Tackle the most pressing insider use cases
Leavers and joiners
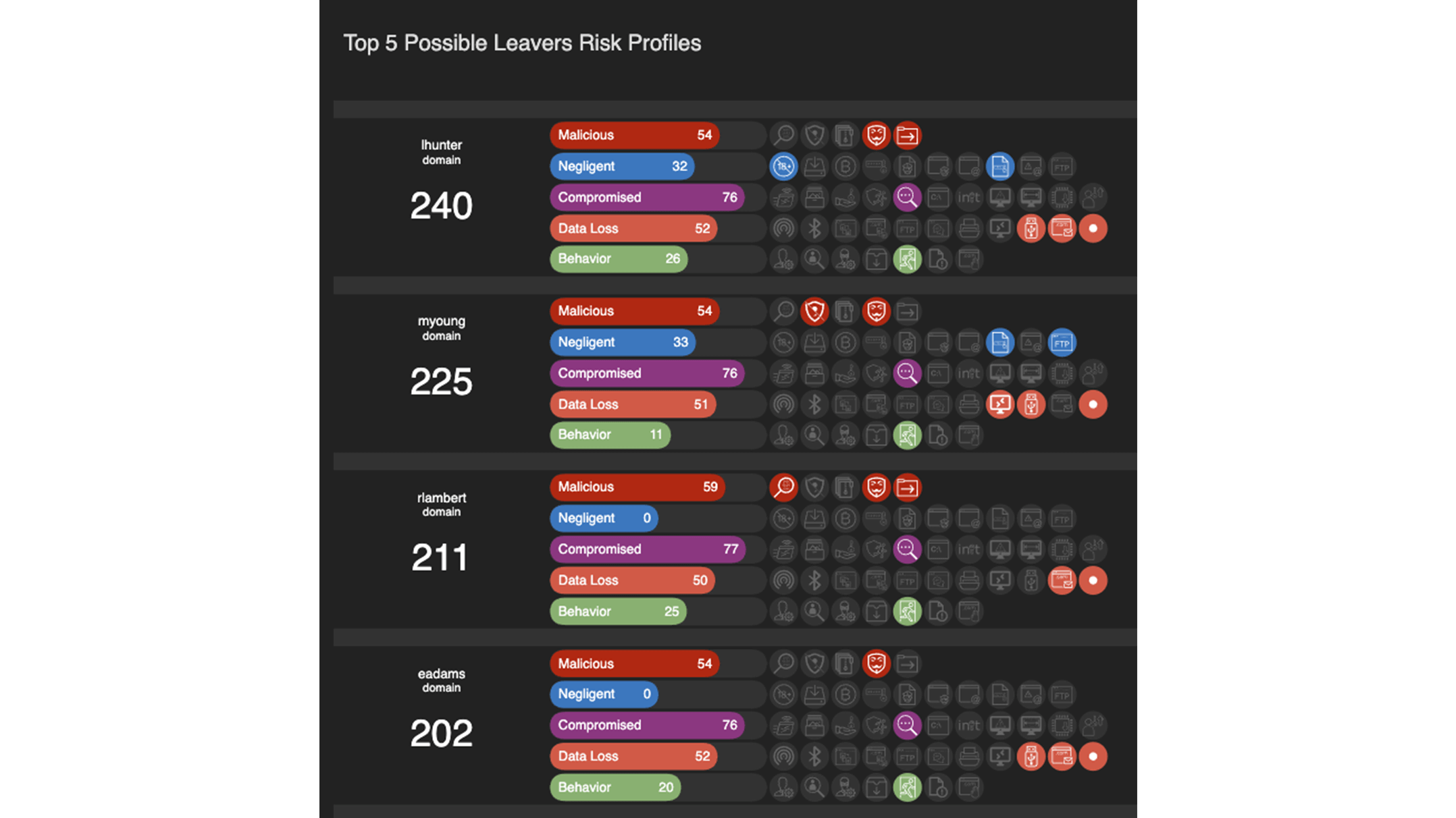
Third Party Risk

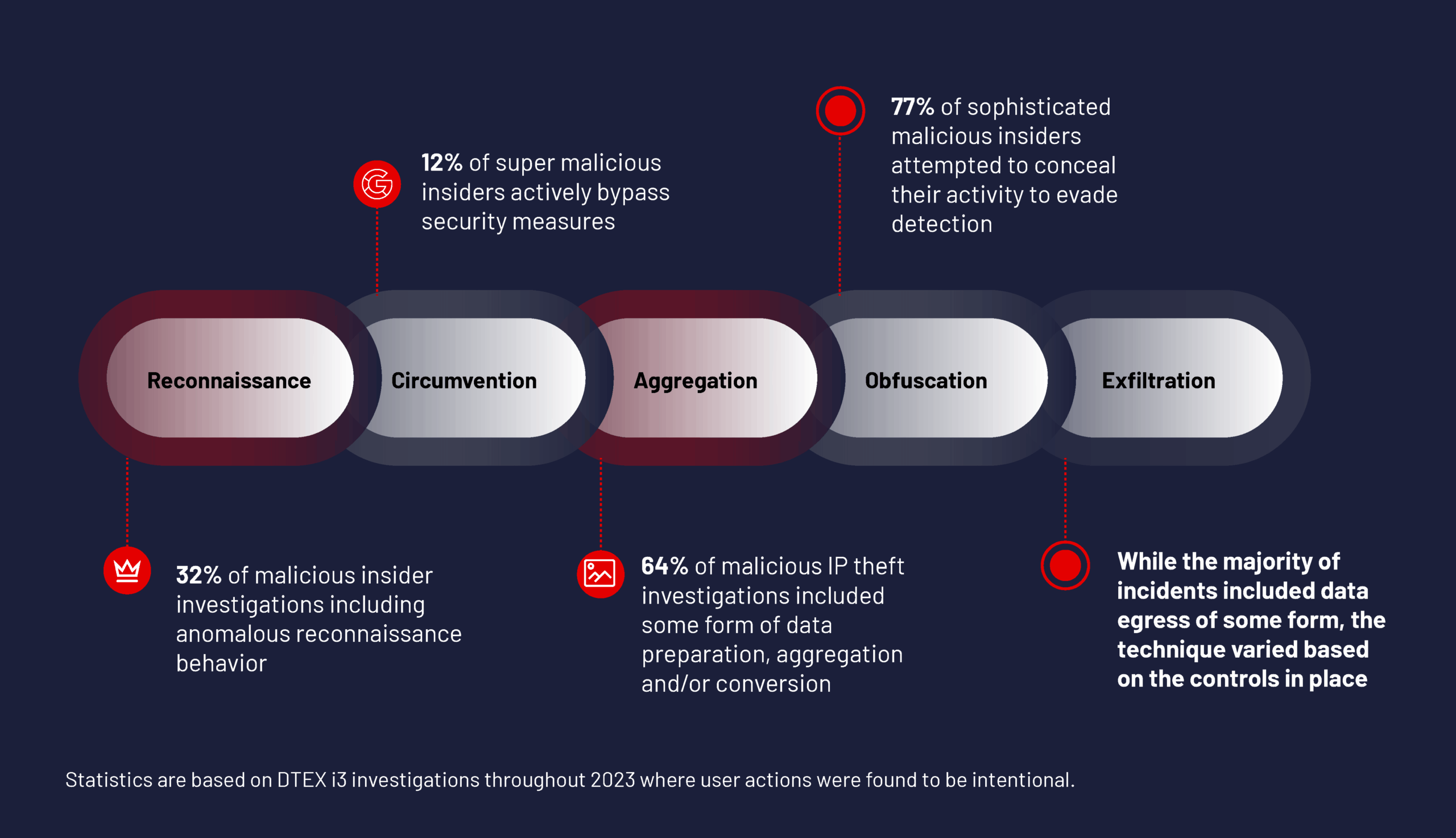
DTEX Insider Threat Kill Chain
IP theft is at an all-time high. The level of visibility into all stages of the Insider Threat Kill Chain is directly related to the ability to quickly and effectively identify, stop and investigate data loss attempts before exfiltration.
DTEX Insider Risk Management Capabilities

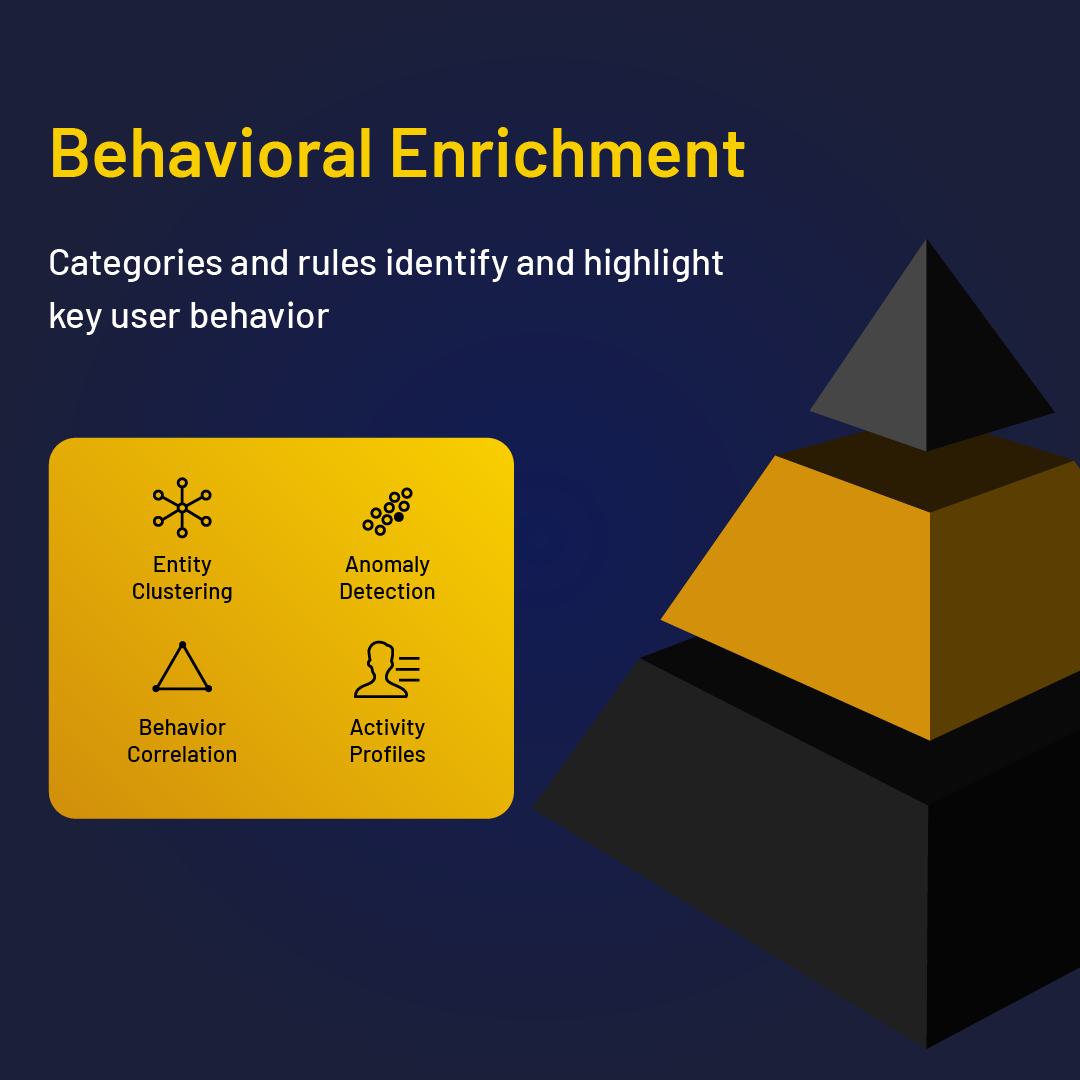
Behavioral indicators of risk
Unlike a typical malware attack, detecting insider threats effectively requires not only technical aptitude, but human investigative domain knowledge to pinpoint flight risk, overwork, system sabotage, or the precursors to data exfiltration.
DTEX IRM drives elevated indicators of risk that act as critical early warning signs of malicious or compromised behavior. Understanding those warning signs plays a big part in preventing an attack.

Threat hunting for malicious insiders
Sophisticated, insider threats often use low-and-slow techniques that bypass standard detection. Insider threat hunting adds a proactive layer to security operations.
With the industry’s richest insider risk dataset and open source query language, DTEX IRM enables analysts to dig deep into raw data and build instant, customized visualizations for quick decision making.

Fast-track risk investigations
DTEX Ai³ guides risk investigations and empowers analysts with summarized user activity and next steps.
Without direct access to the internet, it synthesizes large amounts of information into digestible, context-rich, human-centric insights to help analysts make faster decisions.
The Power of the DTEX Platform
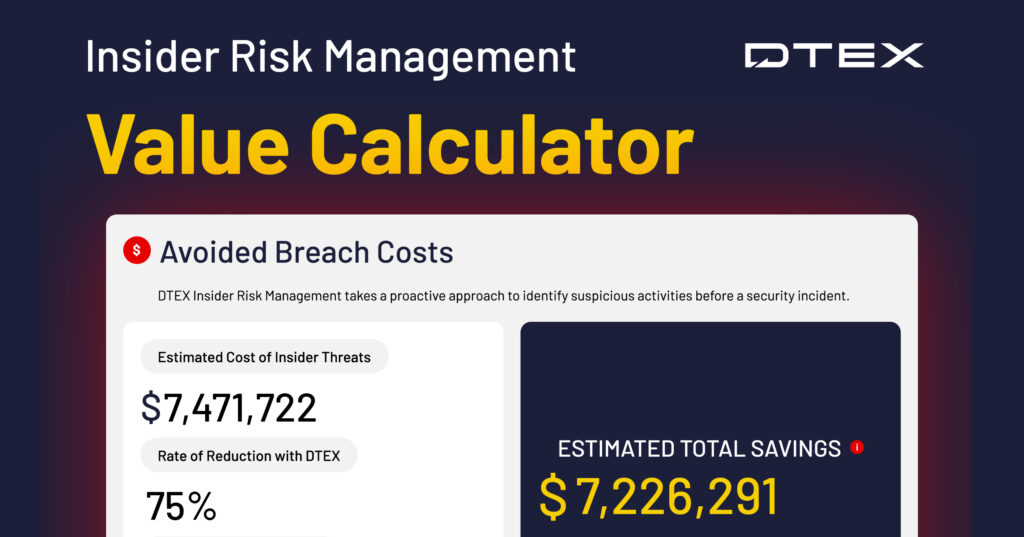
See thevalue of insider risk management
Determine the cost savings an insider risk management program could provide for your organization with our value calculator.