
Gartner analysts Paul Furtado and Jonathan Care recently published a short piece on insider risk management titled: The Rule of 3 for Proactive Insider Risk Management. The research note provides readers new to the topic with a solid foundation of insider risk management and how to attack the challenge of insider risk. For example, it points out the difference between insider risk and insider threats: every user presents risk, but malicious intent defines a threat. It also points out the obvious advantage an internal attacker has over an external threat: they know where the target data is and typically have authorized access to it.
The “Rule of Three” also states what we at DTEX Systems consider to be obvious: security and compliance teams must understand threat types, threat activities, and mitigation goals.
We agree with most of the Gartner team’s suggested approach however do recommend a bit of fine-tuning drawing on our experience with hundreds of enterprise clients and the MITRE Behavioral Sciences team.
Remote Workers Act Differently
Gartner points out that defending against insider threats is harder in a Work-From-Anywhere environment. The most common explanation is that employees, contractors, and partners are working outside the protection of the corporate network. They have access to hardware and software that may not be approved, and home networks are often poorly secured. The behavioral scientists add other factors. When working remotely, employees may have greater perceptions of anonymity and less perception of monitoring. There are often fewer supervisor interactions for remote workers, adding to the impression of less monitoring.
For defenders, remote workers complicate already difficult problems. There is no oversight or detection of unauthorized visitors to a home office, no reliable method of determining who is on the keyboard, or what other equipment is being used. Working hours may differ, making it more difficult to rely on rule-based indicators of anomalous behavior.
The Rule of Three
Gartner’s Rule of Three breaks Insider Risk into (you guessed it) three categories:
- Threat Types
Gartner views the threats as Careless Users, Malicious Users, and Compromised Credentials (essentially, malicious outsiders). Careless users put sensitive data at risk through negligence. They are either unaware of good security practices or bypass those practices in an effort to be more efficient (emailing sensitive data, storing it on unauthorized devices, etc.). Malicious users have malicious intent. They purposely take actions to gather and exfiltrate data. The third category, compromised credentials, are certainly a concern.At DTEX, we have come to understand a fourth category, one we call the Super Malicious Insiders. Similar in a way to an external hacker using stolen credentials, super malicious insiders have the intent and the technical skills required to steal data without detection. Importantly, they frequently also have information the malicious outsider lacks, including an understand precisely how an organization’s defenses work, having received training from their employer. If you’d like to learn more about Super Malicious Insiders, download the DTEX 2022 Insider Threat Report here. - Threat Activities
Gartner’s paper breaks this into Fraud, Data Theft, and System Sabotage. While endpoint detection and response solutions can help with the third category (malware and ransomware), increasingly a more systemwide perspective is required. A malware signature may be recognized, but alerting on unusual activity (e.g., high number of file accesses, high rates of encryption) are better detected by a solution like DTEX InTERCEPT. - Mitigation Goals
The third Gartner rule defines the objectives of an insider risk program: Deter the individuals; Detect the activity; Disrupt the effort. The first largely deals with careless users and focuses on cyber security awareness programs. We would take that further, and use real-time warnings to educate users when their actions could put information at risk.
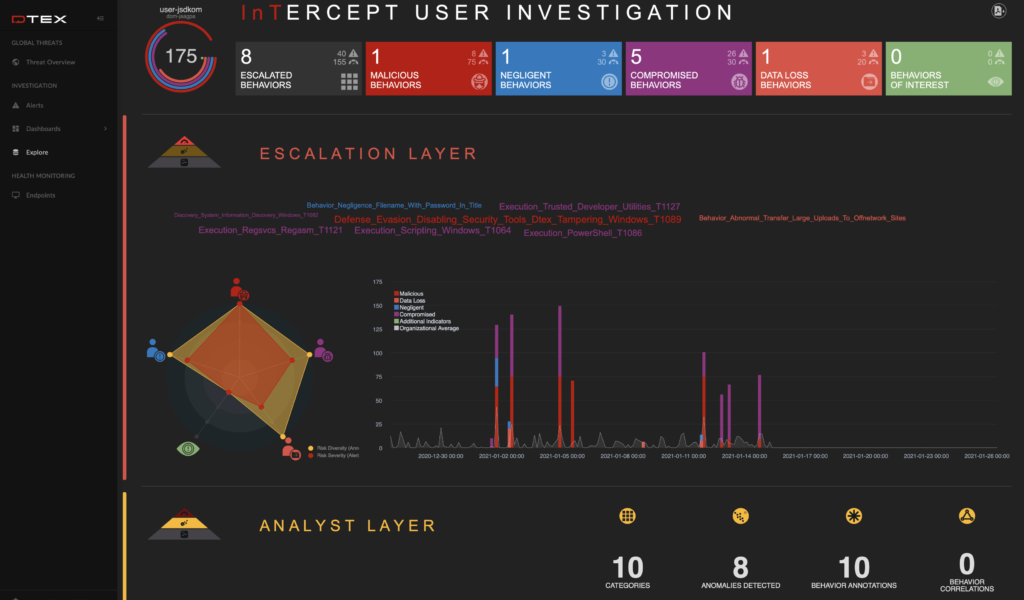
The second objective falls a bit short in our eyes. Gartner recommends, “tooling and staffing to be able to detect any signs of improper data exfiltration before it leaves the care and control of the organization.” Our experience, and that of our customers, has proven that using rules based on specific actions by specific individuals (or roles) on specific data results in false positives, creating alert fatigue for SOC and Insider Risk teams. A skilled attacker, whether a Super Malicious Insider or external attacker with stolen credentials, knows how to achieve their goals without alerting the SOC. A better approach is to understand each action in context of what’s happened before, after, and even in comparison to, the last few months, to identify Indicators of Intent as well as deviations from the norm. This means understanding each step an attacker can take and correlating those irrespective of the order in which those occur.
The final objective—disrupt the effort—is one we fully endorse in our solution. This requires understanding the Insider Threat Kill Chain and the ability to block threats automatically. As noted, SOC teams are overwhelmed with issues. Using automation to implement application locks or device quarantines for negligent or anomalous behavior, session locks for malicious insiders, or network locks for compromised accounts prevents an attack from proceeding.
We encourage you to have a look at Gartner’s Rule of Three note in detail. It’s a solid piece and offers strong recommendations for those beginning to dig into their insider risk management initiatives.
Topics
Subscribe today to stay informed and get regular updates from DTEX Systems





