Here at Dtex and as an industry, we’ve certainly seen a concerted effort to expand what has previously been a laser focus on external threats. The risks associated with those inside of the organization are widely acknowledged, well-documented, and increasingly prioritized. Yet, a formidable challenge remains for many… both when it comes to keeping the bad actors out and ensuring critical, valuable data stays in.
Just last month, we saw headlines made by the former National Security Agency (NSA) contractor responsible for what might be the biggest breach of classified information in US history. Among other highly-sensitive material, investigators discovered top-secret hacking tools – consisting of computer code and instructions on how to use it – in the thousands of pages and dozens of computers and data storage devices seized by the FBI. Another example, seen firsthand, was the recent case of the Chinese National attempting to flee ANZ with customer data exfiltrated from leading financial services provider and Dtex customer, AMP.
THE CHALLENGE: THE ‘SLOW DRAIN’
What’s to blame for the continued struggle to stop data theft and protect valuable, sensitive information? Our complex, ever-expanding networks for one. Every employee, contractor and partner – along with every device or endpoint they’re using to conduct business and access company systems – is now a potential vulnerability and point of exploitation.
Compounding the complexity is the increasing savviness and sophistication of these users, as well as the outside actors preying on them – rendering them increasingly capable of evading traditional security solutions and flying under the radar. It’s this growing ability to find what is slipping through the cracks that is largely responsible for the current data breach epidemic. And it has given rise to one particular, and highly effective, theft mechanism: the “slow drain.”
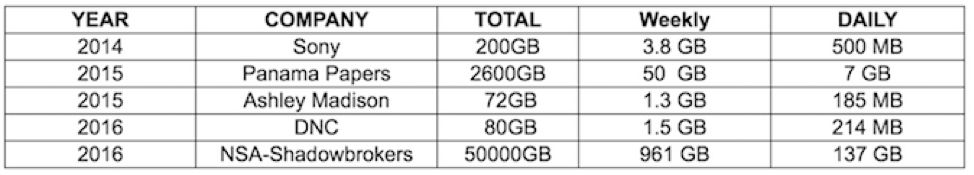
SOURCE: SecurityWeek
While the popular belief is that data exfiltration attempts happens quickly, in one fell swoop, but the truth is that most are not random or impulsive acts. Rather, the most successful and catastrophic incidents have been carried out slowly and methodically, in several stages, over the course of several months (or years, in some cases). And it was the organization’s inability to spot and plug the drain that proved to be their ultimate misstep.
Compounding the consequences is the reality that many of breached organizations did not have the tools in place to determine the source of the drain, how long it was running and just how much damage may have been caused. Take the example of Australian human resources software developer, PageUp, who recently completed an investigation nearly six months after it learned that the company had been breached. The case underscores how long it can take to thoroughly investigate a breach without ample visibility levels and data available, as well as the backlash that companies may endure as they scramble – and largely fumble – to uncover facts.
“A detailed forensic investigation on the PageUp security incident in May this year has concluded that while an attacker was successful in installing tools that could exfiltrate data, no specific evidence was found that data was exfiltrated,” the company says. (SOURCE)
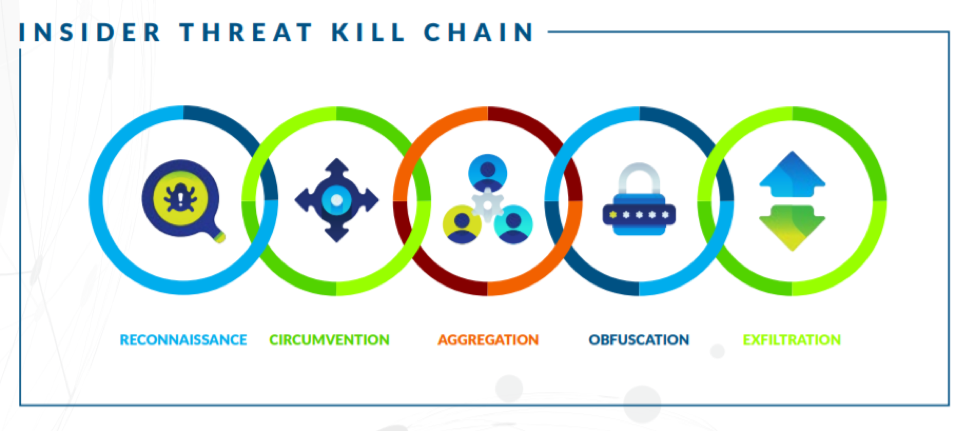
THE GUIDE: THE INSIDER THREAT KILL CHAIN
The good news is that a guide exists to help us better understand data exfiltration incidents and attempts: The Insider Threat Kill Chain. The level of visibility an organization has over all stages of the Kill Chain is directly related to the ability to more quickly and effectively identify, stop and investigate data exfiltration attempts. Without ability to get the full picture, it is impossible to truly understand how an incident unfolded and get answers to key questions – such as what the intent was, where gaps might exist, and how much damage was done.
But, how do we know if we have complete visibility over the Kill Chain? What exactly are we looking for?
Reconnaissance: When considering an exfiltration attempt, users start by their homework. In seeking out files and data to steal, they will typically visit unusual file locations or new-to-them systems. They may also download things like hacking or sniffing tools that will help them pinpoint where security vulnerabilities and gaps exist.
Circumvention: From there, the user moves on to determining how to best – and most discreetly – access the data that they are looking to steal. This typically involves finding ways to bypass security, either through anonymous or private browsing, non-approved VPNs and the like. Dtex risk assessment data shows that this particular behavior is quite common – as analysts noted instances of security bypass, or attempted bypass, in 95 percent of those conducted last year.
Having visibility over this stage is especially critical when it comes to understanding intent, as it can inform whether a user was acting maliciously and deliberately. It also can inform where gaps in security policy and infrastructure exist. In many cases, we’ve found bypass has occurred – and gone undetected – because a security solution that was put in place to block various sites, applications, or activities failed… and the organization was unaware.
Aggregation: Users then move to collect the targeted data into a single location and tend to engage in atypical file activity —which can include excessive copying, random movement or deletion of files, and unusual rates of compression. As we touched on earlier, this stage can happen slowly and over extended periods of time if the actor understands traditional security thresholds and gaps… and how to move under-the-radar to avoid setting off red flags.
In the example of the exfiltration attempt at AMP, because they had full visibility into all user behavior and across the full Kill Chain, it was possible to discern that this stage included the Chinese National downloading the passport and driver’s license information of 20 customers and saving it via his personal email account.
Obfuscation: This is the stage where users attempt to cover their tracks. Typical behaviors include renaming files at the endpoint, using stealth browser settings such as ‘Incognito’ mode, or going off network in hopes of concealing activity.
Across the risk assessments they’ve conducted, Dtex analysts consistently find the most effective method for detecting truly malicious individuals – notably, before exfiltration occurs – is to look for signs of data obfuscation. Why? There are far fewer ways for a user to properly obfuscate their Internet traffic as compared to the almost infinite number of other mechanisms that can be used for exfiltration. Looking at the AMP example, the exfiltrator attempted to install a ‘darkweb’ Internet browser to shield his malicious activity – and instead, because of the tools in place, prompted a security alert.
Exfiltration: The final stage is where the user follows through with the unauthorized data transfer and an act of exfiltration – or theft or breach – occurs. Ideally, the malicious insider is caught long before getting to this point… but, we do understand that can be easier said than done.
The tendency is for most organizations is to focus solely on this one point-in-time and block this particular activity but doing so only gives a small fraction of the story. Neglecting to understand the full chain of user behaviors – in context – that led to this point means neglecting to understand what actually happened and how it can be stopped it in the future.
THE CRITICAL PIECE: COMPLETE, USER-FOCUSED VISIBILITY
The key is both knowing what to look for, both before and after an incident occurs, and having the complete visibility needed to see everything happening across the organization. The truth is, you just don’t know exactly what happened in any security incident unless you see every stage of the kill chain.
An important nuance here, though, is that this visibility needs to be focused on the user, on the human – not on malware strands, or network events, or a set of pre-defined parameters and rules. At its core, the Insider Threat Kill Chain is a collection of malicious insider behaviors – which deems it absolutely imperative to be able to see every user behavior taking place and the context surrounding it.
This user-focused visibility also plays a critical role in the ability to spot anomalies and generate the early-warning signs needed to stop malicious or risky behavior before an exfiltration attempt occurs. The ability to elevate high-risk users or activities is what keeps an exfiltration attempt or incident from becoming an all-out catastrophe.
Having complete, user-focused visibility also means having a full, unbroken audit trail when an incident does occur – which is essential to accelerating investigations and minimizing costs. In the case of AMP, it was this audit trail that ultimately led to the successful arrest and prosecution of the malicious actor. And on the flipside, in the case of PageUp, the damages suffered could have been significantly lessened if the company had been able to get answers quickly and cut down their 6-month investigation time.
To learn more about how to gain full, user-focused visibility over the full Insider Threat Kill Chain using Dtex, download our data sheet.
Topics
Subscribe today to stay informed and get regular updates from DTEX Systems





