Leadership spotlight: Insider risk, AI security and data defense
Explore insights from industry leaders on protecting sensitive data, managing insider risk, and navigating the impact of AI in the workplace. Learn how behavioral analytics, risk-adaptive strategies, and AI-aware policies help organizations detect abnormal activity, prevent data loss, and maintain enterprise-wide resilience against today’s most sophisticated cyber threats.
Featuring:
- Kevin Mandia, Founder, Mandiant
- Howard Holton, CEO, GigaOm
- David Hahn, Operating Partner, Ballistic Ventures
Customer perspective: Strengthening insider risk management and data protection
See how organizations are tackling insider threats and protecting sensitive data with behavioral analytics and proactive security tools. Learn how enterprises use automated insights to identify risky behaviors, safeguard intellectual property, ensure regulatory compliance, and build a security-conscious culture across their teams.
National defense and the insider evolution
Explore the evolving threats to critical infrastructure, including insider risks, nation-state adversaries like DPRK, and AI-driven attacks. Learn how advanced detection and behavioral analytics help organizations identify suspicious activity, prevent data exfiltration, and strengthen national security and operational resilience.
Partner feature: The power of OpenSearch with AWS
Discover how organizations tackle modern data challenges by analyzing vast volumes of structured and unstructured data. With real-time analytics, AI-driven capabilities, and platforms like OpenSearch, businesses can gain actionable insights, enhance security and observability, and make faster, data-driven decisions.
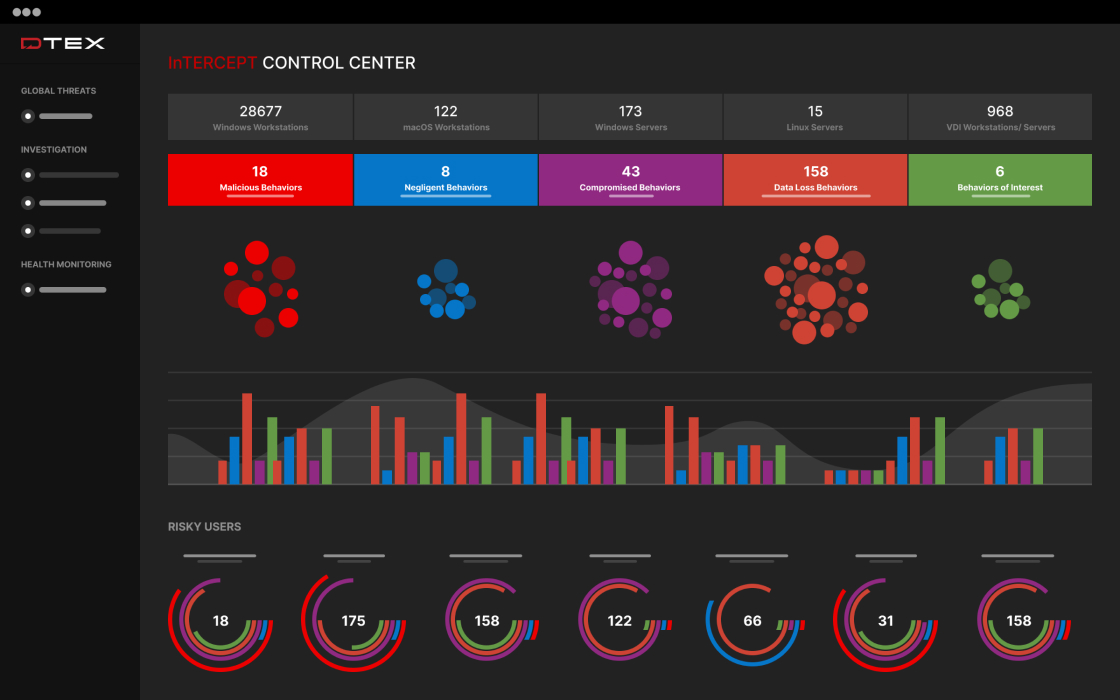
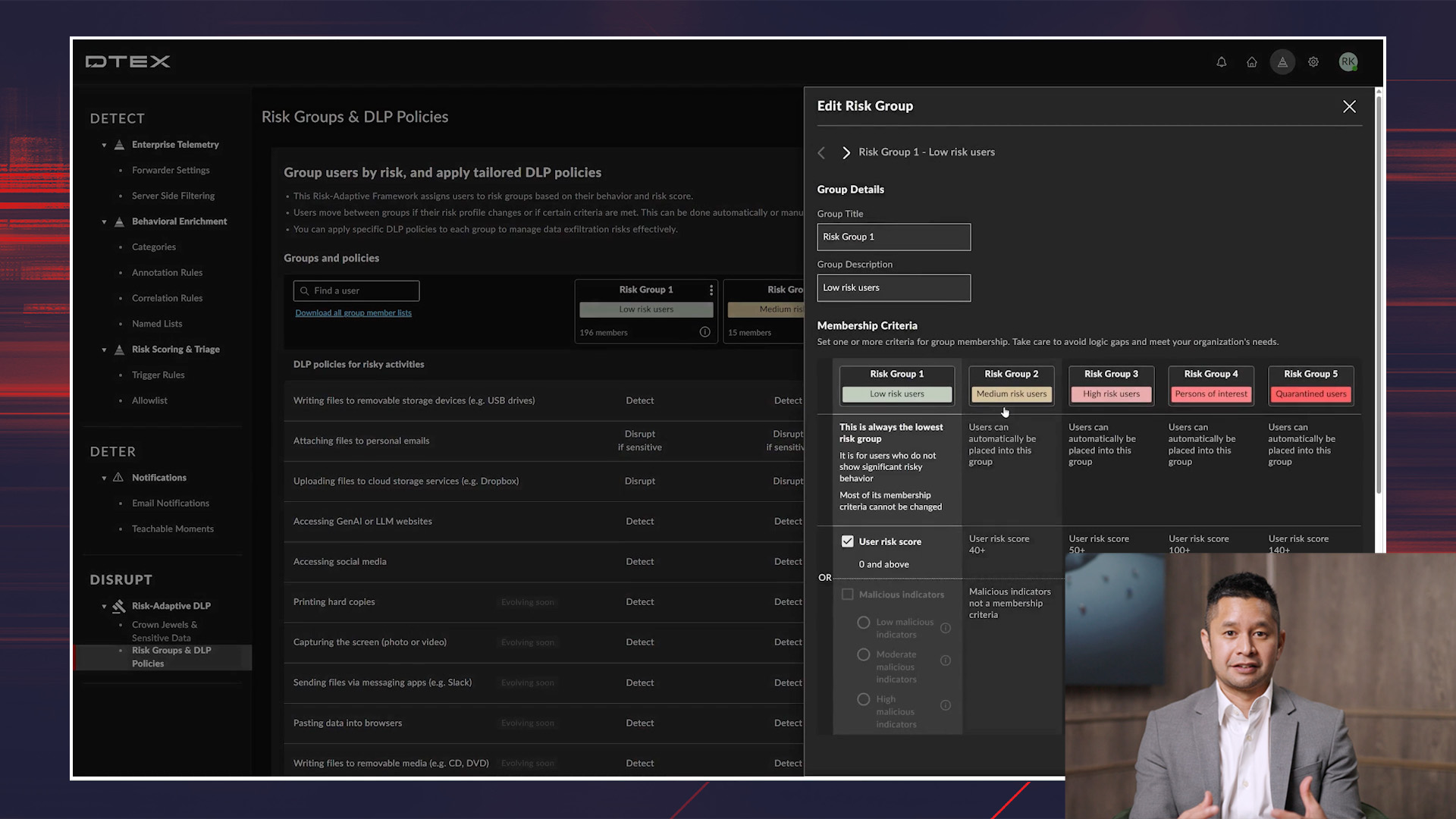
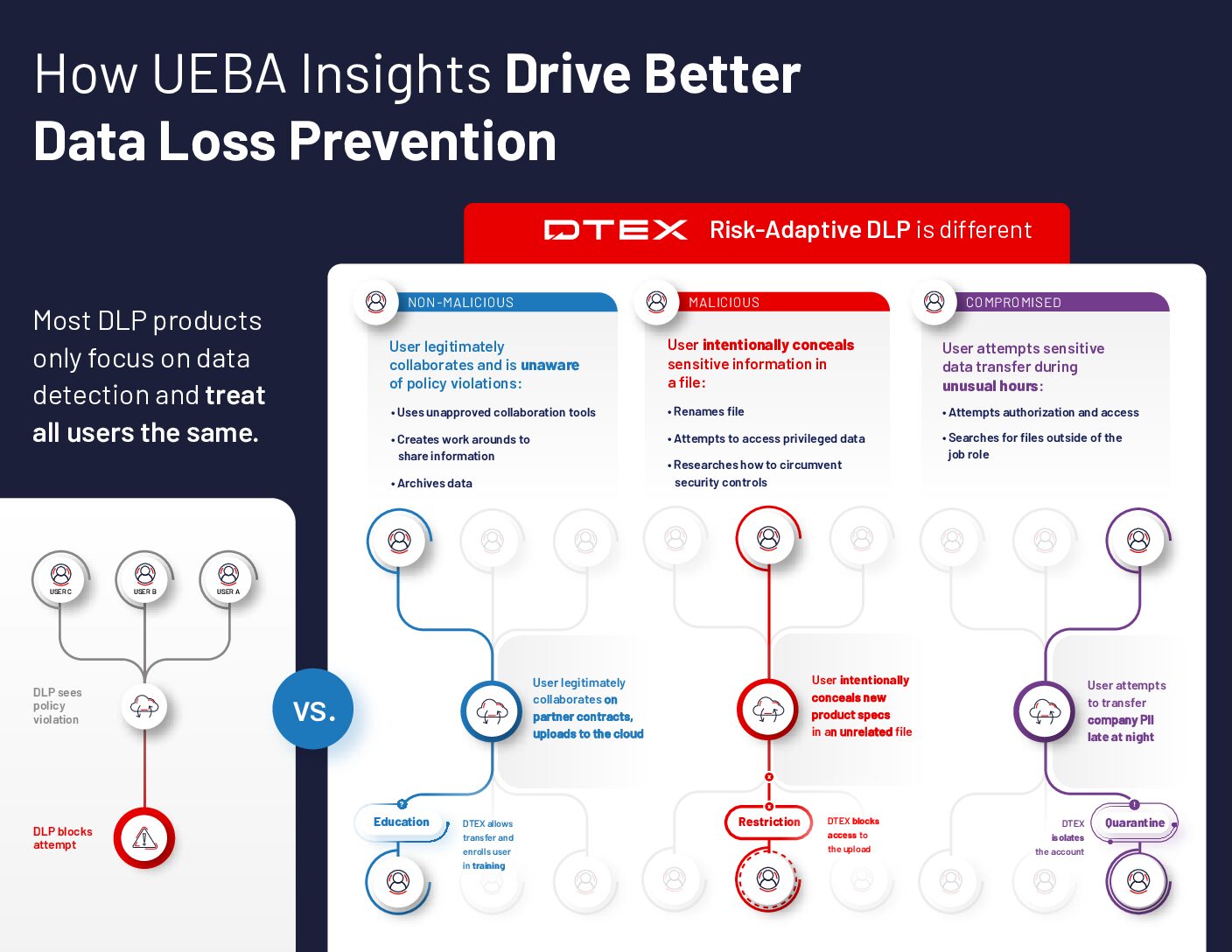
Demo: DTEX Risk-Adaptive DLP
Discover how DTEX Risk-Adaptive DLP combines behavioral analytics, AI monitoring, and dynamic policy enforcement to prevent data loss and detect insider threats. Learn how organizations can track risky user behavior, identify unapproved AI tool usage, and leverage automated investigative workflows for comprehensive, proactive security and compliance.
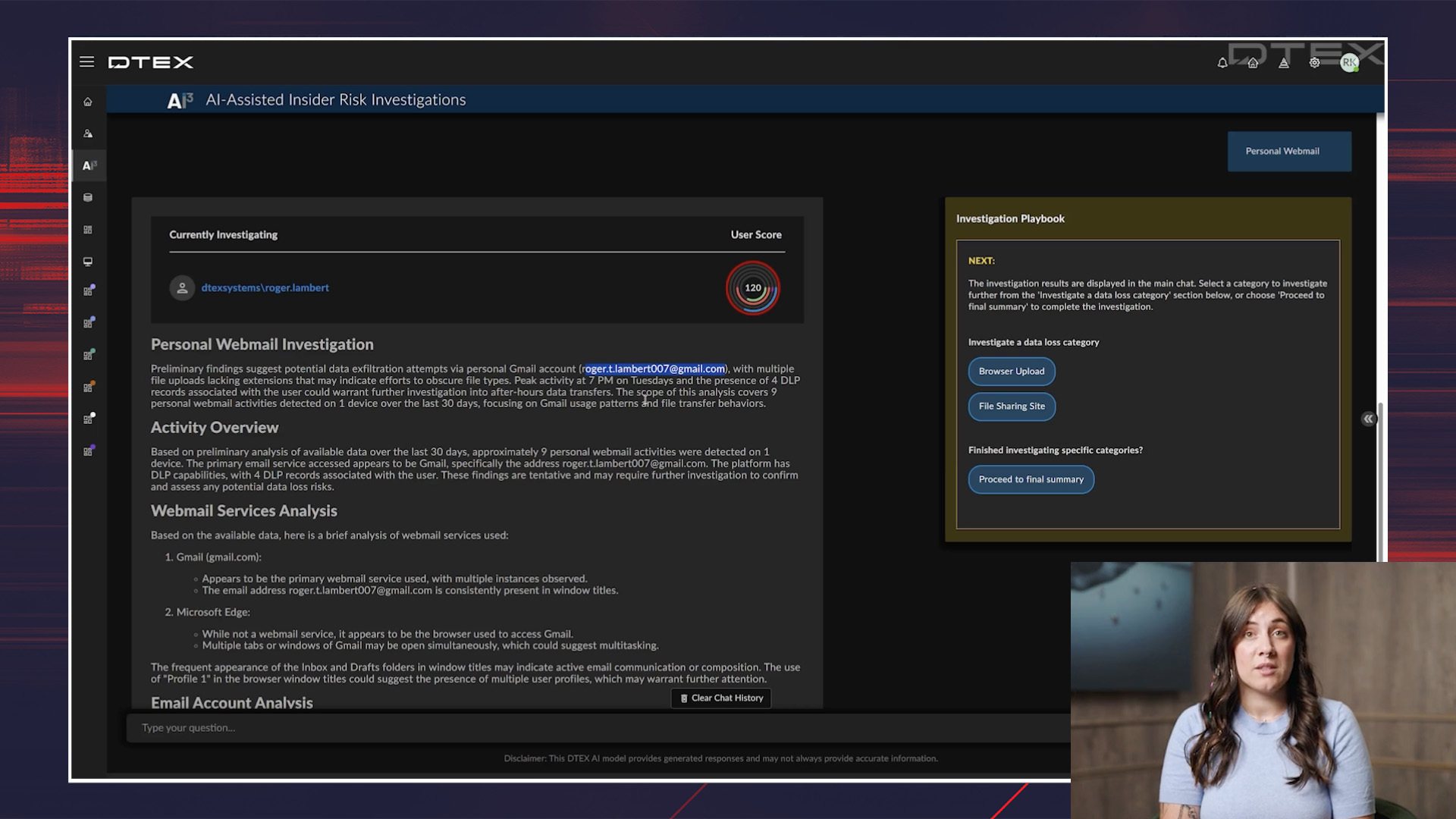
Demo: Shadow AI investigation
Learn how analysts can identify risky user behavior and shadow AI usage using investigative dashboards and tools. Leveraging platforms like OpenSearch, visualizations, and AI-driven risk assistants, organizations can track activity timelines, detect unapproved AI tools, and generate comprehensive reports to support faster, data-driven security investigations.
Ready to get started?