The recent Pentagon leaks have drawn a fine line between trust and risk management, and the need to strike a balance to prevent data loss while maintaining loyalty.
As an IT specialist for the Air National Guard, Jack Teixeira – the US airman behind the leak of US military secrets – held a top-secret clearance, affording him access to highly classified intelligence.
As of 2019, nearly 1.3 million people had a top-secret clearance, while 4.2 million people were deemed eligible to access classified information.
Granting such access implies an enormous level of trust that this sensitive information will not be shared.
By virtue of his clearance, Teixeira may have had the right to know (though whether he truly did is another debate), but by no accounts did he have the right to share this intelligence with people (the public) who did not have the right to know.
The case of Teixeira raises more questions than answers:
- Was technology used to flag anomalies in employee behavior that were indicative of risk?
- Were there processes in place to ensure employee loyalty to the government was maintained?
- Was there an internal process in place for employees to report on suspicious behavior in relation to insider risk to warrant further investigation?
- What was the culture? Did employees feel trusted, respected and protected?
- How were classified documents classified and protected, even with those trusted to access them?
There has been considerable debate on whether the government is overclassifying sensitive information and whether this is inadvertently increasing the risk of data loss. Indeed, so much data to protect combined with so many people with access it only exacerbates this risk.
Changing the way data is classified to begin with is one way organizations and federal entities can help mitigate insider risk, proactively, while maintaining employee loyalty.
File Lineage for Data Classification and Protection
Choosing what to classify or protect does not need to be based on the contents alone which, in the worst case scenario, can jeopardize the right to privacy. Understanding the journey of files over time, and the way employees interact with them, can arm insider risk teams with the insights they need to proactively mitigate risk in a way that scanning file content in isolation cannot.
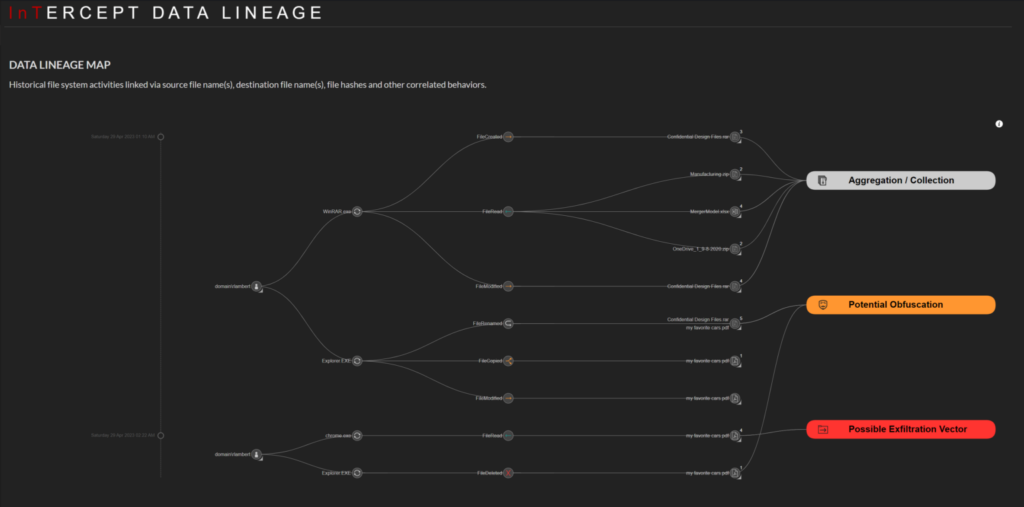
File lineage enables insider risk teams to identify the data with the highest risk of being exfiltrated as well as identify the employees that are putting the data at the most risk. With this understanding comes the power to course correct in a way that is proportional to the level of risk posed.
Trust and Risk: A Double-Edged Sword
On the one hand, trust arms employees with the safety and anonymity to stay motivated and engaged in their role. On the other hand, unconditional trust can come at a cost, fueling the impression of an apathetic employer that won’t notice any transgression.
Managing insider risk should not come at the expense of trust – but it is possible to strike a balance. File lineage provides the best of both words, enabling actionable insights on risk resolution without invading privacy or eroding trust.
Use Case: Preventing Insider Threats with File Lineage
DTEX enabled this telecom company to harness the power of file lineage to proactively and accurately identify, classify and protect its most at-risk data.
Instead of manually attempting to tag and categorize every piece of data in the organization, they now have the visibility to see how people and locations interact with that data.
Importantly, the company can now categorize data in a business context by answering the critical question: What is the risk that this file will be lost or compromised, based on how many people touch this file and what they do with it? This knowledge gives them the power to prioritize their security measures around the high-value data that is most vulnerable.
To learn more about how you can leverage file lineage to classify and protect data while respecting privacy, book a free insider risk assessment or contact us for a discussion.
Subscribe today to stay informed and get regular updates from DTEX Systems






