The Dtex 2018 Insider Threat Intelligence Report continues to lead industry discussions about how frequently the insider threat occurs in public and private sector organizations. Last week, CSO’s Christopher Burgess dove into the report in “How pervasive is the insider threat in your company?” Burgess’ story looks at all insider threat types active today and provides comments on ways to reduce associated risks.
GDPR: Still Much to Do
Dtex EMEA VP Mark Coates penned a timely piece for Dark Reading revealing further how regulations designed to improve security and privacy can actually end up eroding it. In “How GDPR Could Turn Privileged Insiders into Bribery Targets,” Coates explains why this headline is valid:
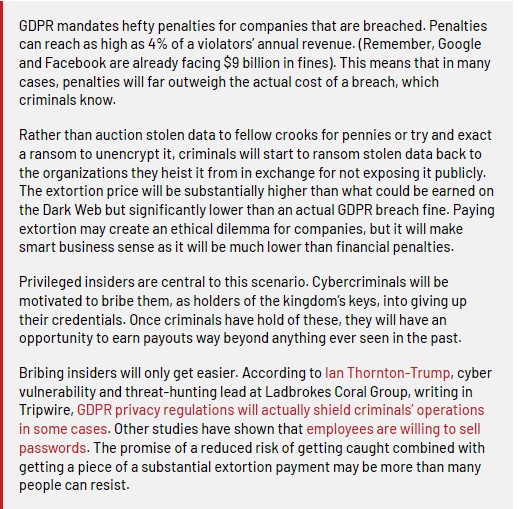
He concludes with four steps organizations can take to reduce risk.
More Dtex News …
Last week, Dtex CEO Christy Wyatt contributed a byline to Chief Executive Story last week where she had an opportunity to share insights about her personal leadership style and how she applies it to her role at Dtex. Wrote Christy:
Read the full story at: Focus (you don’t have as much time as you think)
Also last week, Dtex Insider Threat Analyst (EMEA) Katie Burnell was featured in Dark Reading’s new “Women in Security” list, which highlights women who are driving change in cybersecurity. Read the full profile at: 10 More Women in Security You May Not Know But Should.
Vulnerable Humans Continue to Drive Data Breaches
Last Monday, UnityPoint Health reported the cause of its recent data breach to the California Attorney General reporting site. While the detail in required breach notification letters varies, it reads as if UnityPoint is quite clear about what happened. According to UnityPoint:
What’s more, there’s the challenge of the ‘unknown unknowns.’ The simple fact is that if we don’t know it presents a risk, we won’t know to look for it. If rules and indicators are designed based only on known and available information, without seeking out additional context or intelligence, there will inevitably be things that fall through the cracks.
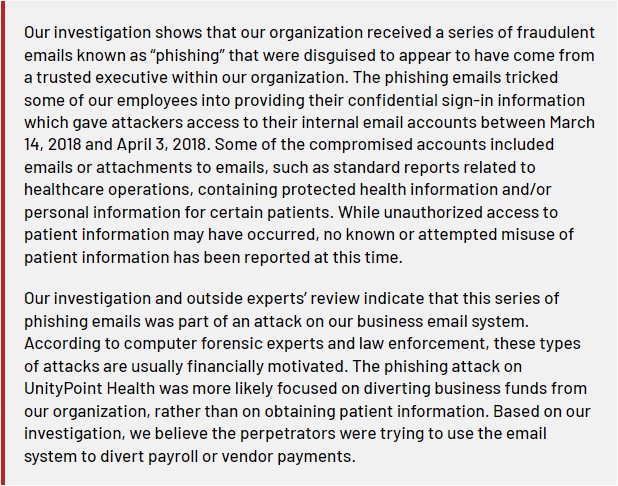
This recent data breach is yet another example of how frequently and easily organizations’ most trusted insiders are fooled by external attackers. It is also a reminder of how often organizations fail to provide employees with protection against attacks. To learn more about the problems vulnerable humans create, read: Introduction to the Insider Threat: What It Is and Why in Matters.
Topics
Subscribe today to stay informed and get regular updates from DTEX Systems
Interested in learning more?
Subscribe today to stay informed and get regular updates from DTEX





