Insider risk solutions for the most pressing use cases
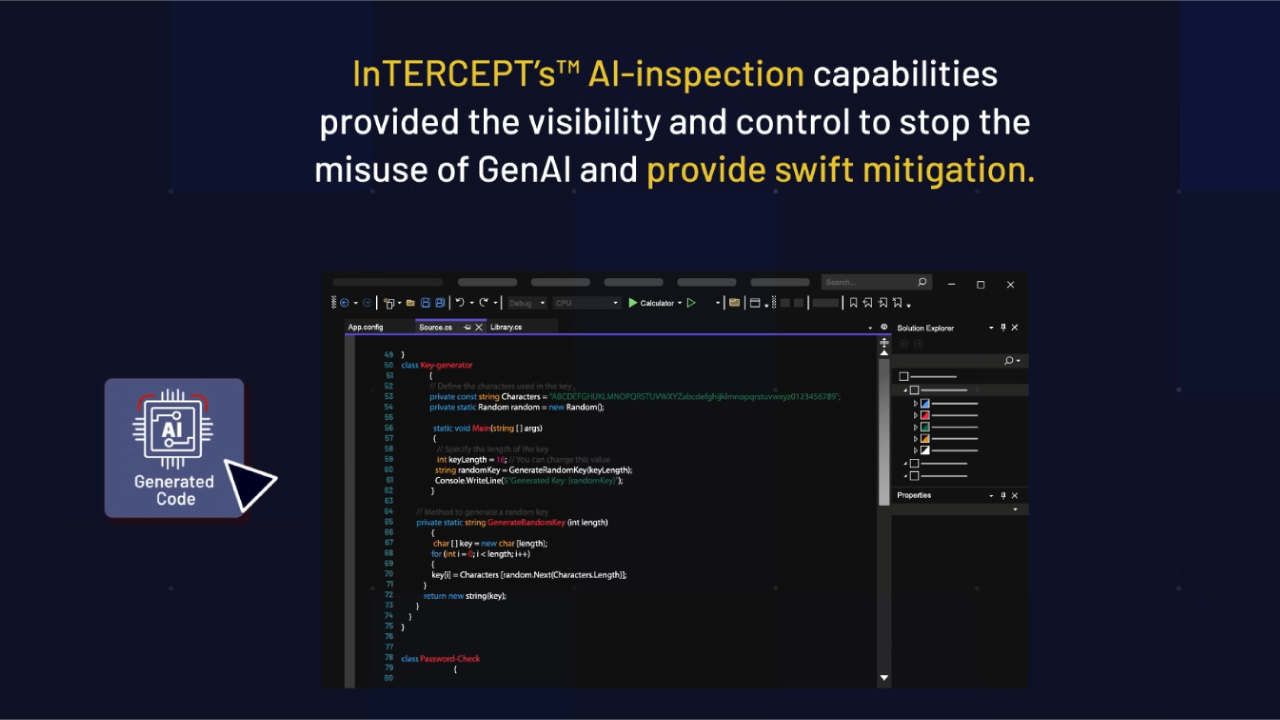
AI Misuse and Abuse
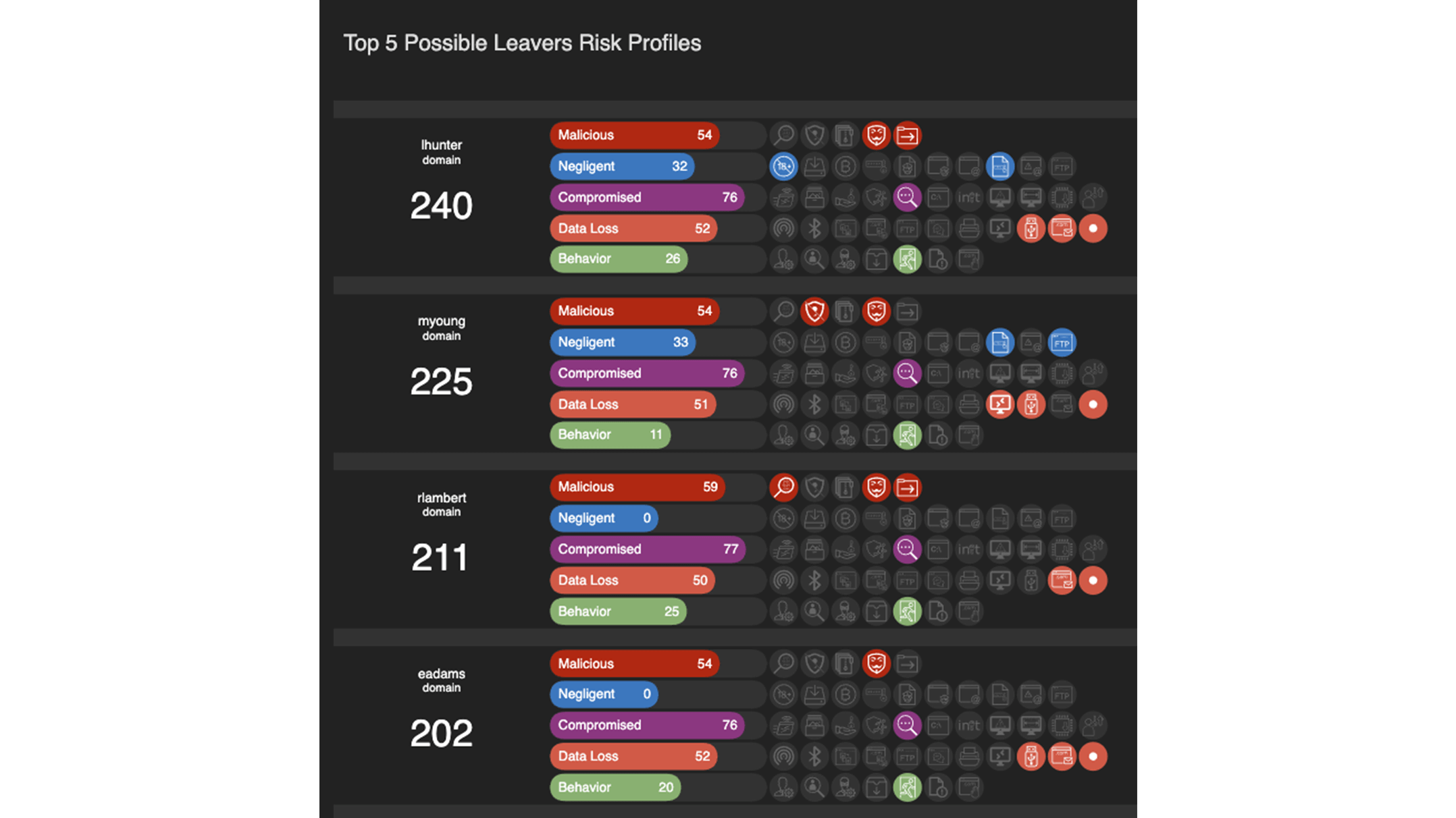
Leavers and Joiners
Fraud

Detect behaviors indicative of financially-motivated fraud.
Forensic Investigation

Support investigations with a complete forensic audit trail.
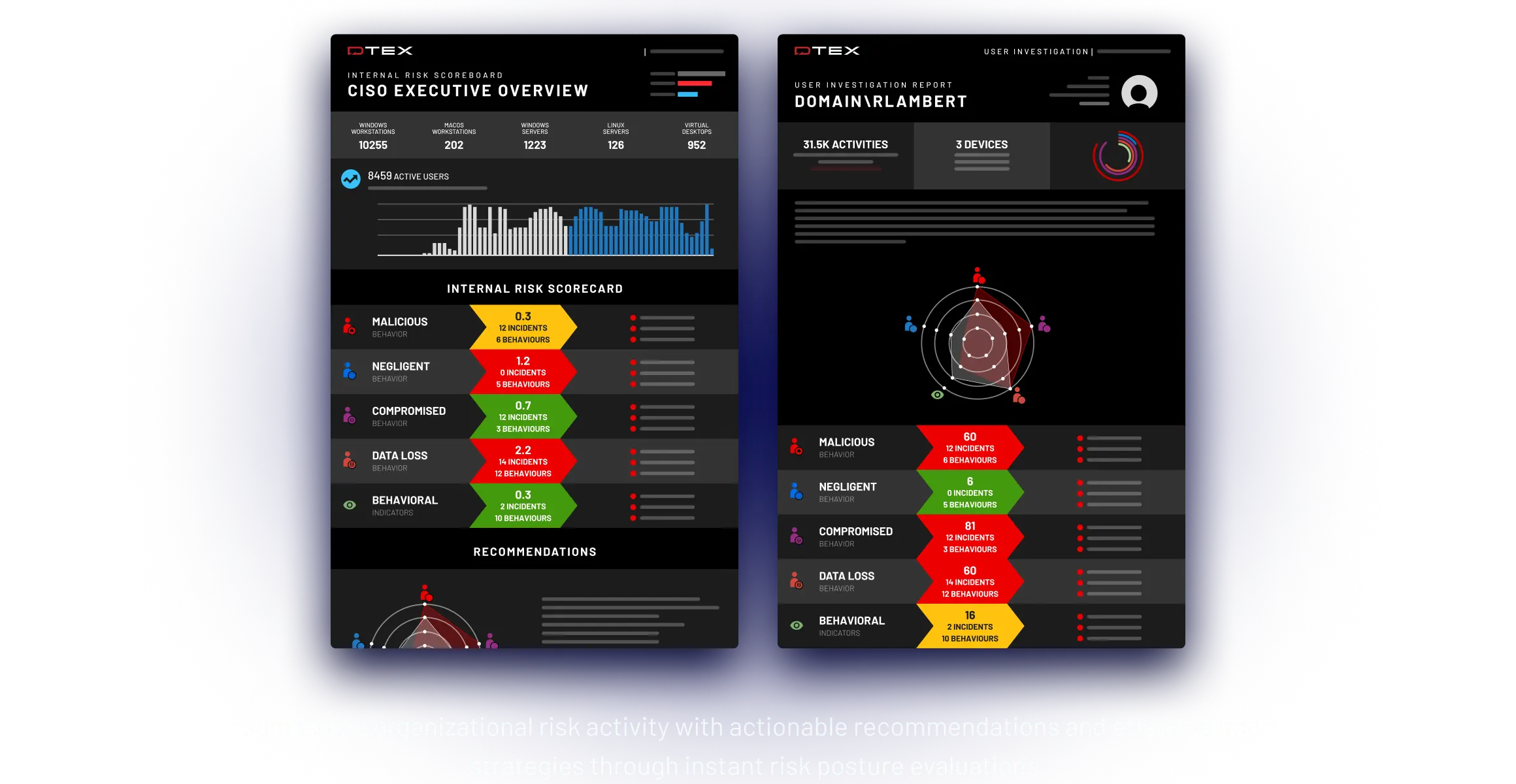
DTEX InTERCEPT PLATFORM
Built on data. Powered by AI.
Uniquely designed to collect the minimum amount of data for a near zero
impact on the endpoint and network.
Innovative platform features
Gain the visibility needed to identify risks earlier and stop data leaks.
Collection, correlation and analytics
to power contextual awareness
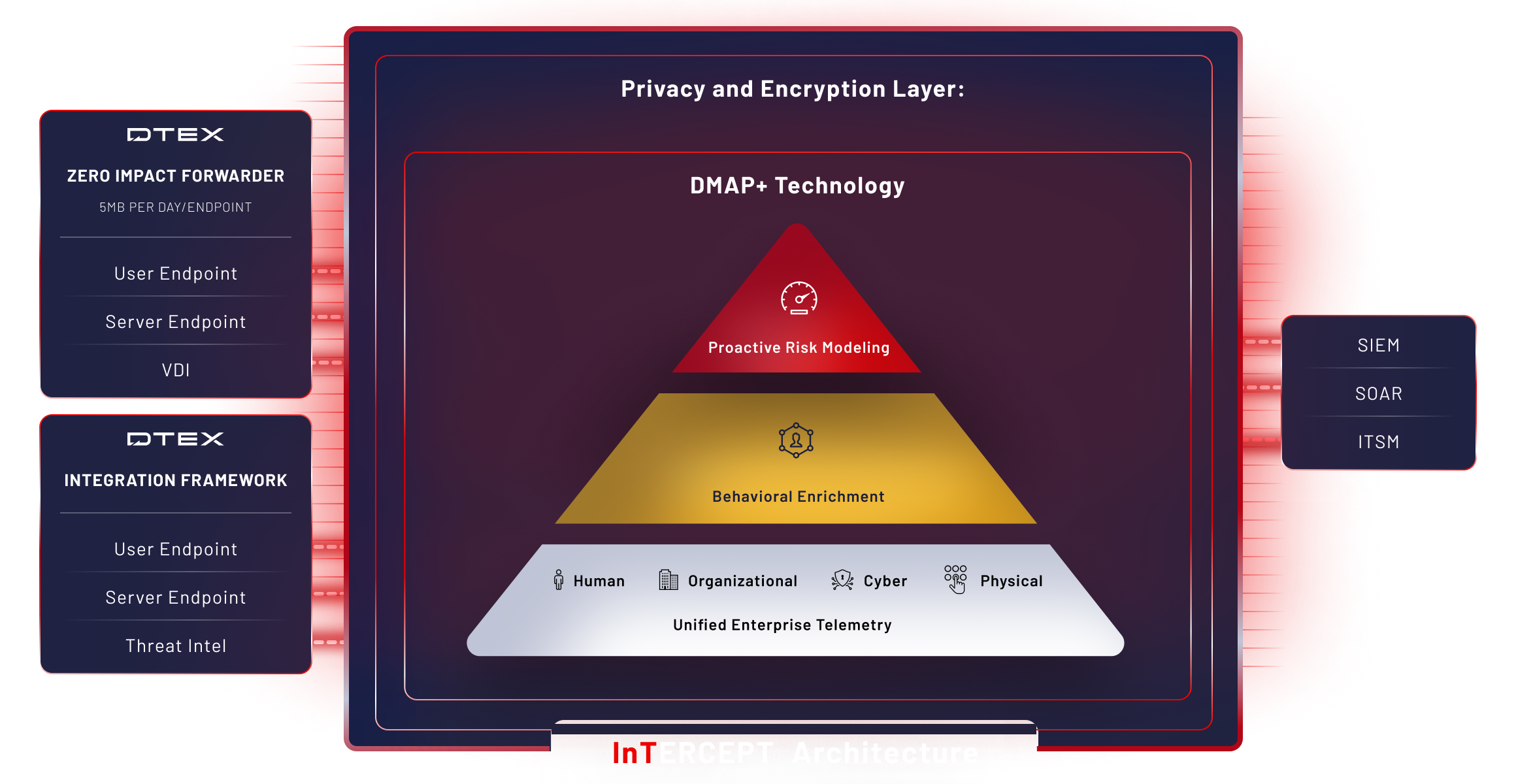
DMAP+ technology overview
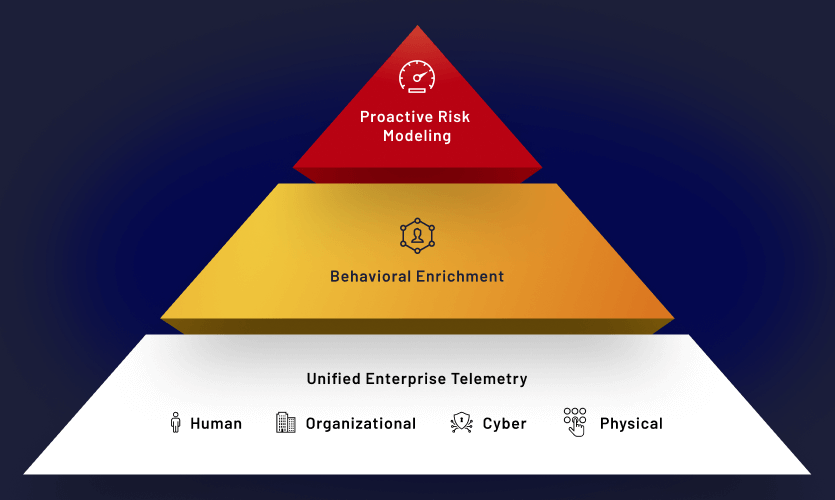
DTEX DMAP technology collects, correlates and analyzes in three distinct data layers, powering the process for AI-driven risk profiling.
Unified enterprise telemetry
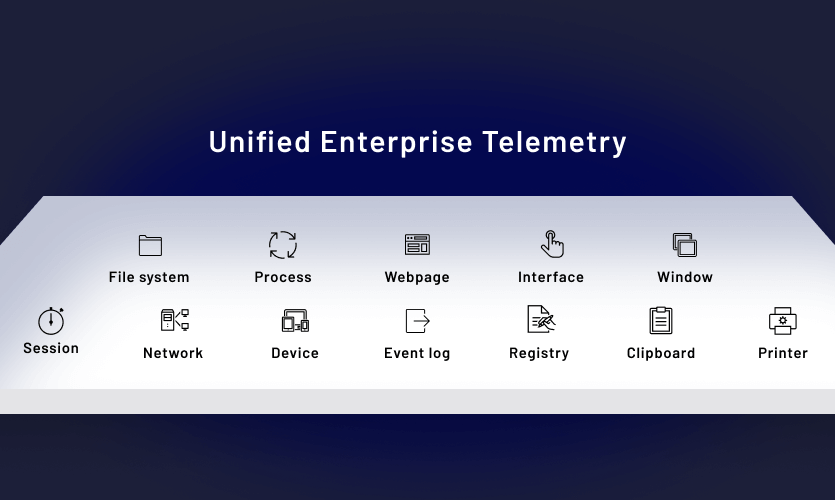
The collection layer captures activity history, behavior trends, and data utilization with situational context, data not provided by 3rd party external log sources.
Behavioral enrichment
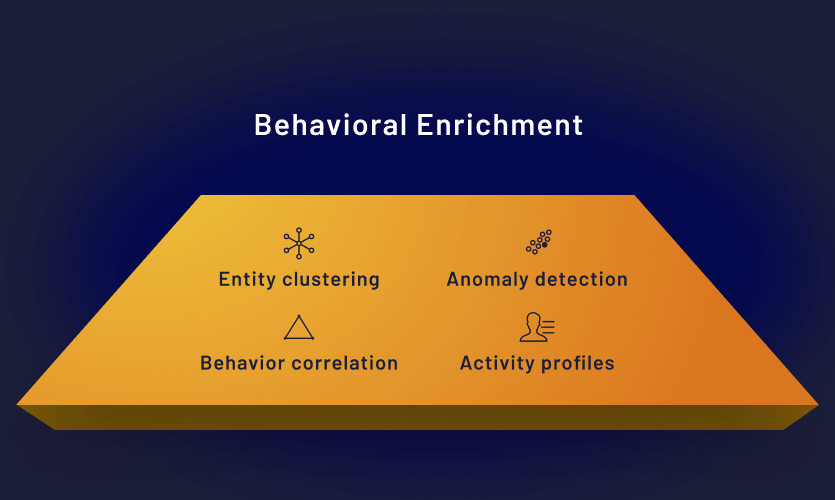
The behavioral enrichment layer parses raw data through configurable behavior profiles and machine learning models to identify activities of interest.
Proactive risk modeling
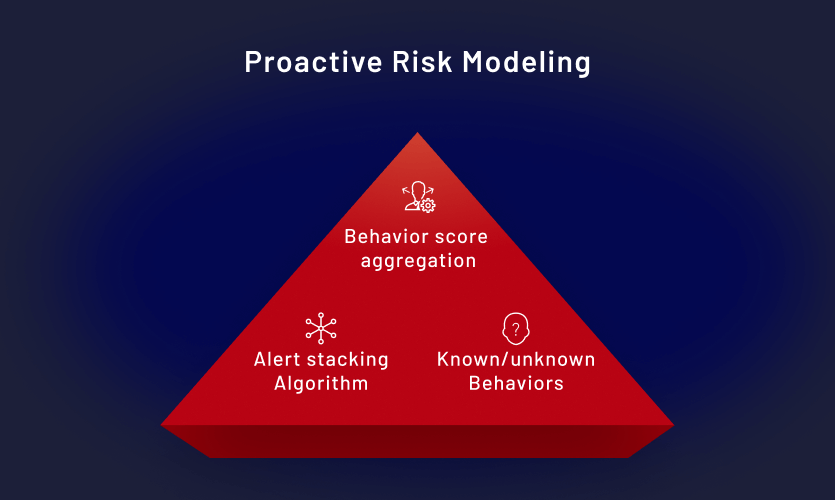
The risk analytics layer identifies patterns of potentially related attributions using advanced rules and alert triage capabilities, indicating compounding behaviors like flight risk.
Powerful benefits
Lightweight
Collect only 3-5MB of data per user, per day with minimal CPU usage and zero impact on employee productivity or endpoint performance.
Continuous
Focus on context, not content. Continuously monitor all applications with full context without waiting for a ‘trigger’ to initiate collection.
Accurate
Quickly differentiate between malicious, careless and compromised behavior in order to take the appropriate action.
AI-enabled
Get clear insight into behavioral intent, where sensitive data is going, who is accessing it, and most importantly, why.
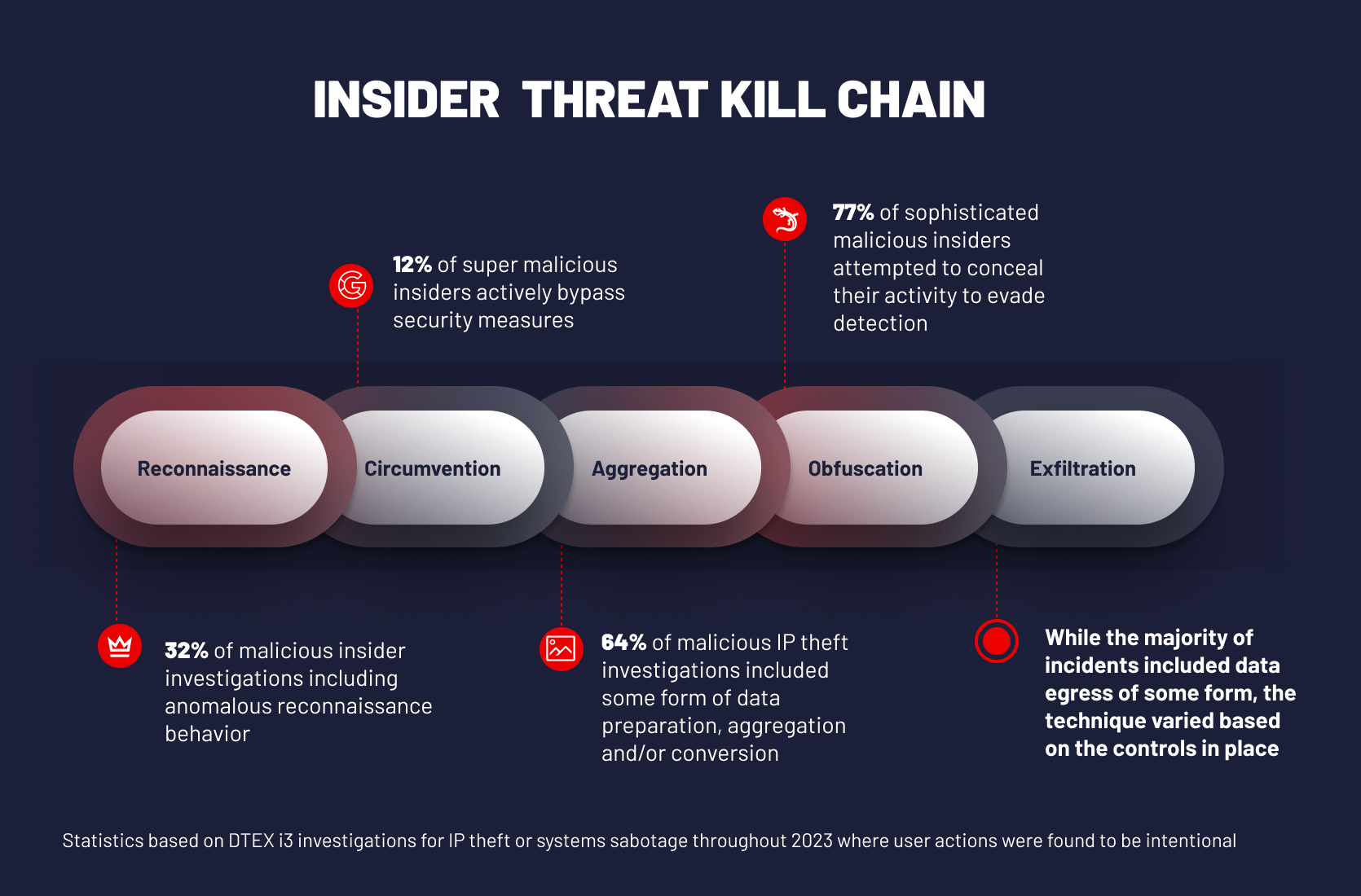
Industrial espionage and
IP theft are at an all time high
The level of visibility into all stages of the Insider Threat Kill Chain is directly related to the ability to quickly and effectively identify, stop and investigate data loss attempts before exfiltration.
Easy deployment and time to value starts now
Deploys in Minutes

Lightweight forwarders collect 3-5MB of data per user per day, create no network impact, and do not harm employee productivity or endpoint.
360° Visibility in 24 Hours
On-demand Reporting in 1st Week
Contextual Data & Forensics in Days
DTEX InTERCEPT named a Leader in Insider Risk Management