Making an effort to balance privacy and security is vital for organizations who want to thrive in the new normal. As the findings of our 2021 State of Workforce Privacy and Risk Report showed, more than half (63%) of companies surveyed believe it’s important to protect employee privacy, yet less than half (47%) say they are effective in doing so.
Change. It’s the one constant we can all count on. And in the last few years we’ve seen more than we would have liked for sure. So, it’s no surprise the cyber security landscape hasn’t been spared, especially when it comes to the latest evolution of the endpoint vendor landscape. Next-generation leaders such as CrowdStrike, Cybereason, and SentinelOne have continued their growth and joined the likes of Palo Alto in the XDR market. Another development is the maturation of Microsoft’s 365 E5 Defender for Endpoint and Cloud Apps modules, as well as its Information Protection & Governance capabilities.
Microsoft 365 E5 Defender and Information Protection tools are gaining a foothold within our customer community and are proving to offer the foundation they need to identify and classify structured, regulatory mandated data and limit negligent data loss. This is a good start, especially for cyber security teams whose organizations have chosen to adopt Microsoft as their security platform
What our customers are learning however is that they need more. Specifically, they need the ability to proactively detect and capture intentional data loss incidents, stop intellectual property theft, pinpoint human behavior attribution as well as malware root cause, and prevent the use and misuse of unsanctioned and sanctioned SaaS applications.
Earlier today we announced new capabilities within DTEX InTERCEPT to support these customers with ‘out of the box’ Behavioral DLP capabilities that expand the scope and protection provided by multiple Microsoft 365 E5 modules to provide the holistic behavioral data loss prevention and workforce activity intelligence capabilities they need across the entirety of an enterprises’ application, data, and operating system architecture to meet their use-cases.
Through enhanced integration with the Microsoft Defender for Endpoint and Cloud Apps modules, as well as Information Protection & Governance, we are delivering cross-platform user behavior telemetry collection, visibility, and analysis capabilities that answer the questions of Who, What, Why, When, Where and How related to a user’s intent when interacting with organizational data and IP regardless of geo-location, on or off-network without employing invasive surveillance data gathering techniques.
Precisely, we are extending Microsoft Information Protection and Governance module’s data classification capabilities with policy templates and multi-factor data sensitivity algorithms to identify the precursors associated with intentional data loss incidents and protect non-regulated intellectual property such as source code, design documentation and other unregulated data types and formats.
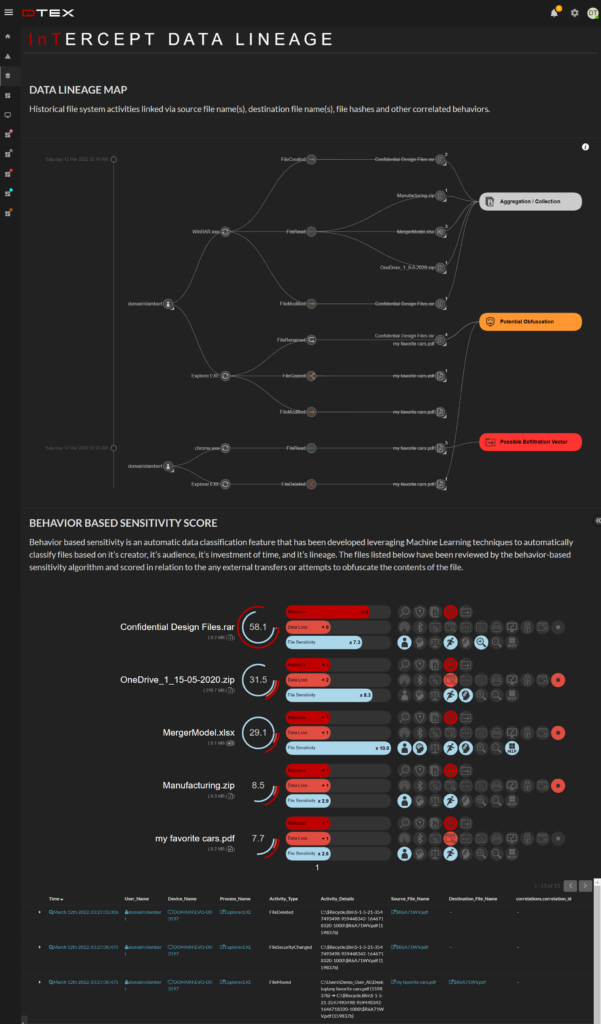
We also infuse Microsoft Defender for the Endpoint with powerful human behavior attribution and malware root cause analysis created by mapping user activity against the MITRE ATT&CK framework and its own patented DMAP+ metadata collection, correlation and analytics engine to contextualize IOC’s and alerts with user activity intelligence. The result is single-click access to dynamic, insider risk and data loss dashboards that offer evidentiary quality incident and file lineage intelligence with drill-down investigative capabilities that inform rapid, targeted incident response and remediation in support of Microsoft’s IRM case-management tools.
In addition, we made it possible for customers to utilize DTEX InTERCEPT to extend Microsoft Defender for Cloud Apps’ powerful IAM capabilities to include the continuous profiling of endpoint access to all web-based resources to detect suspicious SaaS-based uploads and anomalous behavior in real-time without additional configuration. This gives SOC teams and IR analysts the ability to detect both user and peer group anomalies occurring across the entirety of their IT environment including Windows, macOS, Linux, Citrix, VMWare and other cloud-based environments such as AWS Workspaces.
Lastly, but importantly, the additional user attribution, data movement and file lineage, as well as endpoint access intelligence across and beyond an organization’s Microsoft 365 environment captured by DTEX InTERCEPT is seamlessly available within Microsoft Sentinel to enrich SOC operations with user behavior telemetry.
Our strategy is simple, deliver innovative technology that solves real operational and cyber security challenges with a platform that provides deep human telemetry and actionable intelligence. We’ve worked tirelessly with our customers to understand the nuances of the endpoint data they had, the shortcomings of existing solutions, their ineffectiveness and accuracy, and the missing link around user behavior related to a data loss event. And that’s what makes news like today’s so exciting, we are helping our customers achieve their goals.
To learn more, check out our new infographic: How Organizations are Utilizing DTEX InTERCEPT with Microsoft 365 E5.
Subscribe today to stay informed and get regular updates from DTEX Systems






