Last Updated: May 14, 2025
BACKGROUND
DTEX has issued an updated Insider Threat Advisory (iTA) based on recent i3 investigative findings. This update introduces new behavioral indicators related to the “DPRK RevGen: Domestic Enabler Initiative,” as previously reported by U.S. authorities1. The Democratic People’s Republic of Korea (DPRK) deploys skilled IT workers remotely to organizations globally funding its weapons of mass destruction (WMD) and missile programs, violating sanctions. In recent weeks, the techniques leveraged to evade detection have evolved, reducing reliance on traditional “laptop farms”. The threat has also expanded beyond the U.S. with active operations within Europe and other regions.
As part of this iTA we have a list of confirmed email IOCs associated with DPRK IT workers found below. Don’t forget to check HR and recruitment platforms alongside your cyber tools, to determine any existing employees or potential applicants associated with the known IOC emails list.
Key new Potential Risk Indicators (PRIs) identified include:
- Anomalous creation of and access to multiple online identities (personal email, freelance sites, banking/cryptocurrency etc.) for the potential purposes of recruitment, establishment of “sock-puppet” accounts, and further propagation of the initiative.
- Unusual system access patterns with a lack of protective factors2– characterized by a high volume of access at odd hours (often including use of anti-screen locking utilities) alongside minimal collaborative or recreational activity (e.g., lack of internal collaboration tools, internal emails, and personal device use).
- Unusual variance and frequency of banking and/or crypto sites while on a corporate device – access to banking sites often involves leveraging the local device identity to open multiple new accounts under identities unrelated to the employed identity.
- Malicious usage of live video streaming utilities – live video streaming tools (e.g., OBS and ManyCam) have been leveraged to connect multiple DPRK IT workers to individual company video conferences (thereby bypassing specific instances of multiple users as observed in the Chapman indictment3).
- Circumvention of zero-trust network access tools – Secure Access Service Edge (SASE) tools (e.g., Zscaler/Netskope) have been observed being disabled to create a more permissive environment for the usage of remote access tools.
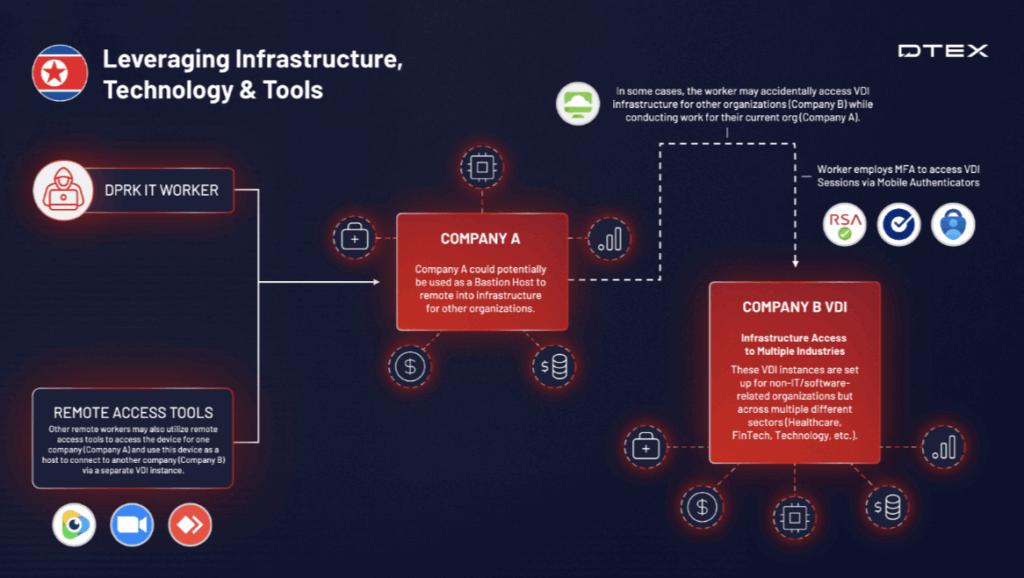
- Lateral movement between companies using VDI – using privileged access from one organization to break into and access another, often unrelated, organization. This has now been seen across multiple organizations, and we believe this is an intentional pivot in tactics, techniques, and procedures (TTPs) to avoid detection by more traditional indicators such as KVM switches and remote access tools.
These indicators should be used alongside existing cyber, recruitment, and psycho-social indicators and combined into an appropriate risk model as outlined in the advisory below.
INVESTIGATION BACKGROUND
On May 16, 2022, the U.S. Departments of State and Treasury, along with the Federal Bureau of Investigation, issued an advisory to alert the international community, private sector, and public about attempts by the Democratic People’s Republic of Korea (DPRK) and its IT workers to secure employment under false identities. This scheme aims to generate significant income for the DPRK, circumventing international sanctions.
Highly skilled DPRK IT workers exploit their expertise, recruit, or compromise non-DPRK individuals and entities, and leverage the global IT skills gap to gain employment for financial gain. North Korea’s history of cyber threats further complicates this issue. The advisory highlights the scheme’s primary economic motive, with some reports linking it to cyber incidents. The Justice Department has announced several indictments and provided updated indicators and details of the scheme.
- Recent FBI & DOJ Notifications:
- January 2025: Two North Korean Nationals and Three Facilitators Indicted
- December 2024: Fourteen North Korean Nationals Indicted
- August 2024: Justice Department Disrupts North Korean Remote IT Worker Fraud
- May 2024: Justice Department Announces Arrest, Premises Search, and Seizures
- October 2023: Justice Department Announces Court-Authorized Action to Disrupt
- Recent DTEX Partner Notifications:
- April 2025: DPRK IT Workers Expanding in Scope and Scale – Google Threat Intelligence Group (GTIG) further highlights the pervasiveness and spread of DPRK across the globe, identifying an increase of active operations in Europe and confirming the threat’s expansion beyond the United States. This growth is coupled with evolving tactics, such as intensified extortion campaigns and the move to conduct operations within corporate virtualized infrastructure.
POTENTIAL RISK INDICATORS (PRIs)
Risk Profile
New investigations have shed more light on the areas of DTEX’s risk profile which are more pertinent to the DPRK insider threat infiltration scenario (see figure below).
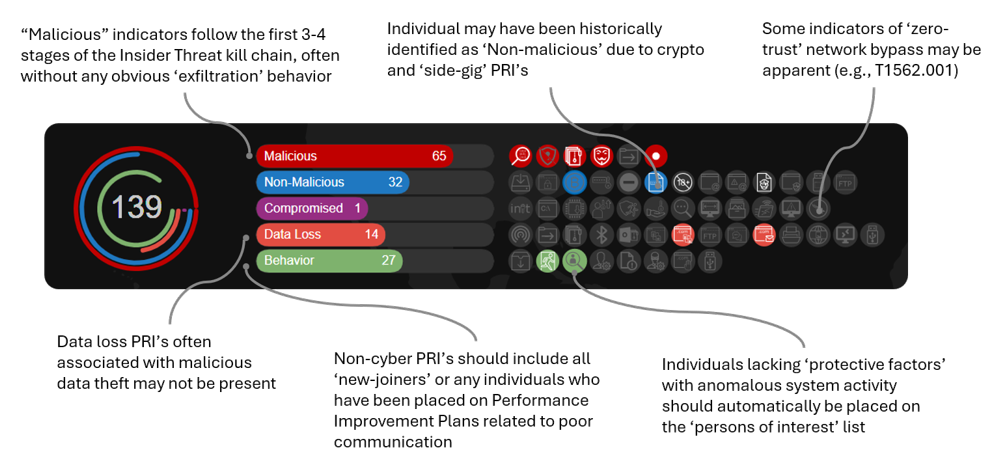
The PRIs that have been actively observed in DTEX’s customer environments have been broken down into individual risk areas below.
Malicious PRIs (Insider Threat Kill Chain)
The DTEX Insider Threat Kill Chain enables categorization for insider behaviors into the five areas seen below in Figure 3. In blended attacks, e.g., those involving external threat actors or nation states, this kill chain is useable with the traditional Cyber Kill Chain to effectively describe the incident. The main difference is that the Insider Threat Kill Chain does not prescribe any linear approach to the actions of the malicious insider due to their level of access into the organization.
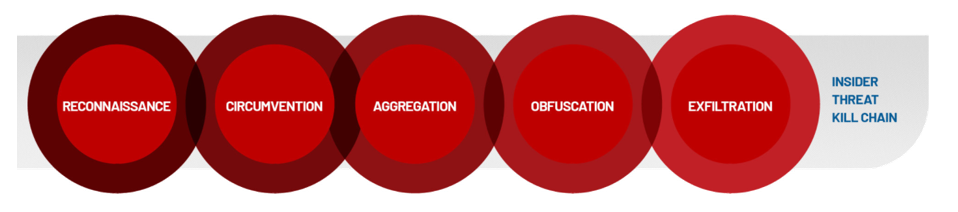
Newly identified PRIs that align to this kill chain are provided below.
Stage: Reconnaissance
Anomalous creation of and access to multiple online identities.
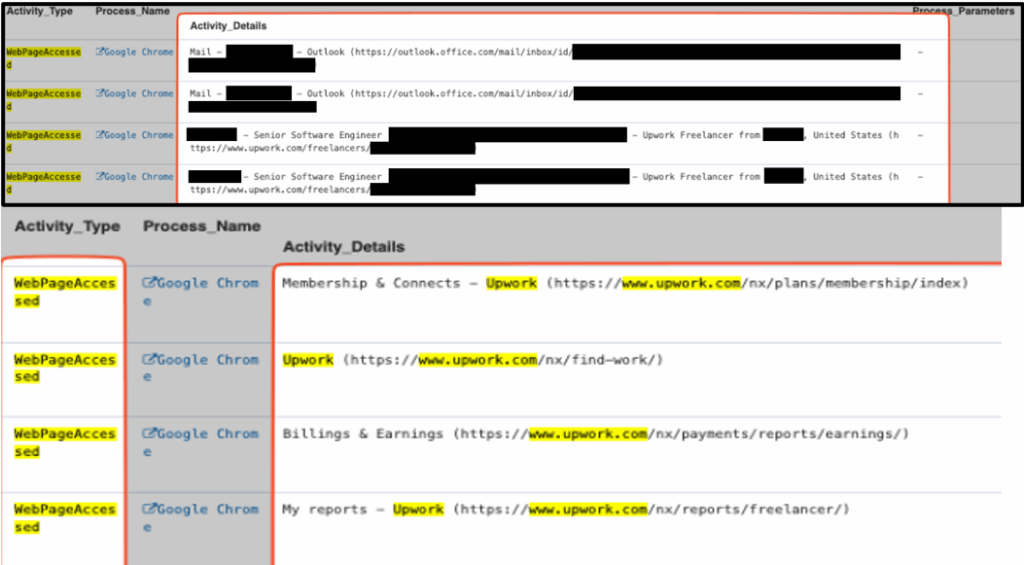
This appears as using multiple email, banking, crypto, freelance, or other online aliases other than the individuals name that was employed. For example, you may have hired an employee named Joe Smith but then the personal email they are using is [email protected]. This activity has ties into the DPRK operatives likely spreading their resources to:
- Bypass geolocation restrictions which have recently been introduced on specific freelance websites (e.g., www.upwork.com now actively restricts access to certain countries4)
- Work freelance jobs while they have a foothold in a U.S. based companies’ corporate laptop to further hide their geolocation.
- Communicate with other freelance accounts with similar skills and profiles, this may be reconnaissance activity for recruitment operations or simply to bolster the legitimacy of a sock puppet account.
- Allow multiple DRPK operatives to work concurrently on the one job, creating clear differences in behavior that can be observed.
While some of the multiple identities could be attributed to individuals having side jobs, being part of the overemployed movement5, or obfuscating their identity, it is the cumulation of the various web services that aligns closely with the DPRK RevGen initiative.
DTEX PRI Detection Approach:
Leverage DTEX’s “Multiple Identities” algorithm to surface unique account logins to web portals. The algorithm can then be used to actively alert when three (3) or more unique identities are present. In DPRK instances, more than four (4) unique accounts with diverse names are often observed.
RECALL: HIGH | PRECISION: MODERATE (see below)
Sample(s):
Stage: Reconnaissance
Unusual variance and frequency of banking and/or crypto sites while on a corporate device.
Access to banking sites often involves leveraging the local device identity to open multiple new accounts under identities unrelated to the employed identity. We have seen this activity occurring on corporate systems (rather than the IT worker’s own device) in order to circumvent geolocation and other security controls typically adopted by U.S. banks and other regulated entities.
DTEX PRI Detection Approach:
While access to bank accounts may be normal for employees, the sheer volume of “new” accounts being created by DPRK IT workers appear unique when compared against peers. This new PRI is specifically focused on bank account and crypto account ‘opening’ actions and alerts when volume is anomalous (greater than 3 standard deviations away from the norm). In practice, this is often more than five (5) new accounts in less than 60 days.
RECALL: MODERATE | PRECISION: MODERATE (see below)
Sample(s):
Stage: Circumvention
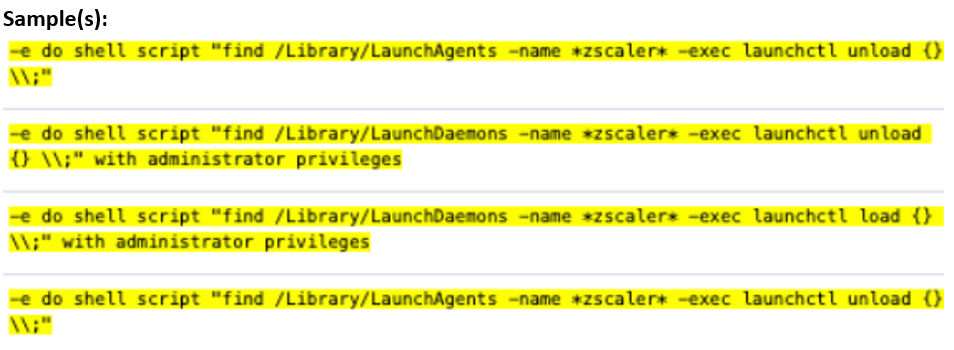
Circumvention of zero-trust network access tools.
Secure Access Service Edge (SASE) tools (e.g., Zscaler and Netskope) have been observed being disabled to create a more permissive environment for the usage of remote access tools.
Disabling security tools is not exclusively associated with the DPRK; however, this behavior seems to be employed solely to facilitate the operatives’ tasks. Aside from SASE tools, our investigation has not identified advanced techniques for disabling Endpoint Detection and Response (EDR) or Antivirus (AV) systems, as the operatives appear to achieve their objectives using legitimate Commercial Off-The-Shelf (COTS) applications.
DTEX PRI Detection Approach:
Leverage MITRE ATT&CK “Persistence” and “Defense Evasion” techniques for proactive detection. Pay specific attention to ID T1562.001 (https://attack.mitre.org/techniques/T1562/001/).
Pay close attention to macOS environments as detection methods are often less evolved and DPRK IT workers are far more likely to be offered this operating system based on software developer job specifications.
RECALL: LOW | PRECISION: HIGH (see below)
Sample(s):
Stage: Circumvention
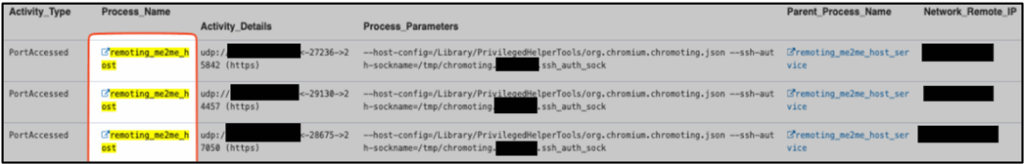
Unmonitored remote access tools favored.
A high number and large volume of remote access tools are in use, all of which can be considered Commercial Off-The-Shelf (COTS) applications. This includes corporate approved video conferencing applications such as Zoom and WebEx, which can function as remote access tools through their screen sharing and control capabilities.
Generally, the use of these tools provides mechanisms to record the screen external to the corporate device and may be leverage for clandestine data exfiltration. The added benefit of certain tools is the prevention of the endpoint entering a screen-lock if there is an active session in one of the video conferencing tools.
Importantly, the use of several remote access tools concurrently on the same device is common and has been attributed to the need for multiple DPRK workers on the same device at the same time.
DTEX PRI Detection Approach:
While the use of 2-3 of these applications may be common for the majority of employees, e.g., Zoom, Teams, and WebEx, it may be less common for 4+ of these applications on a single endpoint unless there was a very specific job role that required this.
The other behavioral indicator could be the long hours of usage, multiple applications in used at the same time, and frequency of usage one after the other.
In some investigations focused observation has been utilized to capture Zoom sessions with unknown participants. The organizations have reasonable suspicion to implement this under the guidance of their legal departments.
RECALL: HIGH | PRECISION: MODERATE (see below)
Sample(s):
Stage: Circumvention
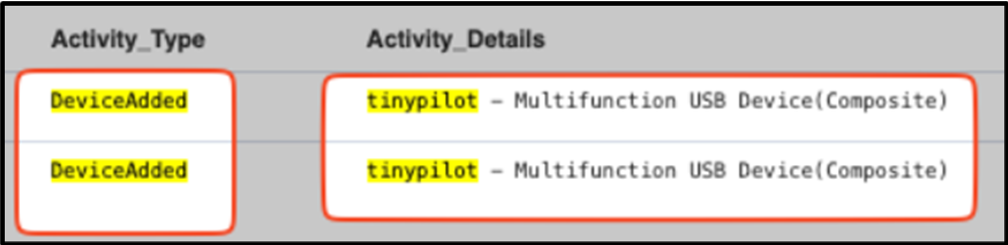
Keyboard, Video, Mouse (KVM) over IP devices confirmed in use.
TinyPilot, a simple plug-and-play KVM, has been confirmed to be used in the majority of incidents we are currently monitoring. While USB device insertions can often masquerade as a composite device, the configuration of such tools can readily be detected and result in fewer false positives.
This is currently a strong indicator of DPRK activity, although this could be expected to change as tactics and techniques progress over time to either other commercial KVMs like PiKVM or even to an enterprise grade solution.
DTEX is aware of other remote access mechanisms that do not require the use of KVM tools. Although we have not observed these alternative techniques in the wild, they cannot be ruled out and underscore the importance of reviewing other behavioral indicators holistically.
DTEX PRI Detection Approach:
Monitor for the initial introduction of removable devices, as investigated laptop farm administrators have been less technical and did not configure the device before connecting it, thereby revealing the default name for the KVM. Over time we suspect that more sophisticated approaches will evolve given the KVM over IP approach is already publicly documents. Additionally, there is an opportunity to detect the device configuration through both SSH sessions and a web UI if the device insertion indicators are missed.
RECALL: HIGH | PRECISION:HIGH (see below)
Sample(s):
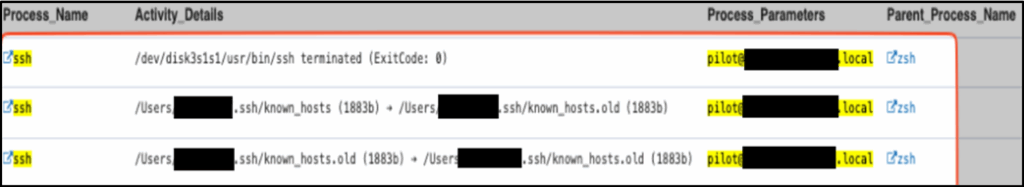
Stage: Circumvention
Anti-screen locking utilities observed.
Throughout the investigations, anti-screen locking applications were observed being downloaded to monitored endpoints (note that indicators should focus on the presence of the application not necessarily the usage of such applications given they were often used sparingly); this could be attributed to the high utilization of remote access and video conferencing tools on the endpoints, which inherently prevent the screen from locking.
This could be considered a supporting indicator if the endpoint was not being used frequently and the DPRK IT worker was attempting to appear more “normal” as tactics continue to evolve.
DTEX PRI Detection Approach:
Pay close attention to not just the usage but also the installers being introduced into the environment. Within reporting there is evidence of “caffeine.exe” which has been seen in our own investigations along with macOS specific tools like “owly”.
DTEX provides several existing indicators for this type of productivity masking tools, such as mouse jigglers. However, in the DPRK RevGen scheme, actual productive work remains high. To reduce PRI false positives, look for anomalous usage of such tools in conjunction with high volumes of system access.
RECALL: MODERATE | PRECISION: MODERATE (see below)
Sample(s):
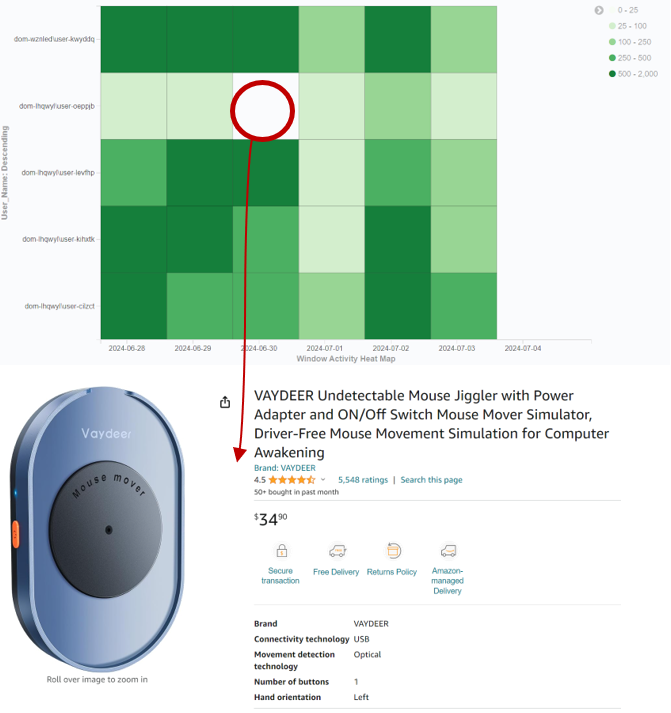
Stage: Aggregation
Text files with passwords on the Desktop.
Text files, with authentication secrets, are often saved to the endpoint in a common folder or directly on the desktop for sharing/handover between DPRK IT resources. This behavior may be attributed to multiple DPRK IT workers managing multiple jobs, where saving the necessary credentials facilitates easier handover or transfer of work.
DTEX PRI Detection Approach:
Monitor for similar files being saved in common locations on endpoints such as the Desktop, Documents, or Downloads folders. The files could be simply accessed as a reference when there is a “shift change” for the DPRK IT workers, or the files could be utilized as a variable in a script (e.g., scripts for disabling SASE controls).
RECALL: LOW | PRECISION: MODERATE (see below)
Sample(s):
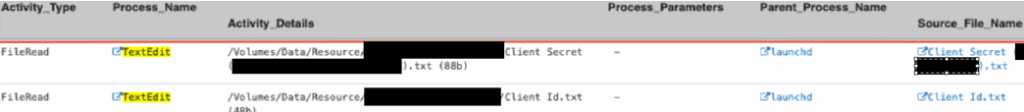
Stage: Obfuscation
Hiding in video calls with additional software.
Malicious use of live video streaming tools, such as OBS and ManyCam (https://manycam.com/), has been observed to connect multiple DPRK IT workers to company video conferences. This tactic can be employed during interviews or regular work calls, allowing a freelance worker to appear on camera while the DPRK IT worker controls the device. This method enhances anonymity and obfuscates identities, similar to concerns raised in the Chapman Indictment. Additionally, screen recording and audio/video manipulation tools support remote access and may assist with language translation and recording.
DTEX PRI Detection Approach:
When monitoring the usage of remote access and video conferencing tools, also monitoring the use of supporting applications simultaneously. Depending on the level of monitoring within an environment it may be possible to observe the process interactions and determine the purpose and use of the supporting tool.
RECALL: MODERATE | PRECISION: HIGH (see below)
Sample(s):
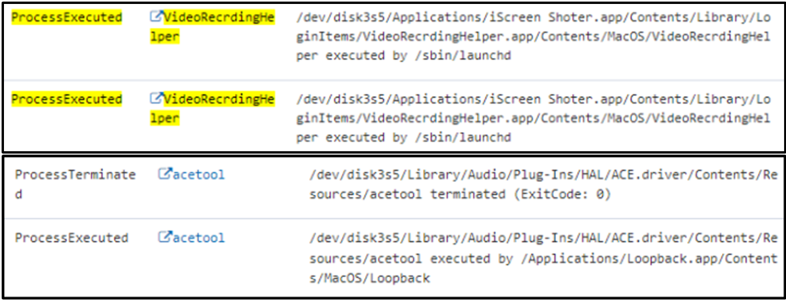
Stage: Obfuscation
VDI is used to lateral move into other organizations.
Lateral movement between companies using VDI has been observed, where privileged access from one organization is used to infiltrate another. This often involves VDI web-based applications like VMware Horizon and Citrix XenDesktop. This highlights the risk for organizations relying solely on secure VDI infrastructure, especially those employing third-party workers. Evidence shows DPRK IT workers accessing other organizations from a compromised entity, underscoring the inadequacy of VDI security alone to mitigate such risks.
DTEX PRI Detection Approach:
Organizations that provide third-party access via VDI should be aware of the behavioral indicators across this campaign and apply those human based monitoring patterns to each person accessing company material within the VDI environment.
If a corporate device has been issued to remote workers, identify any VDI access which is anomalous and not corporate sanctioned tools.
RECALL: LOW | PRECISION:MODERATE (see below)
Sample(s):
Stage: Exfiltration
Common-off-the-shelf file sharing facilitates exfiltration.
Current observations indicate that DPRK IT workers prioritize introducing files into environments and setting up collaboration and file-sharing tools to complete their tasks. While data exfiltration activities have been reported, DTEX’s current investigations indicate a lack of obvious data exfiltration indicators unique to this threat. However, given the nature of remote access, we cannot rule out the use of screen recording tools on the remote device to steal sensitive information.
DTEX PRI Detection Approach:
Continue to monitor for reconnaissance, aggregation, and exfiltration of data within the organization. The initial detection of this could help prevent significant data loss and potentially short circuit a devastating ransomware attack.
RECALL: LOW | PRECISION: LOW (see below)
Behavioral PRIs (Non-Cyber Indicators)
Performance Concerns
Pay close attention to individuals who have been placed on performance improvement plans (PIP), particularly early in their employment; in particular, individuals who have been escalated to HR due to factors such as poor communication to managers and peers, not being on camera, or lack of involvement during meetings. DTEX has observed that behavior of DPRK IT workers can change once a performance concern is raised, hence it is important to ensure that HR data is integrated into the DTEX platform to allow for correlation with any pertinent cyber indicators.
In addition, individuals flagged for performance issues should be added to the persons of interest list.
RECALL: MODERATE | PRECISION: LOW (see below)
Lack of Protective Factors
Unusual system access patterns with a lack of ‘protective factors’ is characterized by a high volume of access at odd hours (often including use of anti-screen locking utilities) alongside minimal collaborative or recreational activity (e.g., lack of internal collaboration tools, internal emails, and personal device use).
Low levels of organic – “normal” communication through work email and company instant messaging. There is a significant amount of activity on the user’s endpoint which includes completing tasks but there is a noticeable lack of proportionate email and instant messaging communication especially for a new employee. This is likely because they are trying to reduce the amount of interaction which could cause detection through either calls or written words which may have spelling and grammar errors due to language barriers.
DPRK operatives exhibit high volume usage of remote access/video conferencing software to both circumvent monitoring and have remote access. This activity would stand out to be well above the average. The uptime or logged in time for the devices are observed to be higher than normal.
RECALL: HIGH | PRECISION: MODERATE (see below)
Excessive Working Hours with Excessive Work Activity
DPRK will continue to advance their methods to avoid detection, although it will be challenging for them to completely change their established workflows. The periodic use of new tools for remote access, anti-screen locking, deepfakes, and multi-device controls can lead to reactive detection when only cyber indicators are deployed. A strong countermeasure for detecting tool evolution is through anomalous user behavior indicators; specifically, behaviors of individuals exhibiting both extensive working hours and overall heightened work activity when compared to peers.
DTEX PRI Detection Approach:
Each time a DPRK IT worker cohort is locked out of their session (VDI or physical laptop), contact with their handler is often required (e.g., U.S. citizen operating laptop farm) which carries additional risk of detection for the IT worker. Hence, DTEX advises monitoring unusual and erratic sessions and work activity among remote employees. Indicators such as prolonged working hours over several days or weeks, along with irregular working patterns, may signal potential issues.
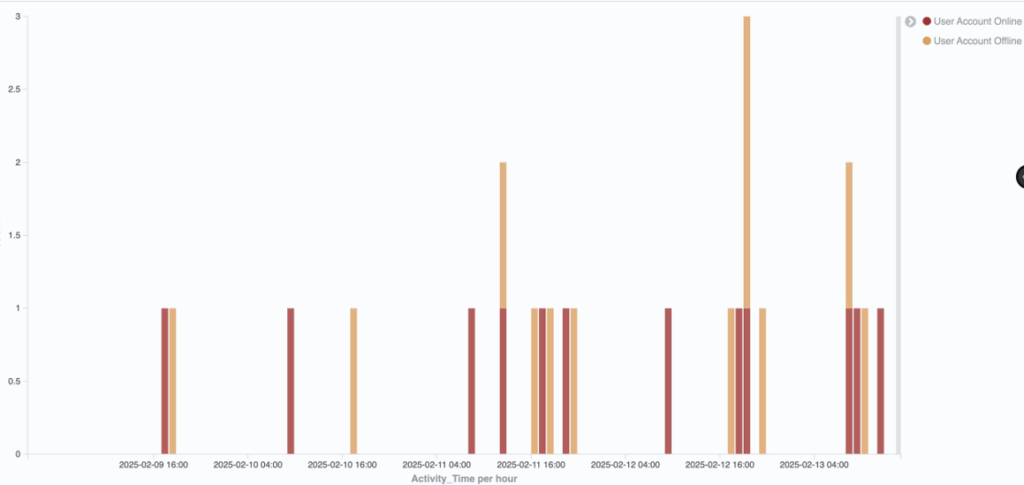
Excessive Working Hours:
The example on the left illustrates a typical employee’s logon/logoff activity within DTEX over a week, displaying regular working patterns with daily logon and logoff times, excluding weekends. Normal behavior includes breaks for personal needs such as restroom use, meal consumption, and sleep. On the right, DTEX observed session activity of known DPRK employees, where the intervals between logon and logoff ranged from 1 to 23 days.
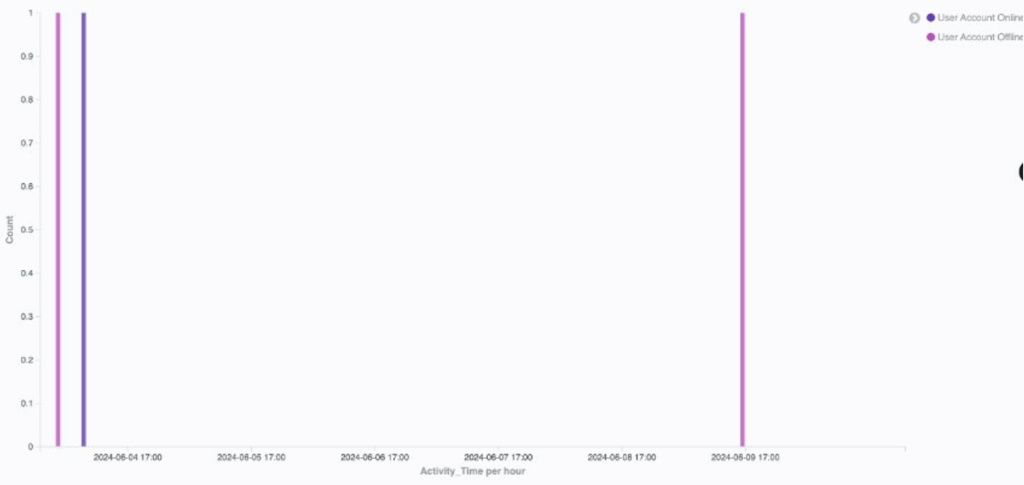
Excessive working activity:
On the left is an example of a normal employee within DTEX for a day’s period, and on the right, we can see the consistently erratic work activity of a known DPRK employee. Importantly, the volume of work activity would be deemed impossible for a single individual.
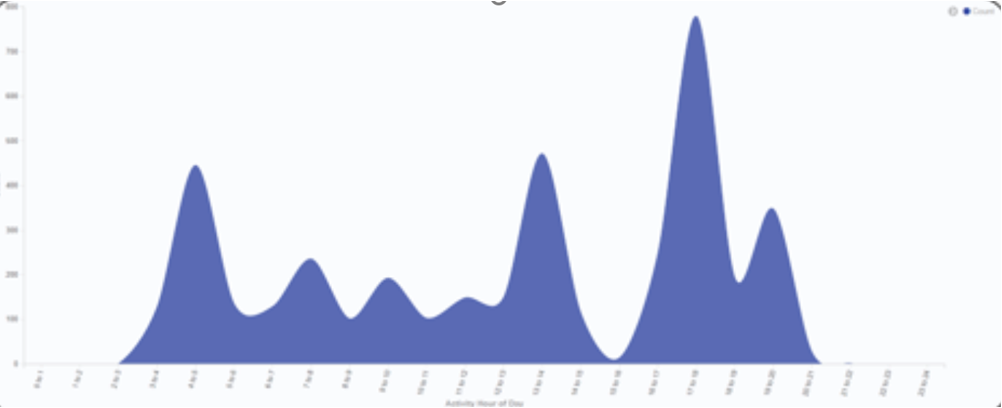
RECALL: HIGH | PRECISION: HIGH (see below)
New Joiners
All PRIs should also be correlated with individuals with “new joiner” status. This has been shown to reduce false positive rates and increase proactive detection.
RECALL: HIGH | PRECISION: HIGH (see below)
Recall and Precision
Both values are assessed once investigations have been completed and may shift and change over time with changes in insiders’ behavior. Indicators are expected to be leveraged in conjunction with other indicators to achieve the desired RECALL and PRECISION detection fidelity.
RECALL is the ratio of true positive predictions to the total number of actual positive instances in the dataset. It measures the indicator’s ability to identify all relevant instances.
PRECISION is the ratio of true positive predictions to the total number of positive predictions made by the indicator. It measures the accuracy of the positive predictions.
| RATING | RECALL | PRECISION |
| LOW | An indicator detects a lower percentage of the target behavior. | An indicator detects a higher percentage of false positives. |
| MODERATE | An indicator on average will detect the target behavior. | An indicator detects a balance of true and false positives. |
| HIGH | An indicator detects a high percentage of the target behavior. | An indicator will mostly detect true positives. |
Additional Tactics Confirmed
In addition to the PRIs outlined in the sections above, we have also observed the following tactics:
- Home country broker fronting interviews and attending remote meetings.
- Fraudulent or manipulated credentials to gain employment.
- Exploitation of weak background check processes for remote roles.
- Server farms and proxy services engaged in the home country appear as workers present in that region.
- Multiple workers logging in to service one role.
The following are some technical indicators we’re starting to see in common across the investigations:
- Infiltrator Demographic: Fluent English-speaking international citizens (typically not FVEY or North Korean citizens who are applying for technical jobs at FVEY entities).
- Identity Fraud: e.g., suspect secured employment at CUSTOMER and established a third-party business using at least one impersonated identity, indicating deliberate deception.
- High Level of Technical Proficiency: Active research into technical topics outside of job scope, e.g., NDI integration in ManyCam and tools such as TinyPilot.
- Suspicious VDI Activity: e.g., a user accessed the VDI environment of a third-party medical technology entity to emulate an employee of that entity.
- Anomalous Search Patterns: e.g., focused interest in online payment platforms and specific technology tools related to North Korea and China. Notably absent are common searches such as local news, shopping, or navigation, which may indicate an effort to obscure their geographical identity.
- Anomalous File Searches and Data Aggregation: e.g., searches for customer records outside of job scope and aggregation to network shares, local drives, cloud storage or USB.
- Testing of Security Controls: e.g.,creating innocuous text files, which are then exfiltrated via multiple channels.
- Anomalous Network Behavior: e.g., out-of-scope UDP communication with a known malicious remote hostname and access to a Gmail account linked to Belarussian or Russian identities.
- Unusual originating IP address geolocation of devices (but not necessarily out-of-country).
- Lack of internal collaboration and/or personal use of devices.
- Engagement with financial community advice sites.
Behavioral indicators should be used in collaboration with existing cyber, recruitment and psycho-social indicators that have proven effective in detecting participants in this scheme. For a further detailed brief on identified indicators and how to apply them in your environment please contact the DTEX i3 team or your DTEX representative.
RECOMMENDED ACTIONS
Immediate Priorities
- Audit Remote Access Policies and Onboarding Processes
- Restrict access to sensitive systems and data based on the principle of least privilege.
- Implement strong authentication and access monitoring for all remote workers.
- Require that a corporate laptop is provided and shipped to the address where the individual claims to live. Ensure that courier companies confirm photo ID upon delivery.
- Perform video onboarding with the camera enabled to confirm the visual appearance of the employee with the photo saved on file. Request that they confirm laptop serial number or asset tag whilst on call.
- Require the use of hardware-based MFA tokens for laptops.
- Strengthen Vetting and Onboarding
- Carefully review existing and potential remote workers’ resumes for inconsistencies. Resumes have been identified with mismatching eras of technology.
- Always interview with the camera on and preferably in person.
- Conduct enhanced background checks for all remote employees, including identity verification, technical skill verification and criminal history, with checks across jurisdictions.
- Collaborate with security-cleared recruitment firms for technical hiring.
- Follow up with detailed background checks/vetting. Don’t rely on email for reference checking.
- Check social media and employment profile pictures for modification with AI (open-source tools can assist).
- Review log sources from applications like Zoom when conducting the remote interview to determine if the remote worker matches any known indicators.
- Review requests for corporate device shipping to a location that deviates from original address. Potential excuses would include visiting a sick relative or a similar reason for being in a different location.
- Monitor for Insider Threat Indicators and Implement IT Controls
- Deploy insider threat detection tools to identify unusual data access patterns or behavior anomalies. These include:
- Unauthorized remote access tools
- Anomalous geolocation of endpoints
- Unauthorized mouse jigglers
- Data hoarding
- IP Address indicators of compromise (IOCs) in Zoom logs (review geolocation of IP’s and compare with known DPRK indicator addresses – including Mandiant provided IOCs6)
- Look for suspicious virtual backgrounds that may indicate a different working environment to that expected of a home employee (e.g. flashes of call centers in outlines of virtual backgrounds).
- Establish regular review processes for user activity logs, particularly for remote personnel.
- Whitelisting of applications – ensure that no unauthorized remote access tools or mouse jigglers can be installed. Alert on attempts to install.
- Monitor for IP based KVM devices and unapproved VPN services.
- Monitor for multiple logins from different IP addresses and abnormal file repository reconnaissance.
- Deploy insider threat detection tools to identify unusual data access patterns or behavior anomalies. These include:
Short-Term (0-6 Months)
- Review Contracts with Third-Party Providers
- Require security clauses in contracts mandating thorough vetting of subcontractors and consultants.
- Limit the use of offshore entities for roles involving sensitive work.
- Potentially perform extended vetting of third-party staff as part of onboarding process.
- Implement Threat Awareness Training and Cultural Changes
- Provide security awareness training for hiring managers and staff to recognize recruitment red flags.
- Encourage a culture of camera on for remote workers.
- Educate employees on social engineering tactics commonly used by adversaries.
- Enable Incident Response Mechanisms
- Test incident response plans for detecting and managing insider threats.
- Maintain a clear escalation process to report and respond to suspected infiltrations.
Long-Term (6-12 Months)
- Integrate Threat Intelligence
- Partner with national security agencies to receive updates on emerging threats and adversary tactics.
- Use threat intelligence to continuously refine vetting and monitoring processes.
- Enhance Security Technology Investments
- Upgrade identity and access management (IAM) systems to include continuous authentication capabilities.
- Invest in advanced monitoring solutions with behavioral analytics capabilities.
INVESTIGATION SUPPORT
For intelligence or investigations support, contact the DTEX i3 team. Extra attention should be taken when implementing behavioral indicators on large enterprise deployments.
APPENDICIES
Email IOCs
The following IOCs are not indicative of a North Korean attributed hack, but instead may have associations with IT worker operations. For that reason, these IOCs require further investigation if observed in your environment. These IOCs were passed to DTEX from third parties in connection with their observed IT worker operations, and not from clients unless dual sourced externally. Any connection to actual persons may be deliberate or incidental depending on North Korean tactics. The actual owner of the email accounts listed herein may be unaware of the IOC relating to their address.
Get Threat Advisory
Email Alerts






