- Enforcing Segregation of Duties (SoD) ensures no single individual has full control over critical systems or sensitive data, reducing the risk of privilege abuse by distributing responsibilities across system administration, data access, and security monitoring for greater accountability and oversight.
- Implementing Just-in-Time (JIT) privilege elevation limits administrative access to only when necessary and for a short duration, reducing the risk of misuse, while requiring detailed audit logs to ensure transparency and accountability for all elevated access events.
- Requiring multi-person approval for high-risk actions ensures no single individual can make critical changes — such as exporting sensitive data or disabling security tools — without oversight, enhancing accountability through documented workflows and audit trails.
- Monitoring and alerting on administrator behavior using behavioral analytics and real-time logging helps detect anomalies and potential misuse of privileges, enabling prompt investigation and response to safeguard sensitive systems and data.
INTRODUCTION
There is always a lot to stay on top of when assessing the evolving risk landscape organizations face year after year. At DTEX, one area we have been deeply focused on is profiling server use cases, a challenge that has proven to be highly contextual and complex. Server infrastructure varies significantly across organizations and industries, making a one-size-fits-all approach ineffective.
What we do know with certainty is this: servers are the prime target in both security incidents and data breaches. According to the 2025 Data Breach Investigations Report, servers consistently rank as the most impacted asset across nearly every industry vertical.
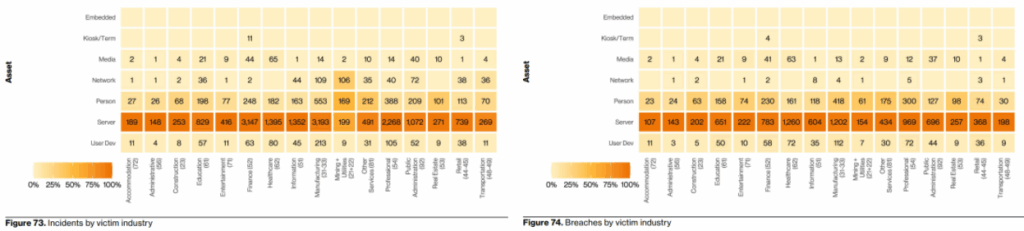
The data shows that in over 75% of incidents and breaches, servers were affected — an alarming trend that underscores the need for user monitoring on servers. Ignoring this threat vector is no longer viable, especially when insiders and external actors alike are actively targeting these systems.
This year, our iTA series has taken a deep dive into this issue:
- In iTA-25-01, we explored nation-state cyber espionage and how server compromise plays a central role.
- In iTA-25-03, we examined the risks posed by users with elevated privileges, highlighting how trusted insiders can become saboteurs.
DTEX INVESTIGATION AND INDICATORS
We released iTA-25-01 earlier this year. It focused on detecting living-off-the-land (LotL) techniques used by Chinese nation-state actors. This iTA uses Russian threat actors, Seashell Blizzard (Microsoft naming convention). We do this not to actively threat hunt across all customers for this threat actor, though it is a nice byproduct. It enables our defenders to start thinking about how to detect similar malicious insider behaviors.
First let’s dive into a high-level timeline of user activity from a documented breach.
Some parts of this Threat Advisory are classified as “limited distribution” and are accessible only to approved insider risk practitioners. To view the redacted information, please log in to the customer portal or contact the contact the i³ team.
Insider Threat Framework stage: circumvention | remote management and monitoring tools
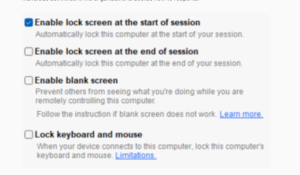

Insider Threat Framework stage: account compromise | credential access
If a threat actor has appropriate privileges, they can dump the LSASS process on Windows.

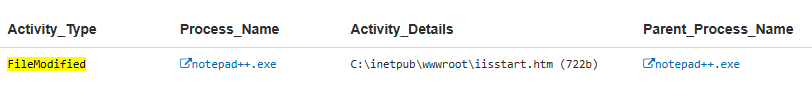
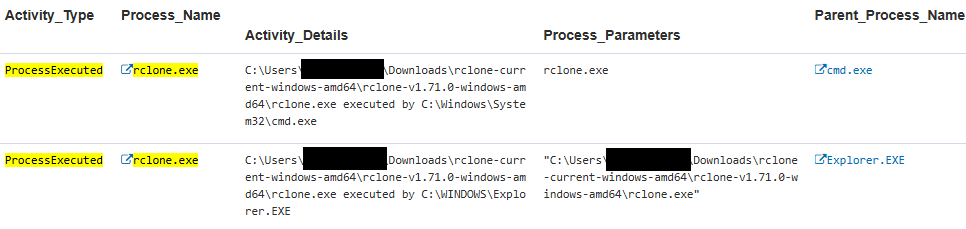
Insider Threat Framework stage: behavior | mass exfiltration via Rclone
- Compatible with over 40 cloud-based storage platforms.
- Single executable file requires no installation.
- Command-line operation allows for scripting and automation, enabling silent background execution.
- HTTPS communicates with cloud APIs, blending its traffic with legitimate encrypted web traffic.
- Encrypts files before uploading.
- With SYSTEM-level privileges, it interacts with sensitive files and directories inaccessible to regular users.
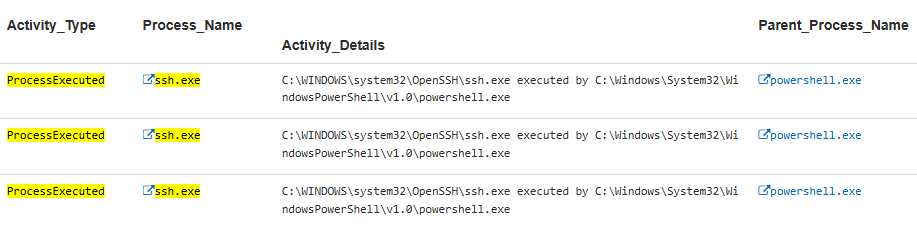
Insider Threat Framework stage: behavior | OpenSSH, additional access and persistence
OpenSSH is widely used in enterprise environments across Windows, MacOS, and Linux servers. This makes detection difficult without additional planning and contextual knowledge.
If you tightly control the number of users, you can detect when any other user accounts attempt to execute SSH.
Insider Threat Framework stage: behavior | file integrity monitoring
Like SSH, this requires context to create a detection. However, server files and directories may change little once in production.
For example, a web server’s pages are accessed but rarely modified unless upgrading the website.
Threat actors often drop webshells by modifying existing files or creating new ones in the web server’s file structure. Monitoring for such changes can uncover malicious activity.

DTEX forensic audit trail
Profiles and personas
Profile: server administrator
Role |
Devices |
Motivation |
Timing and opportunity |
|---|---|---|---|
|
|
|
|
Application usage |
There are no restrictions to what this user can install or use. They have advanced technical knowledge and will use legitimate tooling to achieve their goals. |
Persona
This persona helps organizations conceptualize and differentiate threat-hunting strategies. By separating these behavioral patterns, teams can proactively detect and respond to risks without technical emulation.
Malicious insider
The motivation is clear before the malicious activity. It is broad based on the individual’s position and access.
- Motivation: financial gain, IP theft, or disruption.
- Behavioral indicators: accessing unauthorized data, using applications in new ways, circumventing security controls, or covering tracks.
- Risks: data theft, reputational damage to the organization.
Recommended Actions
Early detection and mitigation
Enforce Segregation of Duties (SoD)
To reduce the risk of server administrators abusing their privileges, enforce segregation of duties (SoD). No single individual should have full control over critical systems or access to sensitive data. Separating responsibilities between system administration, data access, and security monitoring minimizes the likelihood of one person compromising or exfiltrating sensitive information without oversight. This approach creates natural checks and balances by distributing critical tasks, making it harder for any one person to conduct unauthorized activities undetected.
Segregating duties ensures different personnel perform roles like system administration, data access, and security monitoring. Each role has limited access to the organization’s infrastructure. This provides higher accountability, as each party has clear responsibilities. For example, system administrators manage infrastructure but lack direct access to sensitive data, while security teams monitor activities and data flows. Implementing SoD reduces the risk of collusion or privilege misuse, safeguarding sensitive information.
Implement Just-in-Time (JIT) privilege elevation
Just-In-Time (JIT) privilege elevation prevents server administrators from abusing administrative access. JIT grants administrative access only when necessary and for a limited time. This method ensures server administrators do not maintain persistent access to critical systems and data unless their duties explicitly require it. Limiting elevated privileges reduces opportunities for unauthorized actions and minimizes data exfiltration or compromise during non-administrative tasks.
JIT requires thorough documentation of all privilege elevation events and full audit trails for each instance. These logs capture the administrator’s identity, access duration, specific actions taken, and the approval process. This auditability provides transparency and enables the organization to track administrative activities. Suspicious or unauthorized privilege elevations are flagged and investigated, adding an extra layer of security for sensitive systems and data.
Require multi-person approval for high-risk actions
Implement multi-person approval for high-risk activities. This mitigates the risk of server administrators compromising system or data integrity. High-risk activities include:
- Exporting sensitive data
- Disabling security tools
- Modifying logging configurations
Requiring dual authorization or sign-off before these critical actions safeguards against unauthorized or malicious activities. This ensures no single individual can unilaterally make potentially harmful changes.
Workflow tools track and document these approvals, adding control. These tools notify, involve, and hold appropriate individuals accountable in the decision-making process. They also provide an automated record of who approved what and when, invaluable during investigations or audits. Enforcing multi-person approval for high-risk actions ensures sensitive decisions have proper oversight, reducing the likelihood of a breach or malicious data loss.
Monitor and alert on administrator behavior
Monitoring and alerting on administrator behavior detects and responds to potential risks from server administrators. Behavioral analytics tools detect anomalies in administrative activity that may indicate privilege misuse. For example, if an administrator accesses data transfer tools like rclone, scp, or PowerShell, or explores sensitive directories they do not normally access, flag these behaviors for investigation. Promptly alert the security team to anomalies in typical user behavior, such as accessing unusually large data volumes or actions outside standard operating procedures, for immediate review.
To monitor administrator behavior effectively, organizations should use integrated logging and alerting systems. These systems track all administrative actions and generate real-time notifications when they detect thresholds or suspicious activities. This allows the organization to respond quickly to potential threats and investigate unusual activities before they escalate. By leveraging behavioral analytics and setting up targeted alerts, the organization proactively detects and prevents malicious or unauthorized actions from server administrators.
Some parts of this Threat Advisory are classified as “limited distribution” and are accessible only to approved insider risk practitioners. To view the redacted information, please log in to the customer portal or contact the contact the i³ team.
INVESTIGATION SUPPORT
For intelligence or investigations support, contact the DTEX i3 team. Extra attention should be taken when implementing behavioral indicators on large enterprise deployments.
iTA references
Anthropic Threat Intelligence Report: August 2025
Additional material
Get Threat Advisory
Email Alerts






