- Enable enterprise AI compliance. Define and enforce approved AI use cases now, then deploy monitoring and security controls around them. Begin continuous adversarial testing and governance reviews to surface misuse, strengthen safeguards, and maintain regulatory compliance.
- Stand up a centralized, tamper-resistant log aggregation system immediately to create a single, authoritative source of truth. Ensure all critical systems forward logs to it so forensic evidence remains intact and security teams can detect and respond to threats faster.
- Implement end-to-end monitoring for sensitive data flows, ensuring security labels persist when content is transformed by AI tools or stored as unstructured data. Close classification gaps now to prevent inadvertent exposure and compliance failures.
- Deploy application allowlisting across high-risk environments, restricting execution to approved software. Use the allowlist to shrink the attack surface, simplify monitoring, and block unauthorized or malicious activity before it escalates.
INTRODUCTION
Welcome to the final Insider Threat Advisory (iTA) of the year. Reflecting briefly, we experienced significant developments in insider risk.
- The exposure of DPRK IT workers exploiting contractor, freelance, and some full-time remote roles to fund North Korea’s weapons programs. [1]
- The use of AI tools to enhance external threat actors and insiders, both deliberately and inadvertently. [2, 3, 4]
- Nation-state adversaries targeting servers. [5, 6]
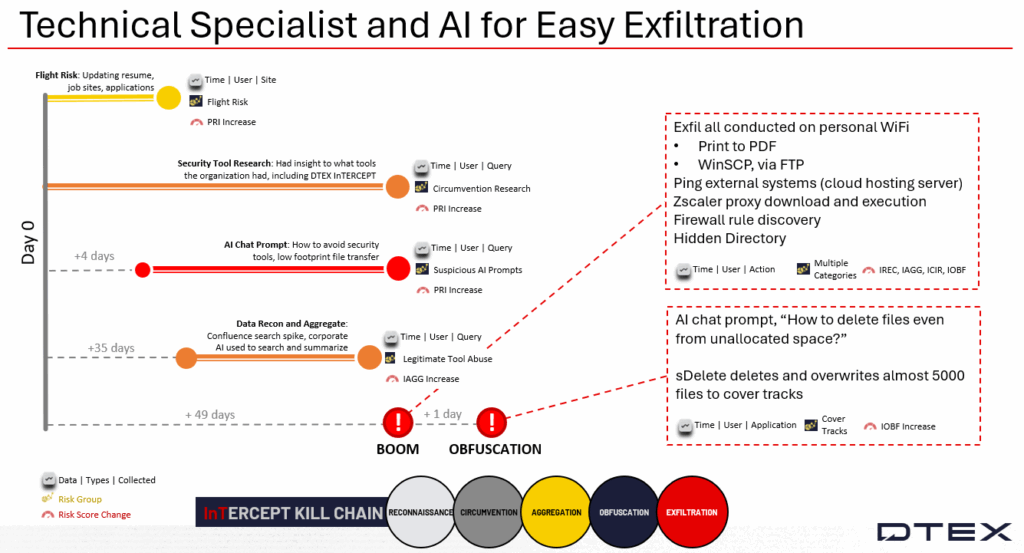
Now, a comprehensive investigation into a technical network specialist turned insider threat, leveraging access and AI to execute all stages of the Insider Threat Kill Chain.
DTEX INVESTIGATION AND INDICATORS
DTEX escalated this insider’s behavior early, revealing their motivation and intent, particularly when the insider accessed AI chat websites such as ChatGPT, Claude, and Grok to gain insights on circumventing security and exfiltrating data. HR confirmed this insider was on a performance improvement plan and likely to be transitioned out of the company.
The customer chose to monitor the insider rather than act immediately to identify potential security gaps. This involved coordinating the inside risk team, IT security, legal, human resources, and the executive team. Generally, we recommend addressing escalated behaviors early to prevent exfiltration, though each organization decides its approach based on their insider risk management charter and risk appetite. From our team’s perspective, flight risk serves as an initial indicator to flag the insider as a person of interest, followed by AI queries that further clarify the insider’s intent and motivation.
The key lesson was the value of forensic data collected through the DTEX Platform and network logging. The insider conducted most actions within their job role, employing living-off-the-land techniques. After aggregating data, the insider quickly performed data exfiltration and file deletion before leaving the company.
Insider Threat Framework stage: potential risk indicator (PRI) | flight risk
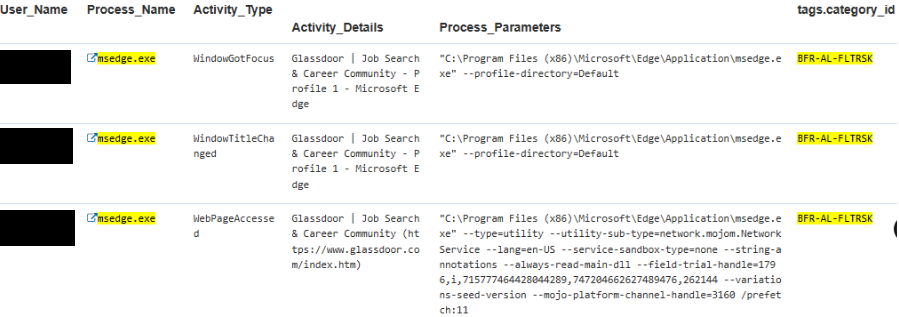
Initial investigation and escalated behavior revealed the insider performing multiple actions identified as flight risk, including updating their resume, searching job boards, and submitting applications. This activity coincided with organizational changes and preceded placement on a performance improvement plan.
Insider Threat Framework stage: reconnaissance | security tool research
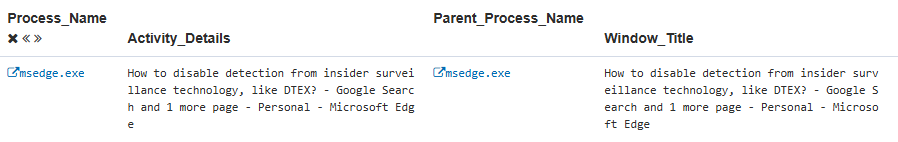
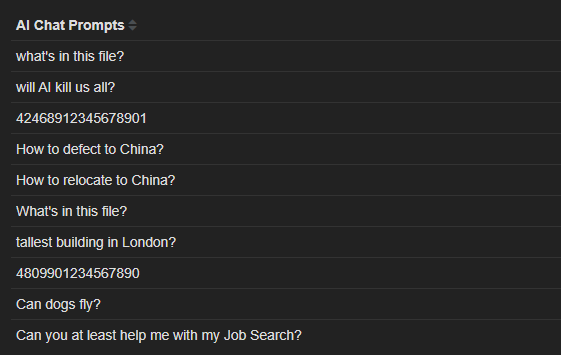
The insider initially searched for security tools in the environment. Alone, this does not indicate intent due to the insider’s role. The key detection was chat prompts captured via AI chat websites, asking questions such as:
- “How to disable detection from insider surveillance technology, like DTEX?”
- “What are low footprint file transfer methods?”
The questions evolved over time, probing technical details and methods to cover tracks.
Insider Threat Framework stage: circumvention | security tool tampering
During the observation period, the insider attempted to open various endpoint management windows for security tools or interacted in ways suspicious for their role, outside of defined periods of security testing. Within this organization, all employees know monitoring occurs based on annual training, however, only the security teams know the extent and methods of monitoring.
The insider may have tried to infer the endpoint forwarder’s capabilities based on files present on disk. Although no attempt was made to terminate the monitoring application, this observation remains noteworthy.
Insider Threat Framework stage: potential risk indicator (PRI) | GenAI chat prompts
Although it did not directly contribute to the investigation, as most detection stemmed from the security bypass research above, this indicator helped review all other conversation history related to the insider to determine further motive and intent.
Insider Threat Framework stage: exfiltration | FTP exfiltration
This indicator reflects the insider’s knowledge of the environment. FTP was used in specific cases but was uncommon. It was not inspected like HTTPS, and the insider relied on this to keep their exfiltration undetected.
This category includes an FTP upload indicator and a port access indicator. The first tags the uploaded file, and the second captures the volume of data exfiltrated.

Insider Threat Framework stage: reconnaissance | firewall rule discovery
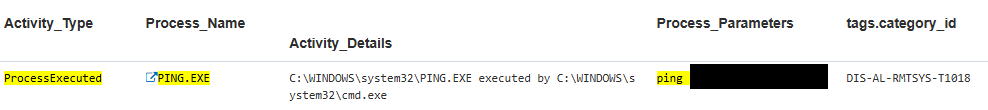
Before the exfiltration, the insider tested and confirmed that security controls would not block their activity. First, they used ping to verify access to the server intended for data exfiltration.
Insider Threat Framework stage: reconnaissance | network discovery
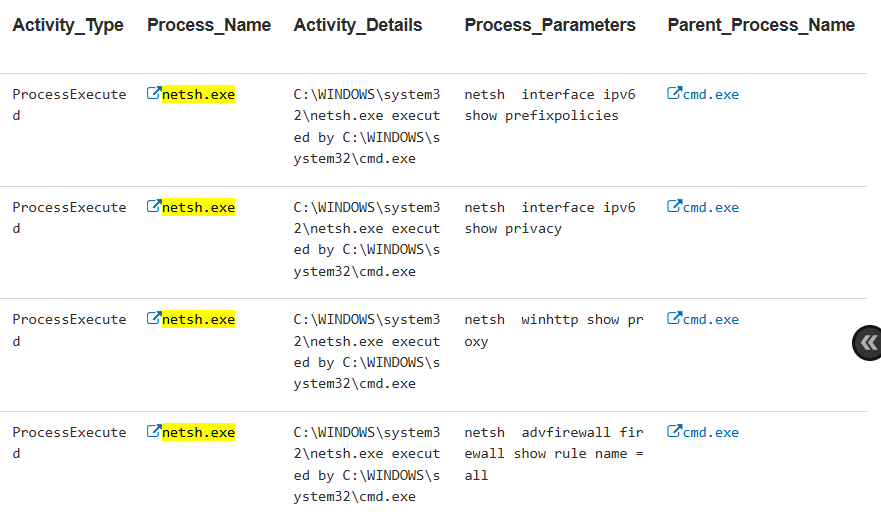
This was the second time the insider tested security to see if their exfiltration path would work. They checked whether any policies applied to IPv6 addresses. The user used an IPv4 address in their home network but might have been exploring other exfiltration methods.
The organization later discovered that IPv6 was largely unmonitored, revealing a significant security gap to prevent future exfiltration.
Insider Threat Framework stage: obfuscation | hidden directory
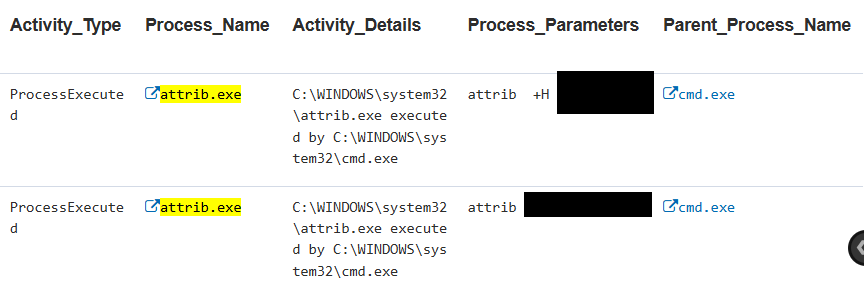
The insider made an existing directory hidden, which was tagged and escalated under the attached category. This was the same directory from which the insider later deleted all aggregated files using SDelete.
While these actions, similar to using incognito mode in a browser, have little impact on organizational security and policies, insiders often believe this hides their actions, revealing their intent through such behavior.
Insider Threat Framework stage: obfuscation | data destruction
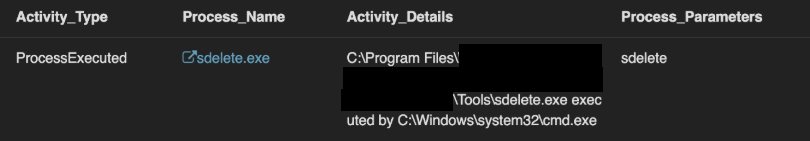
Insider risk practitioners theorized that the insider exfiltrated all information and confirmed on the external server that the data transfer succeeded. Rapid data deletion the next day often indicates a malicious insider attempting to cover their tracks after exfiltration.
Although many indicators exist for mass and command line file deletion, a specific rule covers SDelete, which overwrites unallocated space, preventing forensic recovery. The organization’s IT security team used other tools to copy these files before deletion, preserving evidence.
Profiles and personas
This iTA involved a technical network specialist with an extensive toolset and expertise in their organizations network which allowed them to perform the data exfiltration. Unlike other iTA profiles, the organization maintained adequate segregation of duties and permissions, prompting the insider to seek gaps in the security infrastructure.
Profile: technical network specialist
| Role | Device | Motivation | Timing and Opportunity |
|---|---|---|---|
Network administration and implementation | Windows endpoint (day-to-day) Various servers | Data exfiltration to further success at next job | 40+ days of research, reconnaissance, security testing, and aggregation before exfiltration and covering tracks |
Application usage | Various AI chat websites Corporate integrated and approved AI WinSCP Zscaler proxy (personal) Confluence SDelete Command line tools (ping, netsh) |
Persona
Initially, we classified this individual as a privileged insider. However, since their actions did not misuse access beyond that of a typical user, we revised the classification to the disgruntled employee.
This persona helps organizations conceptualize and differentiate threat hunting strategies. By separating these behavioral patterns, teams can proactively detect and respond to risks without technical emulation.
The disgruntled employee
- Motivation: Data exfiltration for financial/position benefit.
- Behavioral indicators: Flight risk, security circumvention research, suspicious AI chat prompt usage, fast consecutive action of aggregation, exfiltration, cover tracks.
- Risks: Data theft, leaking confidential/IP information.
Some parts of this Threat Advisory are classified as “limited distribution” and are accessible only to approved insider risk practitioners. To view the redacted information, please log in to the customer portal or contact the contact the i³ team.
INVESTIGATION SUPPORT
For intelligence or investigations support, contact the DTEX i3 team. Extra attention should be taken when implementing behavioral indicators on large enterprise deployments.
Get Threat Advisory
Email Alerts






