Fighting insider threats requires more than intelligence.
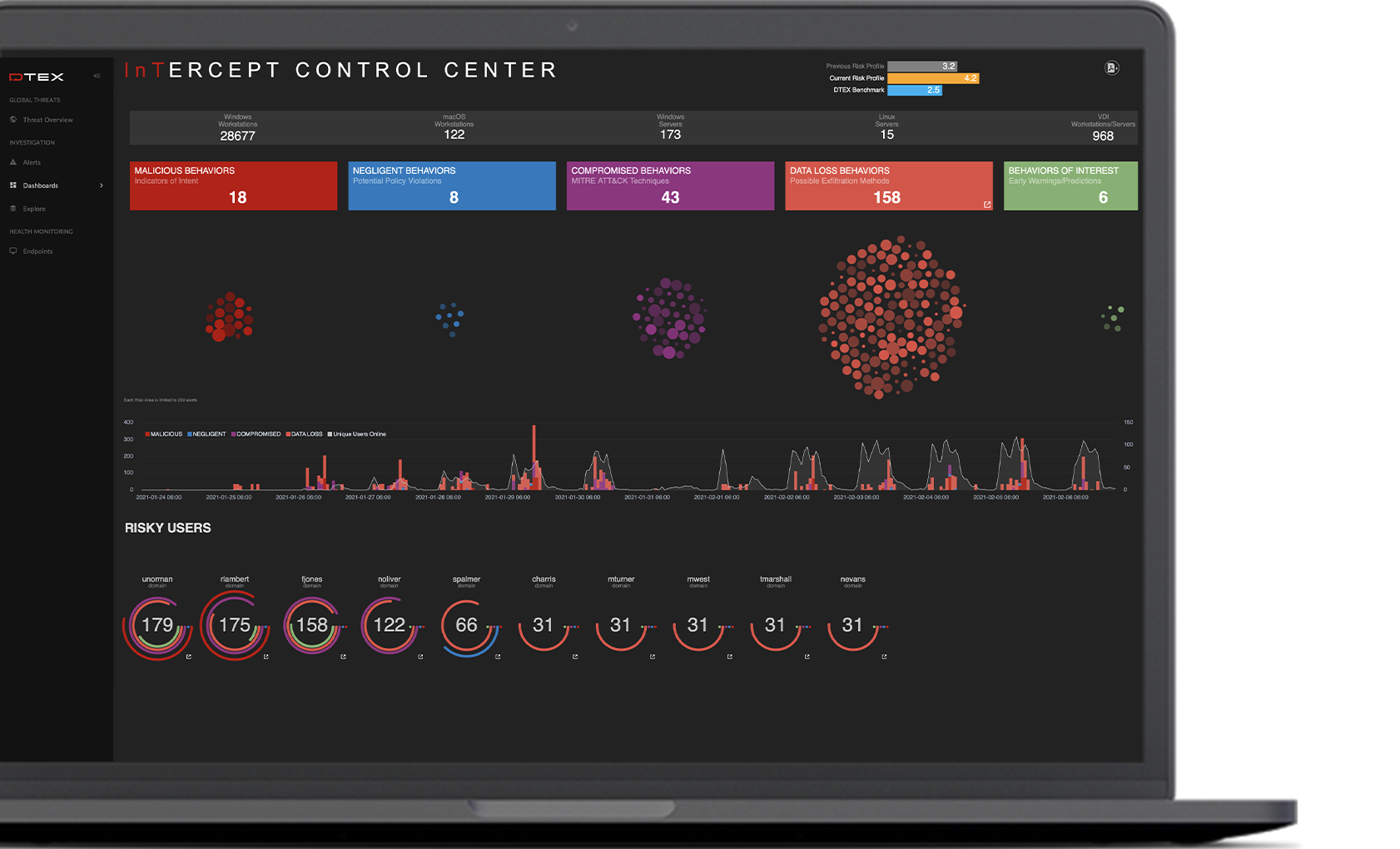
Insider threats can come from just about any angle. To stop them, you need a solution that brings context and Indicators of Intent to the task. DTEX combines an incredibly lightweight forwarder on each endpoint with a powerful server- based analytics engine to deliver proactive, privacy-conscious user awareness and protection.
With more telemetry than any other solution, DTEX utilizes patented behavioral enrichment techniques and predictive analytics to automatically build user-level activity profiles and identify sudden changes in behavior that indicate abnormal activity.
Four Steps to Put Behavior in Context
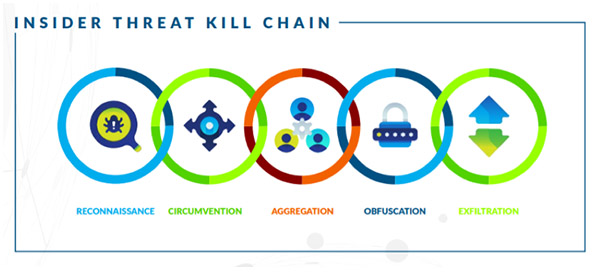
The Insider Threat Kill Chain
The vast majority of security threats follow a pattern of activity during an attack, and insider threats are no exception. Many security professionals will already be familiar with Lockheed Martin’s Cyber Kill Chain, which outlines the steps that APT attacks tend to follow from beginning to end. Since human behavior is more nuanced than machine behavior, however, insider attacks follow a slightly different path. Over the course of thousands of insider threat investigations and incidents, DTEX analysts have identified the insider equivalent: The Insider Threat Kill Chain, which encompasses the five steps present in nearly all insider attacks.
The Latest On Workforce Cyber Intelligence

Protect & Respect: 7 Endpoint DLP Capabilities that Empower the Virtual Workforce
How do you protect your organization against data loss, while enabling your workforce to be productive and showing respect for…
Read More
DTEX Insider Threat Mitigation Guide
Guidelines for evaluating Insider Threat Mitigation technology solutions and considerations for building an effective Insider Threat Detection and Response Program…
Read More
SANS Product Review: Smart Enterprise Visibility with DTEX InTERCEPT
Download this report from SANS for an assessment of how DTEX InTERCEPT can help your organization achieve its security objectives.
Read More

