When organizations think of insider threats, the focus is often on disgruntled or malicious employees or partners misusing data. This could include downloading sensitive data to USB drives, sending it to personal email accounts, or uploading it to cloud drives.
Each of these actions is something well within the technical capabilities of a typical employee. Despite their malicious intent, these folks aren’t “hackers.” No special skills are required. They aren’t cracking passwords or escalating privileges. They are simply taking the data they have access to in their everyday jobs.
This is why most Data Loss Prevention solutions are rule-based. They focus on the individual actions on specific data by specific users. When Bob from engineering downloads a terabyte of tagged design documents for a project he doesn’t normally work on—ALERT! When Alice from sales emails tagged sales projections to her Gmail account—ALERT!
Brilliant…
We agree with most of the Gartner team’s suggested approach however do recommend a bit of fine-tuning drawing on our experience with hundreds of enterprise clients and the MITRE Behavioral Sciences team.
But what happens when employees like Bob and Alice are hackers? When they have the same technical skills as the proficient and external “bad guys” we worry about? Now add to that the fact that we have trained these skilled insiders on our defensive measures, so they know the specific rules and actions we are looking for. Now what?
Welcome to the age of the Super Malicious Insider. These insiders have the same malicious intent as the traditional insider threat paired with the technical skills to carry out sophisticated attacks and the knowledge to evade detection.
This isn’t a hypothetical anymore. It’s simple for people to find resources for learning “hacking” tricks and techniques. The demand for these skills for defensive purposes is overwhelming, and more people than ever before are developing these skills. We train our employees to understand clues of malicious activity and on the technologies we use to detect threats.
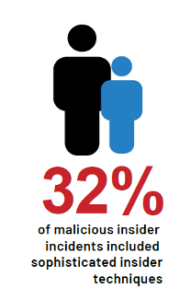
Our 2022 Insider Risk Report makes clear the impact of this threat. Almost a third of all malicious insider events included sophisticated techniques like “burner” email accounts and the use of Open Source Intelligence (OSINT). The prevalence of super malicious incidents was highest in technology companies (33% of the total incidents) and critical infrastructure (24%).
Our research with MITRE shows that these threat actors could carry out attacks without triggering traditional rule-based monitoring tools. They have identified, collected, and exfiltrated data in ways that appeared tobe normal activity. They understand what these systems are watching for and simply avoid using those. Even adding MITRE ATT&CK tactics, techniques, and procedures doesn’t deter them. 96% of the incidents we saw were carried out while avoiding using ATT&CK techniques.
We will be talking a lot more about Super Malicious Insiders in the future. To learn more about them today, download our 2022 Insider Risk Report.
Subscribe today to stay informed and get regular updates from DTEX Systems






