i³ Threat Advisory: MSDT Exploit Detection, CVE-2022-30190
ACT NOW TO MITIGATE RISK
- Confirm that KB5015805 has been installed across all endpoints running Windows.
- If the security update is not installed, you can apply a workaround until patching can be implemented by disabling MSDT URL:
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command “reg export HKEYCLASSES_ROOT\ms-msdt _filename”.
- Execute the command “reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.For information on the effects of these mitigation steps and how to reverse them please refer to the references section and the Microsoft blog on this vulnerability.
For information on the effects of these mitigation steps and how to reverse them please refer to the Resources section at the bottom of this Threat Advisory.
INTRODUCTION
On May 30 2022, Microsoft issued an alert (CVE-2022-30190) regarding the Microsoft Support Diagnostic Tool (MSDT) vulnerability. It affects the following versions of Windows; 8.1, Server 2012 R2, Server 2012, 7, Server 2008 R2, and Server 2008 SP2.
The CVE describes a Remote Code Execution (RCE) vulnerability that exists when MSDT is called using the URL protocol from a calling application, such as Microsoft Word. An attacker who successfully exploits this vulnerability can run arbitrary code with the privileges of the calling application. The attacker can then install programs, view, change, delete data, or create new accounts in the context allowed by the user’s rights.
DTEX customers should review environments for suspicious behavioral indicators outlined in the Threat Advisory referenced below.
The DTEX i³ team often observes unsupported Windows systems, like those that are exploitable by the vulnerability CVE-2022-30190. Through research and working with organizations like MITRE Corporation, it is known that malicious insiders may have a high degree of technical capability, including the ability to use proof of concept (POC) exploits of existing CVE vulnerabilities.
Based on the experience of the DTEX i³ team, old servers are either currently being used as file servers or document archiving, which would be a rich target for malicious insiders to try and gain access to and then exfiltrate valuable information.
INVESTIGATION AND DETECTION
DTEX i³ Research
This attack can be used against a variety of Microsoft products that rely on the msdt.exe process to help diagnose issues with Microsoft programs. The following program processes can be used as an attack vector:
- Outlook.exe – Outlook Application
- Winword.exe – Word Application
- Excel.exe – Excel Application
- Powerpnt.exe – PowerPoint Application
- Onenote.exe – OneNote Application
- MSpub.exe – Publisher Application
- MSaccess.exe – Access Database Application.
Based on actual exploitation testing of the vulnerability by the DTEX i³ team, it is seen that msdt.exe is a child process being executed by a parent process being any of the Microsoft products. In this case, Microsoft Word is the parent process as the malicious file is a .doc file.
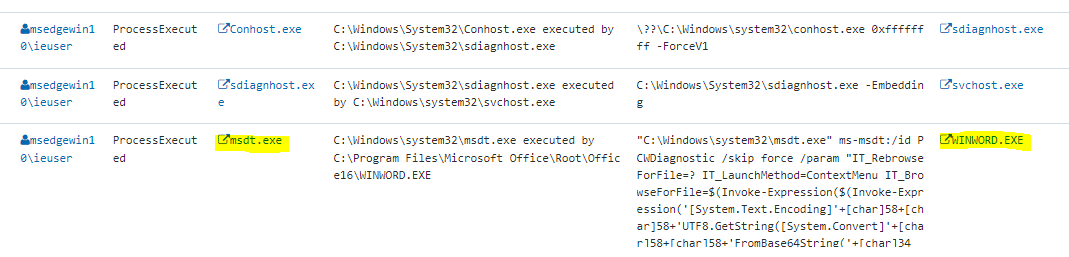
The following payload commands are required by a malicious insider in order to successfully carry out the attack. Because these fields are required, it is with high confidence that if the following three strings appear in the command line/Process Parameters that potential exploitation is underway.
PCWDiagnosticIT_RebrowseForFile=?IT_BrowseForFile
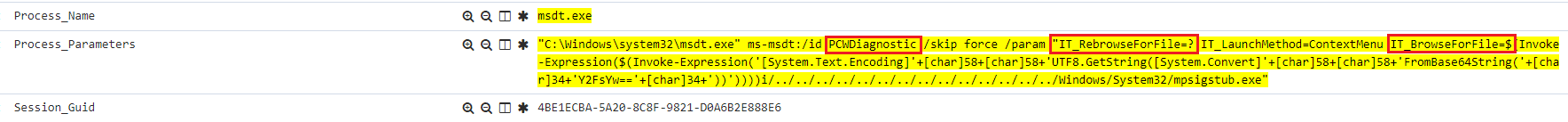
Detection Query
The following search query combines all of the attack TTP’s and should be used in the Discover page search bar to review for matching logs:
Process_Name:(msdt\.exe) AND Process_Parameters:(*PCWDiagnostic* AND *IT_RebrowseForFile* AND *IT_BrowseForFile*) AND Parent_Process_Directory:(*Microsoft*)CONCLUSION
Addressing security vulnerabilities requires a comprehensive approach that encompasses regular security assessments, ongoing monitoring, and patching. By understanding and proactively searching for vulnerable endpoints, organizations can significantly enhance the resilience of their overall security and limiting the ability of malicious insiders.
Continuous security testing, threat hunting within the DTEX InTERCEPT platform and staying abreast of emerging security trends are vital components to identify and remediate web application security vulnerabilities. For support relating to this Threat Advisory, contact the i³ team.
RESOURCES
This blog covers the affected versions of Windows, mitigations, Defender detections and Protections that are in place, explanation of possible exploitation attempts, and an FAQ. A complementary resource to this would be, Security Update Guide – Microsoft Security Response Center.
The Cybersecurity & Infrastructure Security Agency (CISA) regularly release timely and relevant information on trending threats facing American Critical Infrastructure. This announcement highlights the criticality of the vulnerability and the initial workaround for organizations to implement.
