It’s exciting times for DTEX Insider Risk Management (IRM) users with the arrival of the new Risky Users dashboard, designed to simplify and connect useful information in a more analyst-centered workflow.
An evolution to the previous Alerts page that focused on a list of individual alerts, this latest iteration works to more efficiently connect behavioral indicators and build surrounding context into a single view. After all, with DTEX IRM, it’s about surfacing and connecting the most important information for faster assessment and triage. And this new view effectively provides the answers to questions like, “Who are my risky end users and why are they doing what they’re doing?”
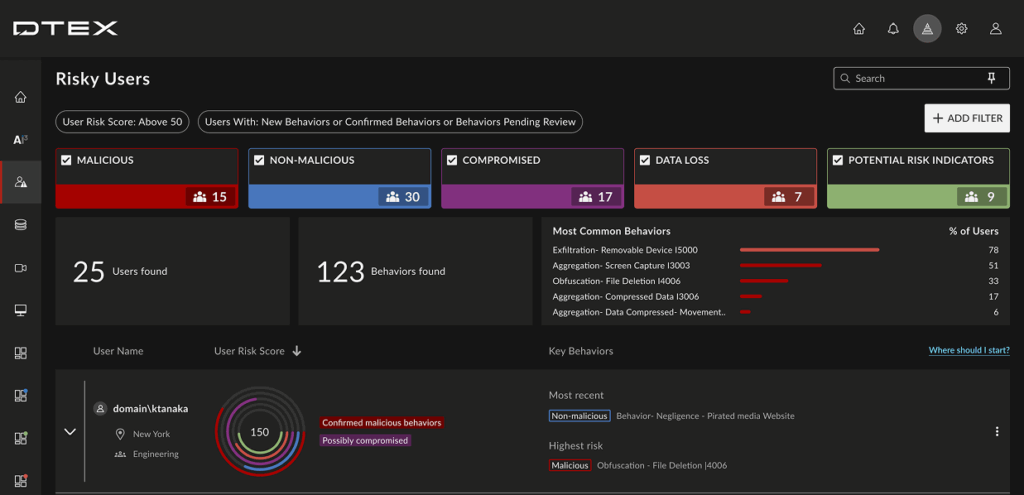
The shift to the risky user
This update focuses on bringing together content from different areas of the platform to minimize context switching. The summary at the top of the page highlights trends and totals risky behaviors associated with malicious, non-malicious (i.e., mistakes) and data loss activity. The page then ranks users by risk score and groups each user’s specific activity in a timeline, calling out the most recent and highest risk actions. Identifying and looking into contextualized activity early is what can stop data loss before it occurs.
Another benefit of the new view is the quick links to the surrounding data that provide deeper meaning and provide a better and fuller picture of what is taking place. These connected pathways provide discrete information about an individual’s activity and provide analysts with the opportunity to dig into escalated behaviors identified in a user’s risk score.
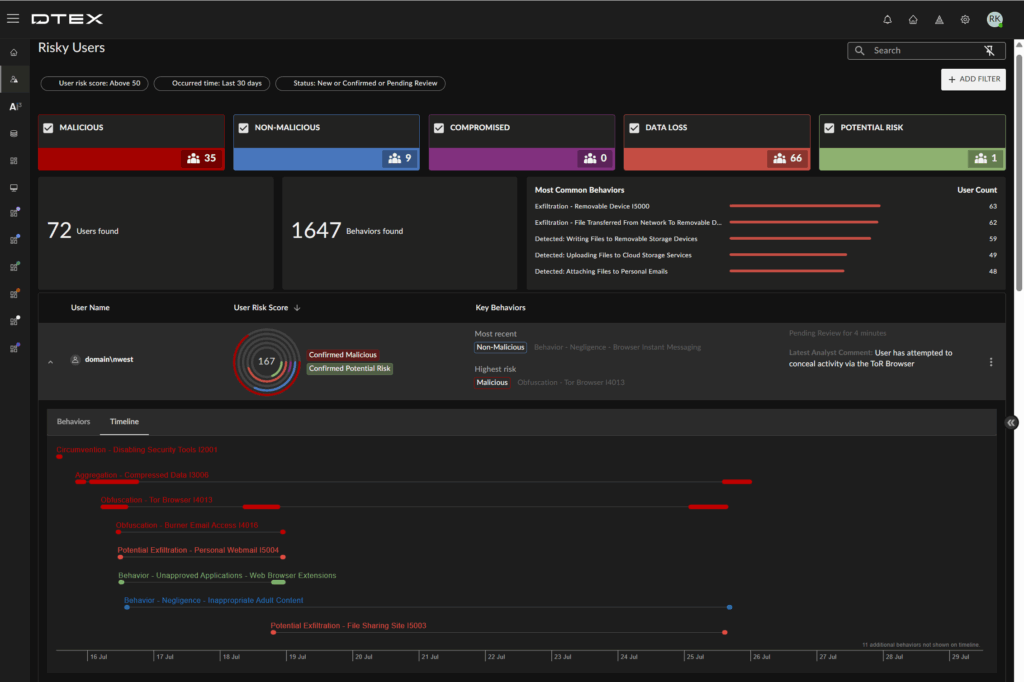
What is the DTEX differentiator? Behavioral insights.
Behavioral science is at the core of the DTEX Platform. And it starts with the continuous collection of a unique data set that spans both cyber and non-cyber sources, whether the data is important at the time or not. With this as a foundation, DTEX builds multidimensional risk scores to categorize activity, applying DTEX risk models and highlighting risky behavior that is associated with the precursors to insider threats and data loss events. The platform starts with a top-level view, so analysts know where to start and can streamline decision making.
Digging into the collection of escalated behaviors, which comprise a collection of discrete activities, provides risky behavior details and an automated, easy-to-understand summary of the behavior in non-technical terms.
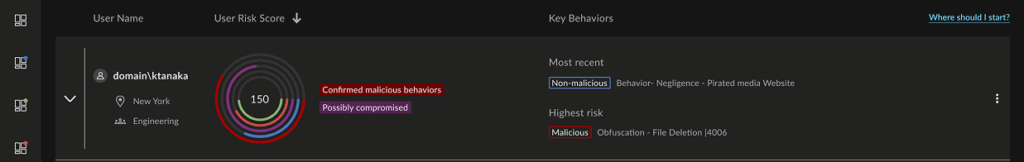
Because activity is grouped by end user and can include the user’s location and peer group (AD), analysts better understand the highest risk people. Context is king. This update combines all the meaningful data that drives analysts more efficiently in the immediate direction of that needle in the haystack.
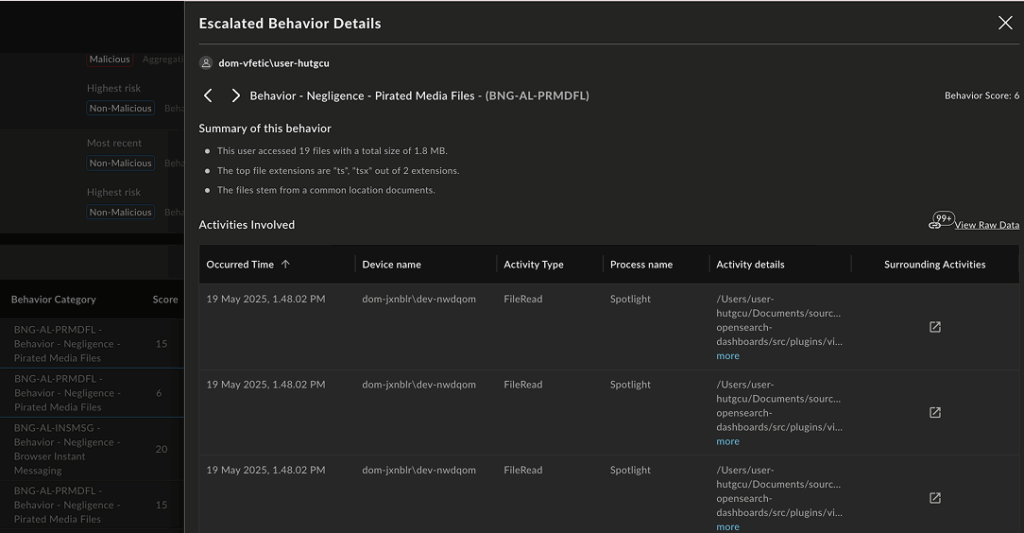
Decide next steps, faster
By bringing together context as early as we can and clustering related information in a way that reveals intent, analysts have the information they need to decide next steps. And it is the activities around each escalated behavior that tell the story of what the user is doing. This is routinely missed by other vendors in this area. Connecting the dots between users, activities, and data movement is key for quick triage and preventing data loss.
For more information and to see this live, reach out for a demo.
Subscribe today to stay informed and get regular updates from DTEX






