How does Risk-Adaptive DLP work?
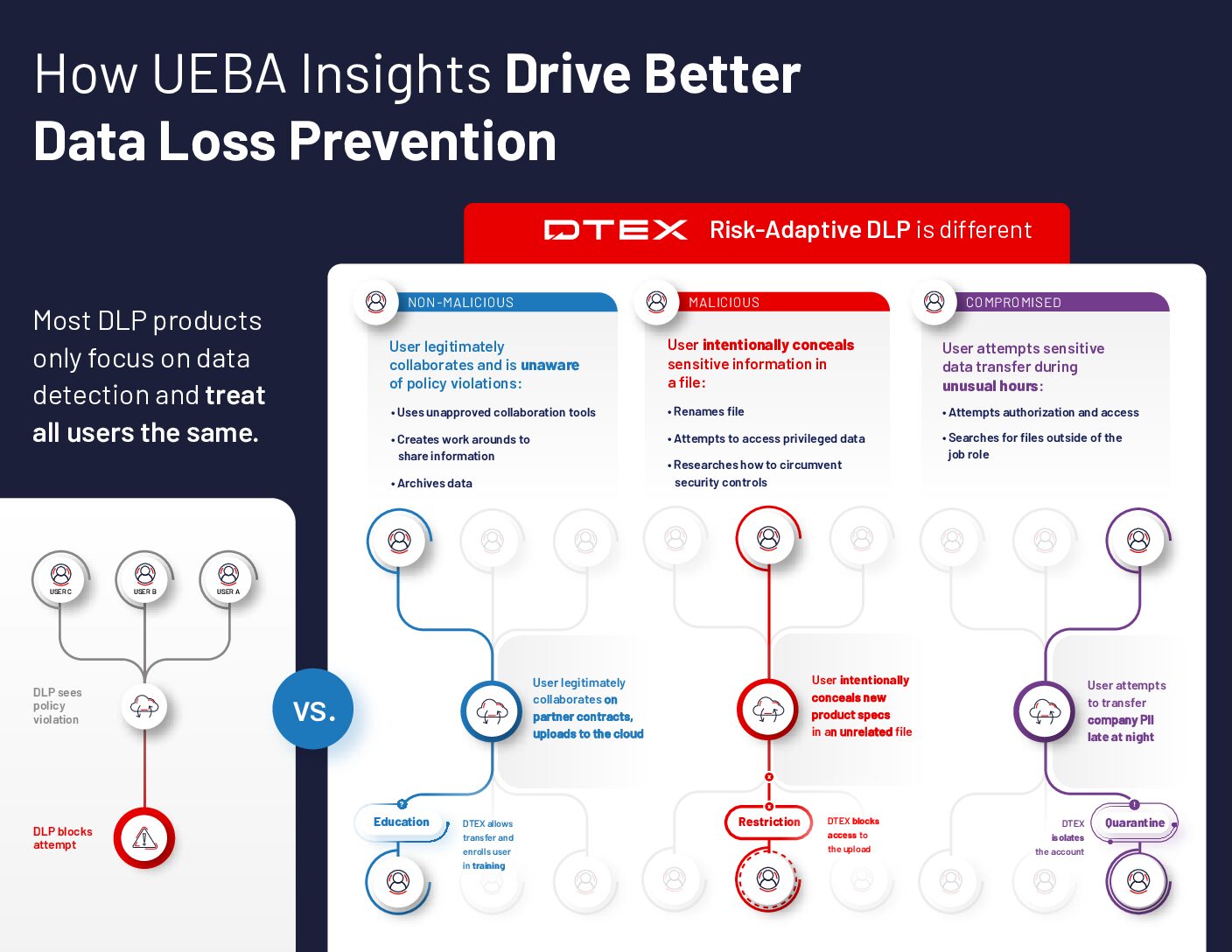
The behaviors leading up to a data exfiltration event are more important than the event itself in differentiating the types of insider risk and determining next steps.
Precision protection based on risk
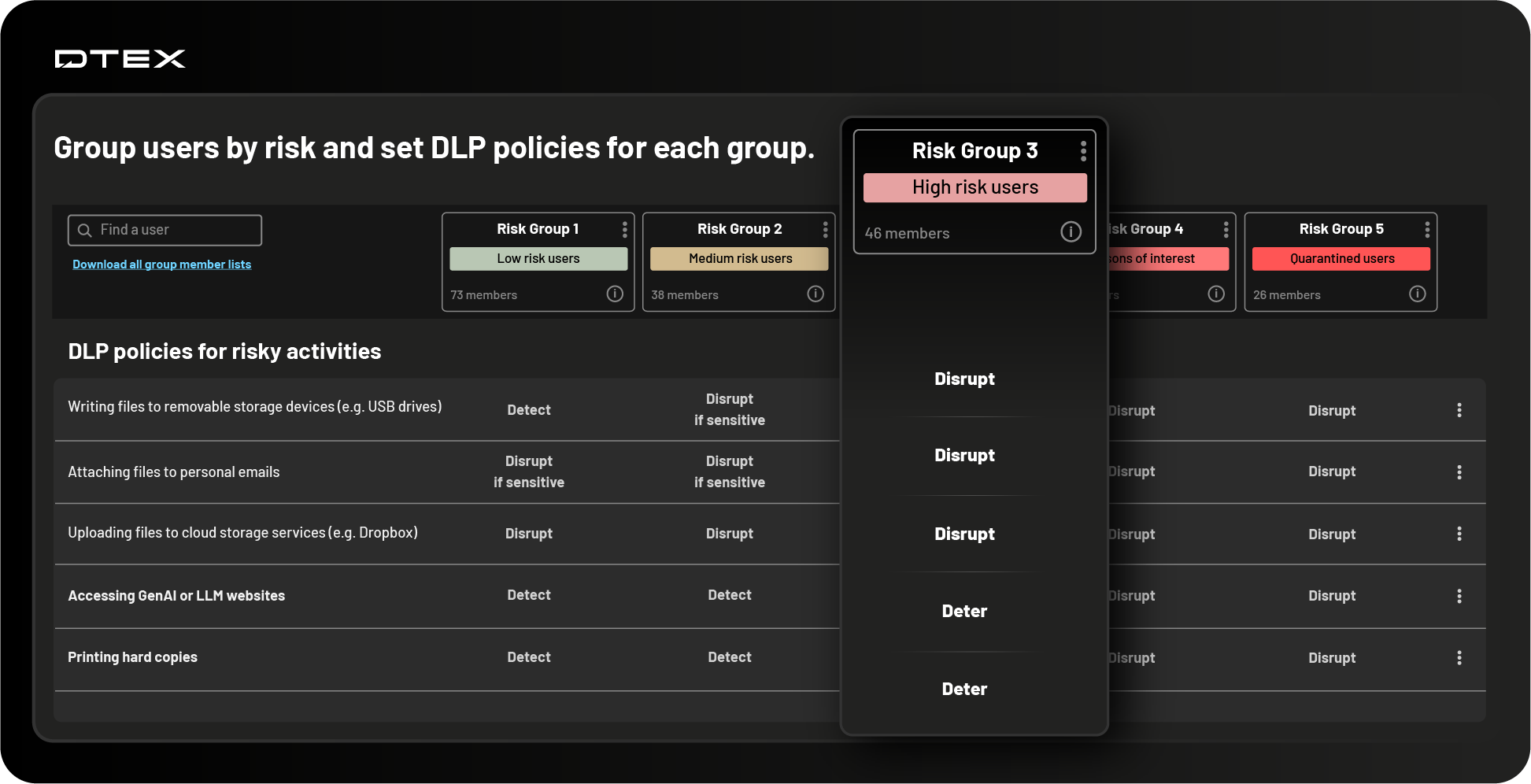
What is the DTEX Risk-Adaptive Framework™?
The DTEX Risk-Adaptive Framework™ instantly creates and automates data protection policies that adapt in real time.
Powered by dynamic risk groups, this unified system enables precision, automation, and proactive defense as user behavior and risks evolve.

Native content-based data classification
DTEX Content-Based Classification identifies and protects regulated data in real time through intelligent, on-device content inspection for business-critical data — driving behavior-based AI models to make it easier to identify and protect crown jewel information.

AI-driven, behavior-based classification
As an intelligent, lightweight approach, DTEX Behavior-Based Classification classifies data using AI-driven digital fingerprints, inferring sensitivity based on file attributes and behavior. And it applies to all file formats — videos, source code, and images — not just text, a first in the industry and groundbreaking for unstructured data.

Comprehensive AI security
DTEX redefines AI security with unmatched visibility and control over a full spectrum of generative AI tools and workflows.
DTEX tracks all usage, blocks generative AI prompt uploads of sensitive data, and monitors AI-generated content — even across unknown browsers, personal accounts, and non-browser utilities.
Fast-track data leak investigations
The DTEX AI risk assistant guides data leak investigations and empowers analysts with summarized user activity and next steps.
Without direct access to the internet, it synthesizes large amounts of information into digestible, context-rich, human-centric insights to help analysts make faster decisions.
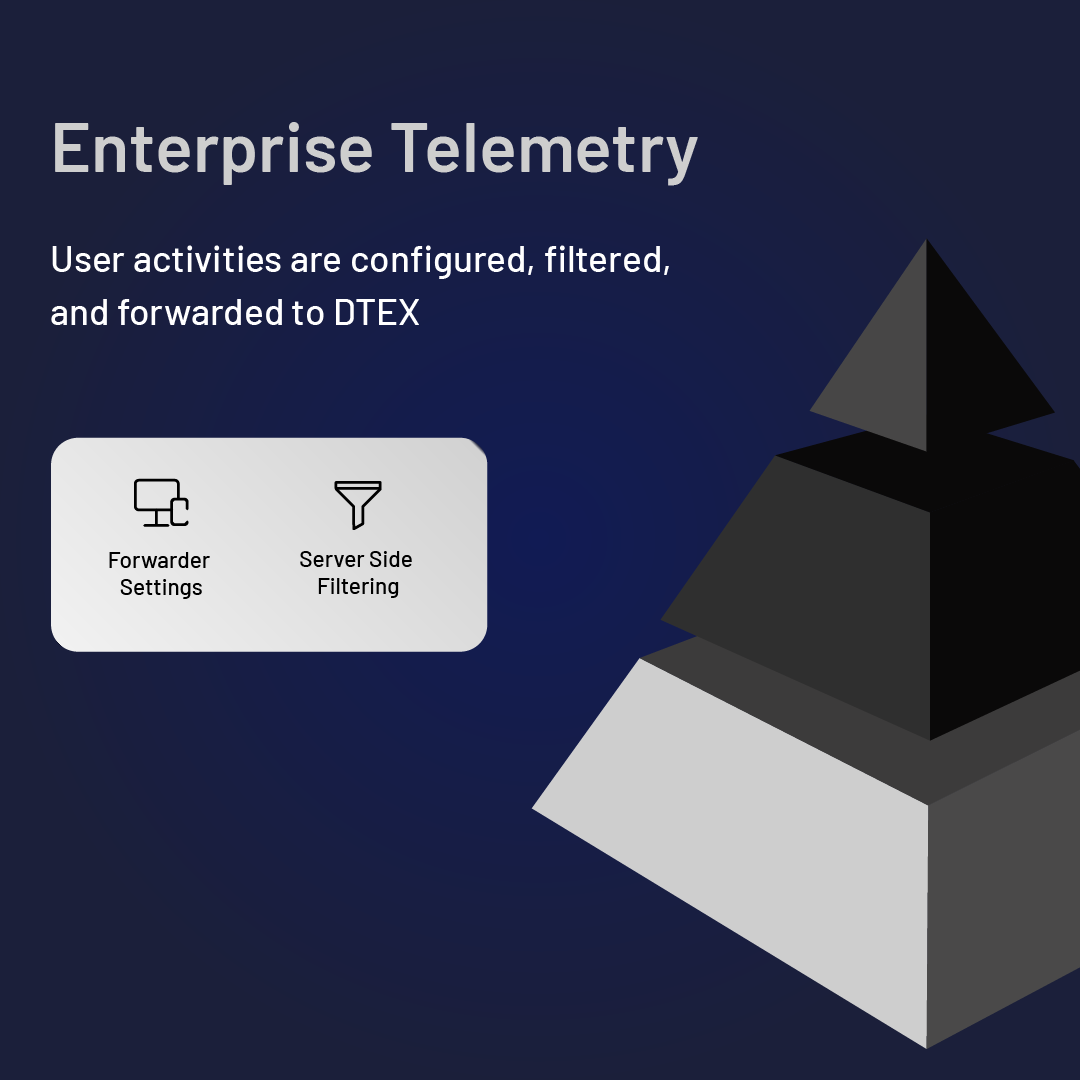
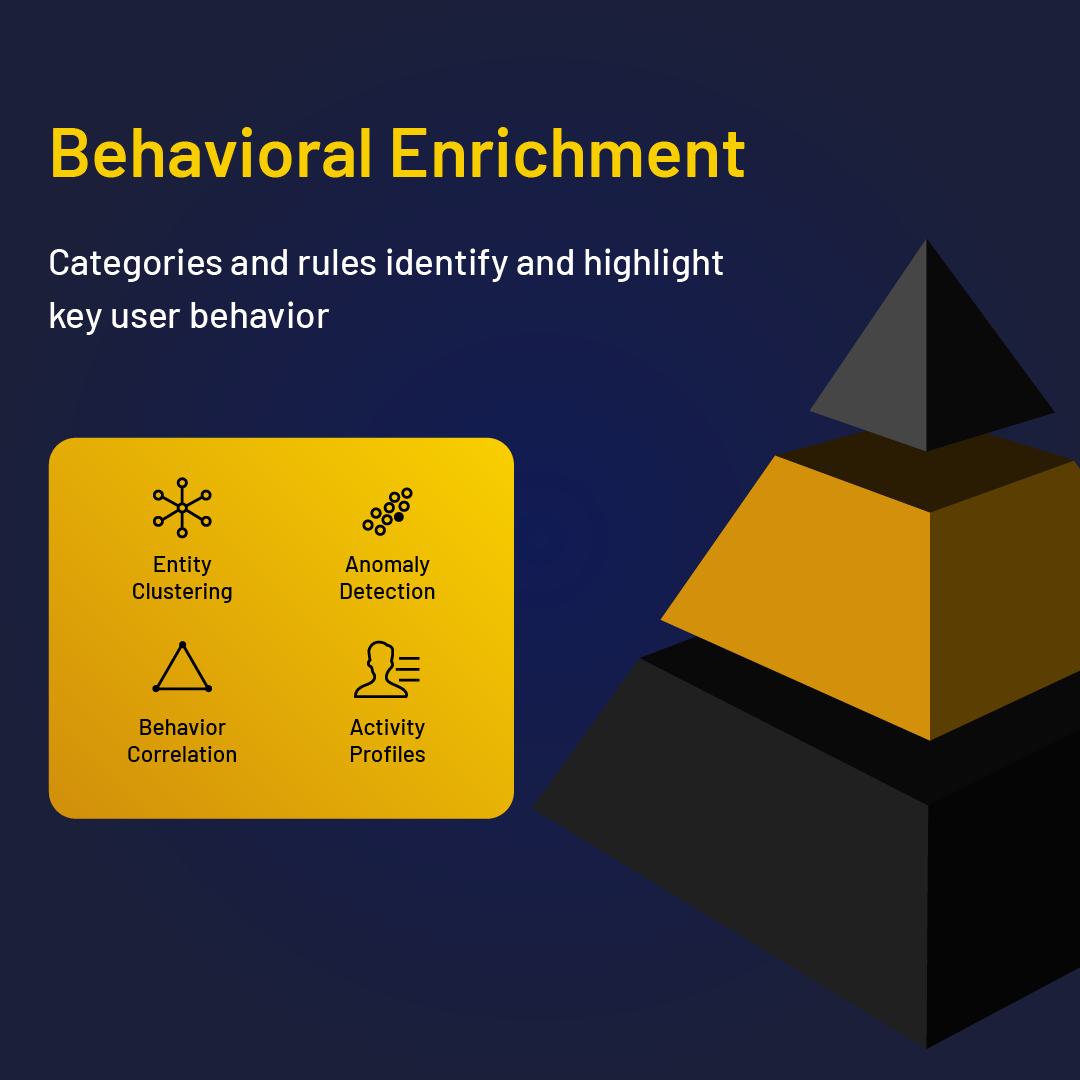
The power of the DTEX Platform