Workforce Security and Management Software
A strong insider risk management program encompasses multiple security strategies, including user activity monitoring, data loss prevention, and user behavior analytics.
FAQs
If your organization is developing an insider risk management program or you want to strengthen your current solutions, our FAQs are a good place to start. If you have additional questions, please reach out to a DTEX team member for more information.
What is Endpoint Data Loss Prevention (DLP)?
What is the difference between Network DLP and Endpoint DLP?
What is a Data Loss Prevention Endpoint Agent?
What is Host-based Data Loss Prevention?
Data Loss Prevention Methods
Does DLP Detect Malware?
Data Loss Prevention vs. Data Leakage Prevention
What is UEBA?
What does User and Entity Behavior Analytics (UEBA) provide?
What is the difference between User and Entity Behavior Analytics (UEBA) and User Behavior Analytics (UBA)?
What is an Insider Threat?
Types of Insider Threats
What is the difference between Insider Threat and Insider Risk?
What are Malicious Insiders?
What are “Super Malicious” Insiders?
How to Detect Insider Threats
What are Insider Threat Indicators of Intent?
What is a Remote Work Security Policy, and how can you develop one in your organization?
How can you prevent insider attacks?
How does AI assist with insider risk investigations?
What is the DTEX Ai³ Risk Assistant?
What can the DTEX Ai3 Risk Assistant do?
Have more questions? Contact us to learn more about Insider Risk Management.
The Latest in Insider Risk Management

DTEX and CrowdStrike Bring Endpoint Telemetry Together
DTEX and CrowdStrike have partnered to bring together behavioral context and deep endpoint telemetry for better real-time visibility.
Read More
Workforce Visibility Without Privacy Intrusion
Traditional employee monitoring solutions rely on intrusive surveillance techniques. Learn how DTEX's privacy-by-design approach works.
Read More
A Modern Approach to Employee Engagement and Well-being
Workforce Cyber Intelligence is the Future of Work and Privacy by providing insightful and actionable analytics on your organization’s workforce,…
Read More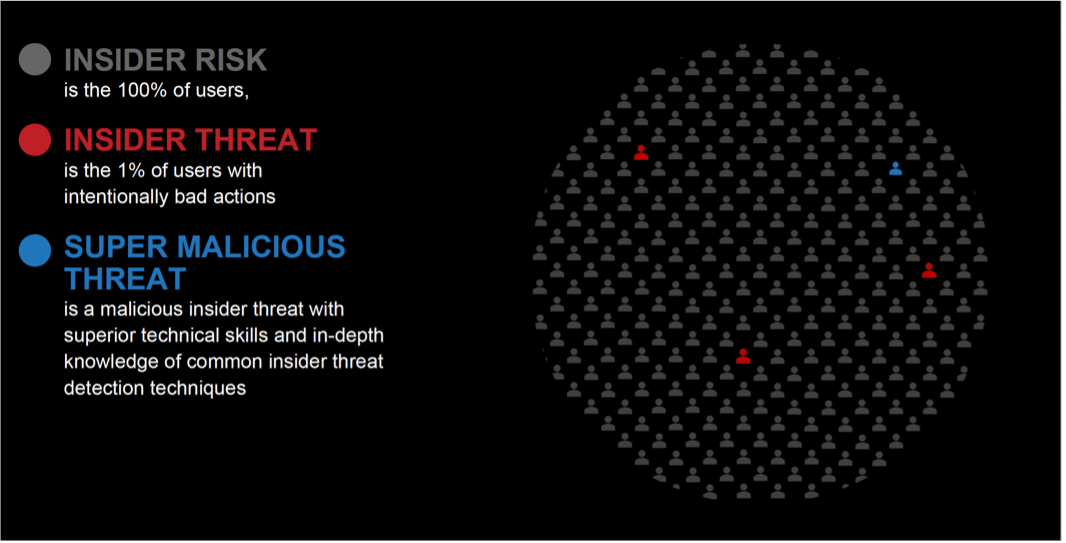 Anyone who has access to sensitive information is an insider risk. Humans make mistakes, whether accidentally emailing data to the wrong recipient, misplacing their computer, or having company data stolen from their car. Insider risks are also those who place sensitive data at risk by misusing it with innocent intent, including sending sensitive information to their private email or cloud storage accounts so they can work remotely.
Anyone who has access to sensitive information is an insider risk. Humans make mistakes, whether accidentally emailing data to the wrong recipient, misplacing their computer, or having company data stolen from their car. Insider risks are also those who place sensitive data at risk by misusing it with innocent intent, including sending sensitive information to their private email or cloud storage accounts so they can work remotely.
 To stop the super malicious insider, organizations need to understand how their actions differ from insiders with benign intent and from malicious insiders with lesser technical skills. To do so, organizations cannot rely on detecting overt actions such as those covered by rule-based DLP solutions.
To stop the super malicious insider, organizations need to understand how their actions differ from insiders with benign intent and from malicious insiders with lesser technical skills. To do so, organizations cannot rely on detecting overt actions such as those covered by rule-based DLP solutions.