i³ Threat Advisory: People's Republic of China - Volt Typhoon
ACT NOW TO MITIGATE RISK
- Harden domain controllers and monitor event logs for ntdsutil.exe and similar process creations.
- Any use of administrator privileges should be audited and validated to confirm the legitimacy of executed commands.
- Administrators should limit port proxy usage within environments and only enable them for the period of time in which they are required.
- Investigate unusual IP addresses and ports in command lines, registry entries, and firewall logs to identify other hosts that are potentially involved in actor actions.
- In addition to host-level changes, review perimeter firewall configurations for unauthorized changes and/or entries that may permit external connections to internal hosts.
- Look for abnormal account activity, such as logons outside of normal working hours and impossible time-and-distance logons (e.g., a user logging on from two geographically separated locations at the same time).
- Forward log files to a hardened centralized logging server, preferably on a segmented network.
INTRODUCTION
CISA (Cybersecurity and Infrastructure Security Agency) has issued a joint Cybersecurity Advisory (CSA) to highlight a recently discovered cluster of activity of interest associated with a People’s Republic of China (PRC) state-sponsored cyber actor, also known as “Volt Typhoon.” One of the actor’s primary Tactics, Techniques, and Procedures (TTPs) is living-off-the-land, which uses built-in network administration tools to perform its objectives. In this Threat Advisory, DTEX has provided queries that security teams can use to surface potential IOCs (Indicators of Compromise) within their environment using the DTEX InTERCEPT platform. Behavioral indicators can also be legitimate system administration commands that appear in benign activity. Care should be taken not to assume that findings are malicious without further investigation or other IOCs.
Advanced Persistent Threats (APTs) often refer to Government-funded threats that have long cycles of development and significant resources to compromise their targets.
iTA-23-03 highlights Volt Typhoon and the detection capability within DTEX to uncover behaviors of users. Traditional Endpoint, Detection and Response (EDR) often focus on malicious atomic IOCs or the behavior around to abuse of native tools. This may not be enough to uncover state-sponsored threat actors who are excellent at appearing normal once they have infiltrated or have a malicious (or unknowing) insider acting on their behalf.
INVESTIGATION
The following queries can be used to help surface potential IOCs related to the threat actor on host systems.
The threat actor has been observed to have executed a command to gather information about local drives. The following DTEX query can be used to potentially surface related activity.
Process_Name:(WMIC.exe) AND Process_Parameters:(*caption,filesystem,freespace,size,volumename*)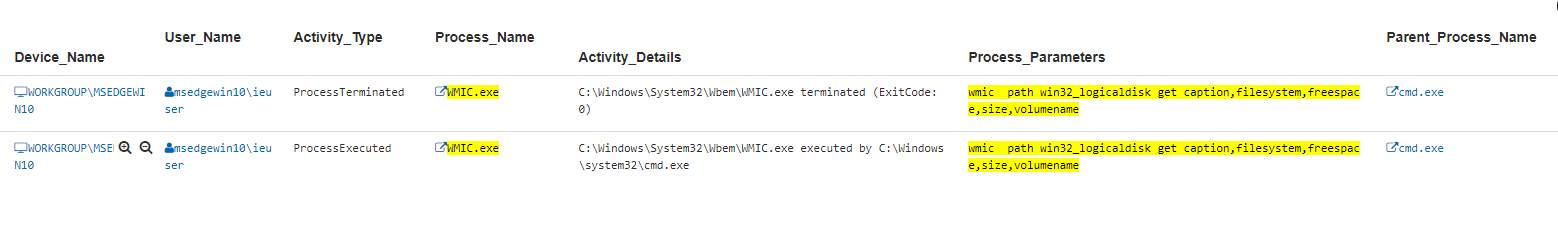
The threat actor is believed to try and exfiltrate the ntds.dit file and the SYSTEM registry hive from Windows domain controllers (DCs) out of the network to perform password cracking. The following DTEX query can be used to surface activity related to the creation of a shadow copy from which the actor utilizes.
Process_Name:(vssadmin.exe) AND Process_Parameters:(*vssadmin* AND *create* AND *shadow* AND *\/for\=*)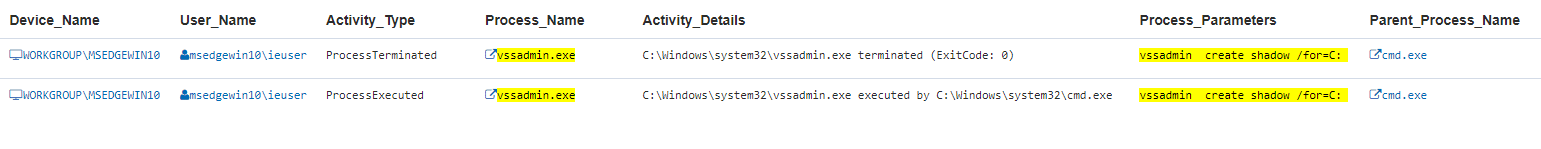
The threat actor was observed to have used the command line version of 7zip to potentially compress and password-protect zip folders possibly to prepare data for exfiltration. The following query can help surface command line 7zip compressing. Other compression software should also be searched for.
Process_Name:(7z.exe) AND Process_Parameters:(*7z\.exe* AND *-p* AND *c\:\\windows\\temp\\*)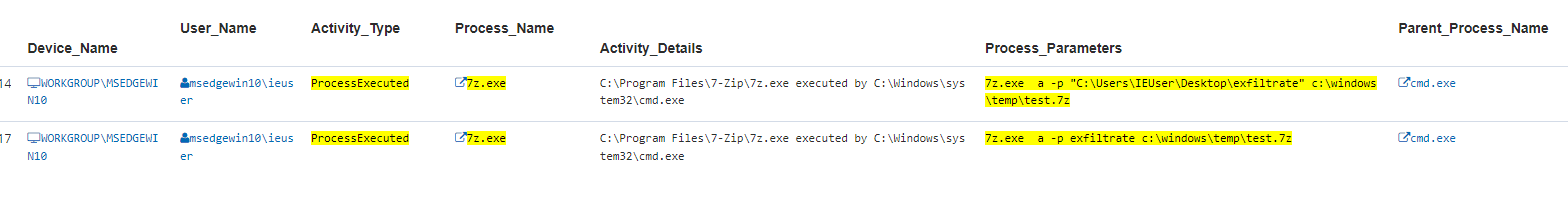
Implants utilized by the threat actor have been observed with a number of different process names, as noted in the original Cybersecurity Advisory (CSA). The following query searches for any activities that pertain to a non-exhaustive subset of known process names.
Process_Name:(WmiPreSV.exe OR cisco_up.exe OR watchdogd.exe OR "cl64.exe")CONCLUSION
APTs, like Volt Typhoon, are often considered to be some of the best threat actors. This is due to the amount of funding, development, and often government backing. After the initial foothold into an organization’s environment, they will often blend in as much as possible and only use applications and tools that already exist, known as living-off-the-land. While traditional EDR often struggles to detect this type of behavior, if an organization has a good baseline of its user activities day-to-day, it is highly likely that the APTs risk profile would quickly rise to the top of suspicious users.
INVESTIGATIONS SUPPORT
For intelligence or investigations support, contact the i³ team.
RESOURCES
CISA Cybersecurity Advisory AA23-144a
The Cybersecurity & Infrastructure Security Agency (CISA) regularly release timely and relevant information on trending threats facing American Critical Infrastructure. This CSA highlights evolving threat, and TTPs posed by the threat actor Volt Typhoon.
The Australian Signals Directorate (ASD) in conjunction with the US National Security Agency (NSA), the US CISA, the US Federal Bureau of Investigation (FBI), the Communications Security Establishment’s Canadian Centre for Cyber Security (CCCS), the New Zealand National Cyber Security Centre (NCSC-NZ) and the United Kingdom National Cyber Security Centre (NCSC-UK), release an advisory relating to the Volt Typhoon threat and where organizations could seek assistance.
