Netflix recently released a new documentary which is timely to today—Valentine’s Day. It tells the story of The Tinder Swindler, a man who pretended to be a wealthy diamond mogul and courted women on dating apps as part of one big scheme to ultimately con them out of millions of dollars.
Here at DTEX we also recently released “related” content. No, it doesn’t surround love interests, luxury travel or fancy parties. However, it does include theft, deceit, cover-up and obfuscation tactics, and, well, heartbreak.
Just last Tuesday we released our 2022 Insider Risk Report, which identified the rise of the ‘Super Malicious Insider’ persona. What do the Super Malicious Insider and The Tinder Swindler have in common? A lot actually.
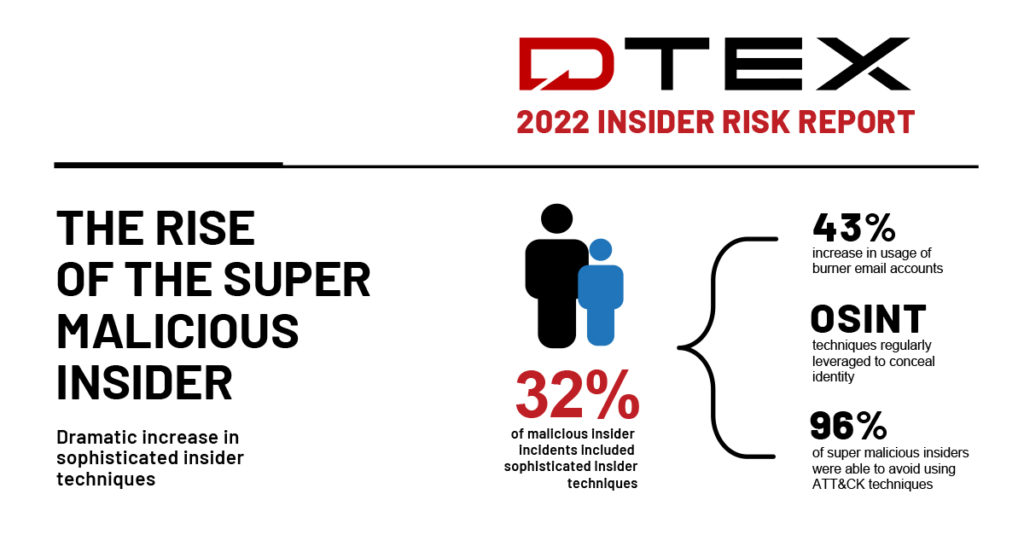
The Super Malicious Insider is a technically proficient employee who is acutely aware of an organization’s cyber security architecture, solutions, and processes and who understands both the technical and human analyst limitations in detecting insider threat indicators. Our report, based on real investigations and data collected by DTEX’s Insider Intelligence and Investigations (i3) team, found that super malicious insiders account for 32% of attacks, including a 43% increase in the use of burner email accounts. Additionally, the team found a noticeable increase in the use of OSINT practices to conceal identity, and the active avoidance (96%) of techniques known in the MITRE ATT&CK framework.
To summarize, the Super Malicious Insider acts a lot like The Tinder Swindler. They both use a number of the same tactics to “cozy up to” their victims and fool them, like burner phones or fake social profiles. They leverage their insider and technical knowledge to take advantage of either online daters who are seeking connection or employers who are trusting, to steal money or critical data in secrecy and then cover their tracks and disappear.
How do you prevent this heartbreak?Don’t ignore the red flags, in dating, or in security. And know what to look out for to protect yourself and your organization so that you can stop both of these malicious actors before it’s too late.
Interested in learning more about our findings and the emergence of the Super Malicious Insider persona? We’d love to connect!

