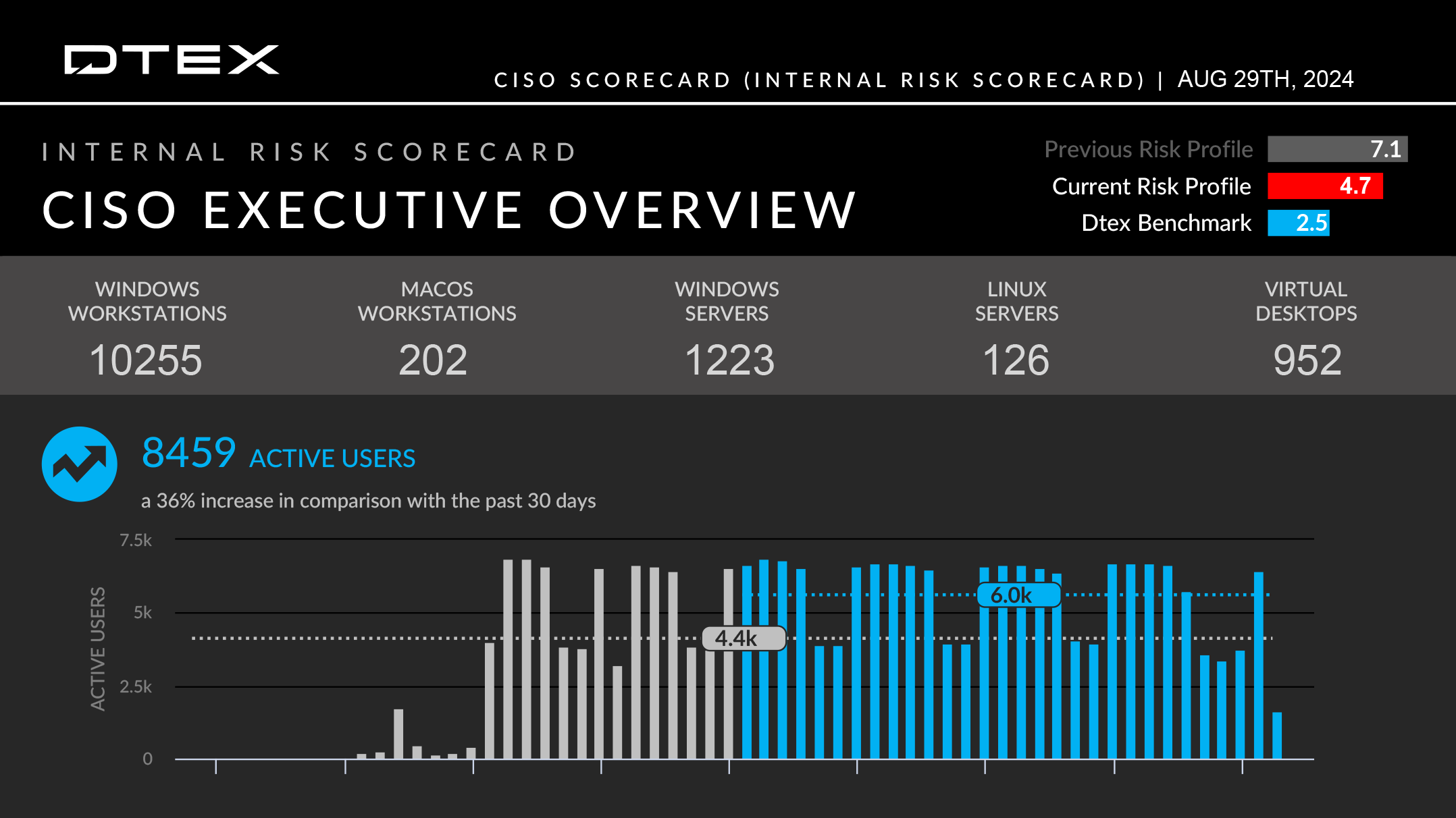
Simple, 1-click role-based reporting
Instantly access a wide range of reports that summarize organizational risk with actionable recommendations for continuous optimization.
An integrated platform to prevent insider incidents, while optimizing security and user privacy
Combining the best of DLP, UEBA, and UAM into a powerful AI-driven platform
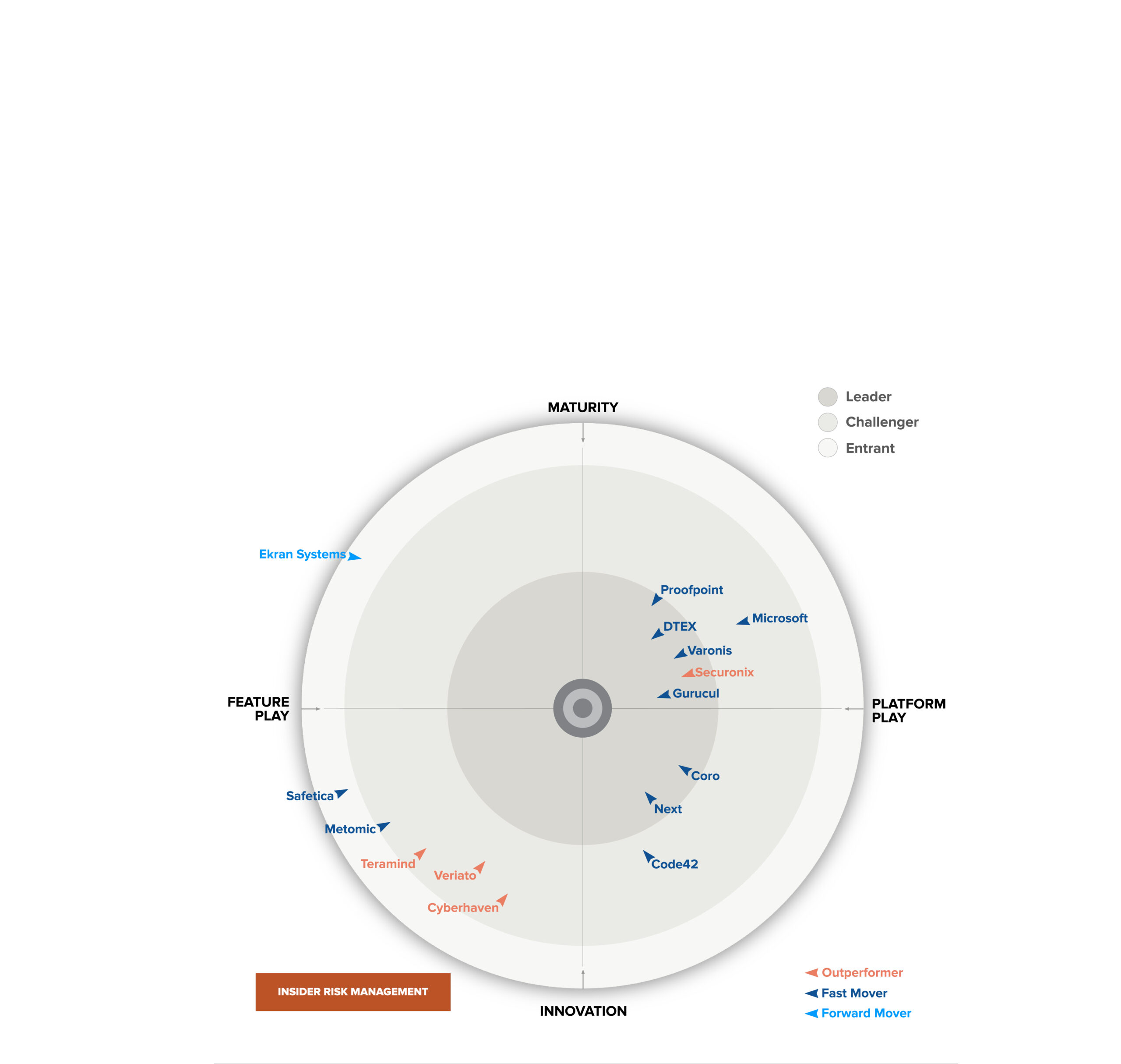
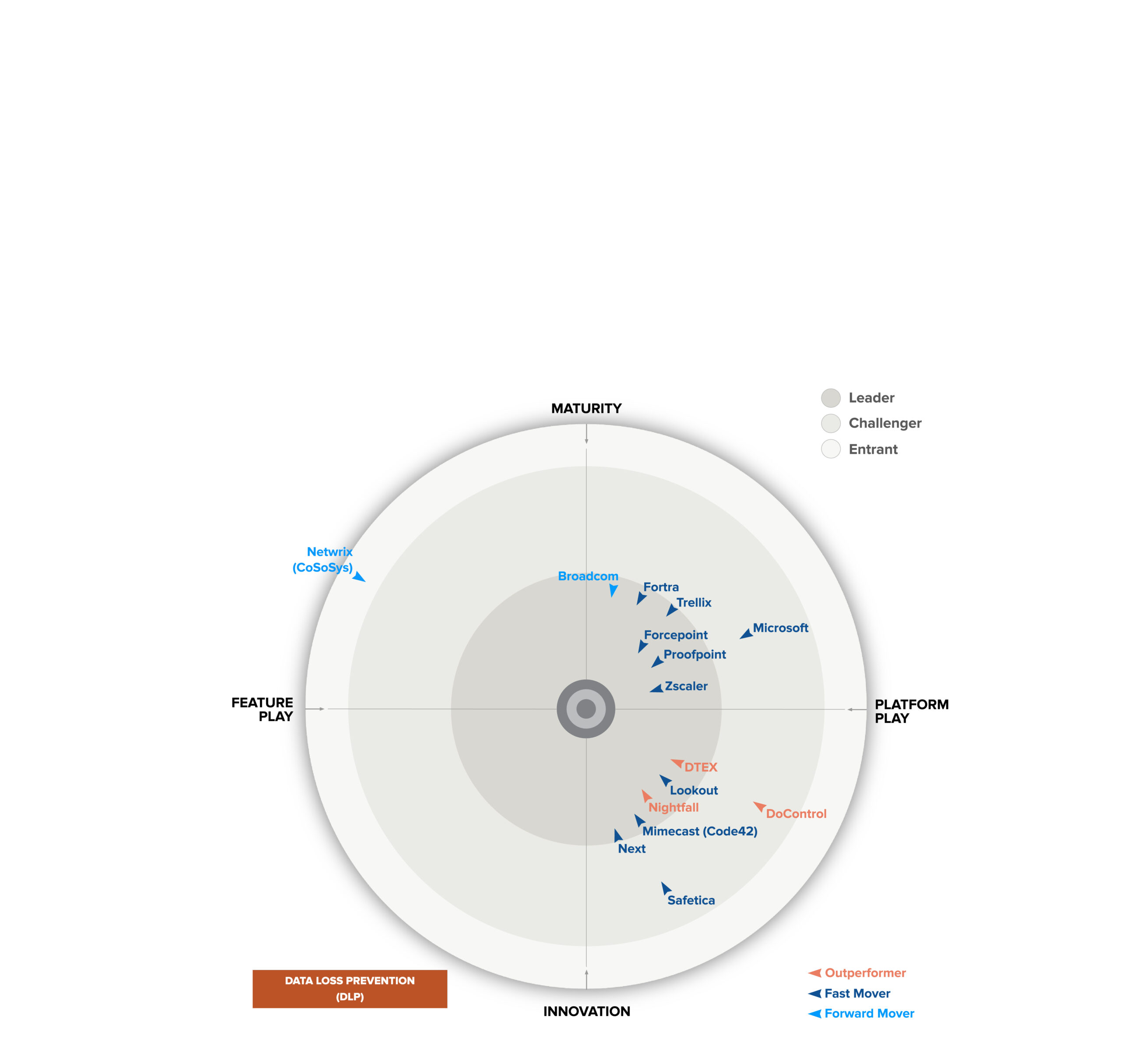
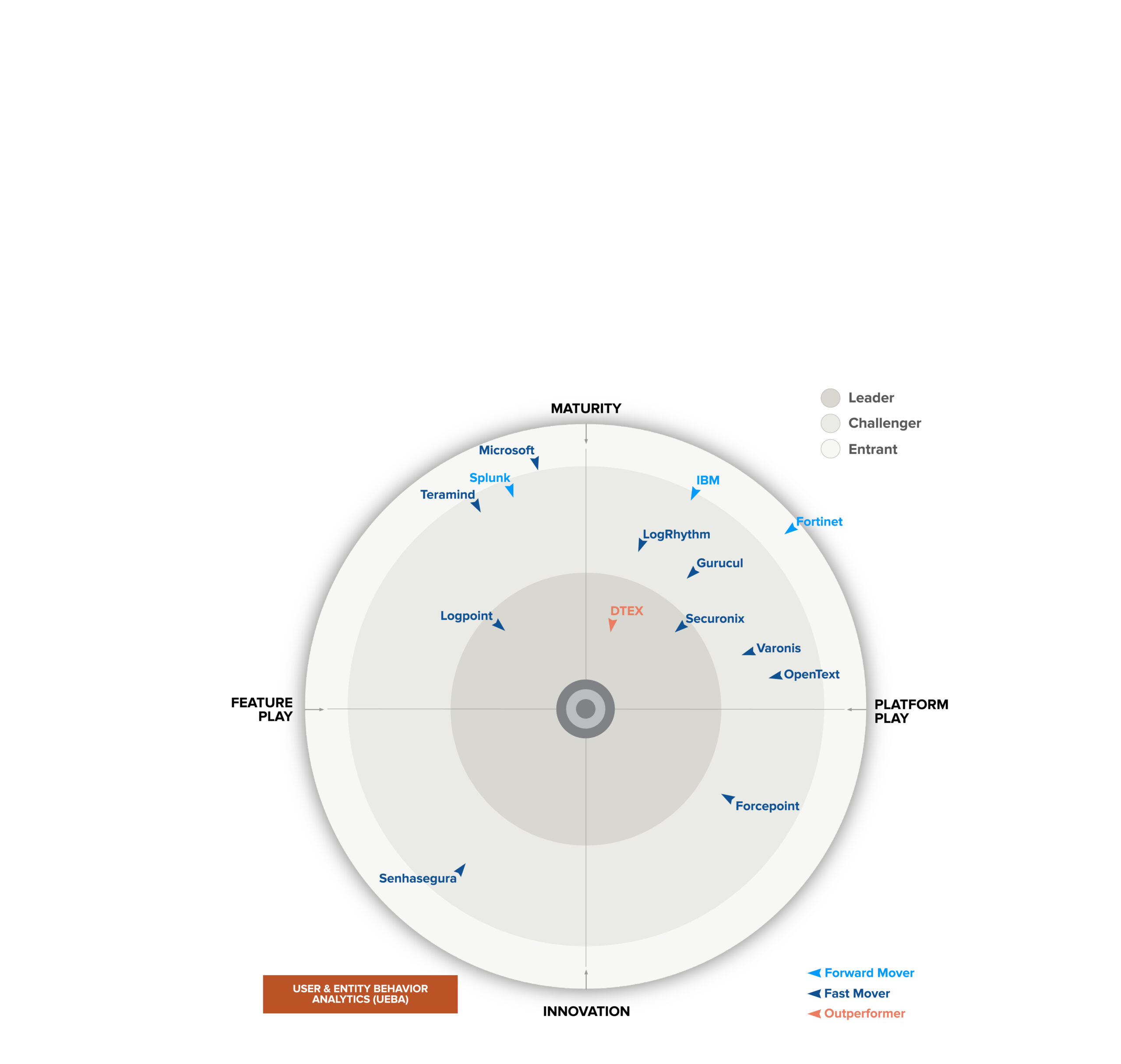
Analysts point to DTEX for insider risk management
DTEX i3: Delivering Trusted Insider Risk Investigations Support
DTEX Insider Intelligence and Investigations (i3) enables enterprise entities to strengthen their insider risk capability maturity to stop insider threats from materializing into data breaches. The team offers insider risk services and publishes regular research and threat advisories.
Ponemon 2025 Cost of Insider Risks Global Report
Independently conducted by the Ponemon Institute

Customer Insights
Hear from Melissa, Lead at the Threat Management Center at Verizon, talk about her experience with DTEX as an insider risk management tool.
She touches on DTEX’s ability to deploy both on-prem and in cloud at mass scale, dynamic risk scoring, and behavioral analytics. She also offers advice to those looking to stand up an insider risk management program.