Insider risks can no longer be ignored
$
M
in costs
average annual cost of insider-led cyber incidents (2023 Ponemon Cost of Insider Risks Global Report)
%
involve humans
Eighty five percent of breaches involved human interaction (Verizon 2021 Data Breach Investigation)
days to contain
Insider incidents take an average of 86 days to contain and every additional day, costs you more.
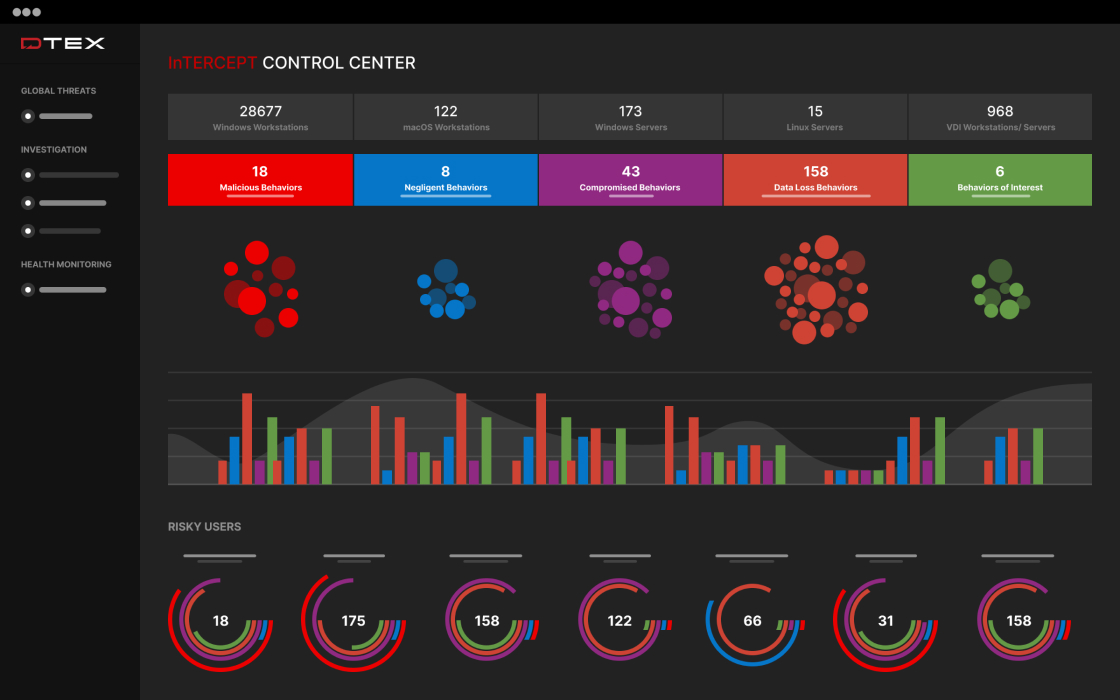
DTEX prevents risks from becoming costly threats
Predictive, proactive, preventative
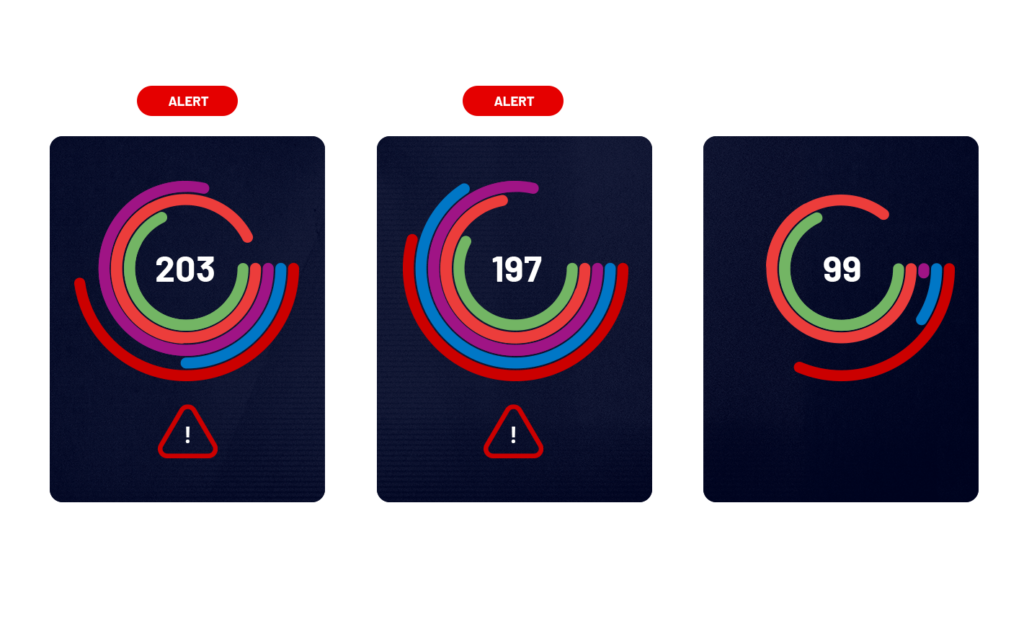
DTEX analyzes activity, trends, and behavior to provide actionable intelligence and early warning signs of insider threats. Quickly answer Who, What, When, Where, and How. Detect and automate responses to prevent data loss or theft.
Privacy to address multiple use cases
Lightweight and scalable
Cutting edge research & intelligence
KEY RESOURCES
Ponemon’s 2023
Cost of Insider Risk
Global Report
The 2023 Ponemon report examines insider risk costs and offers new insights into how organizations fund their insider risk management programs.

Ready to get started?