The Global Leader for Insider Risk Management
Powering a trusted workforce by stopping insider risks from becoming insider threats.
Join us on May 8th in San Francisco for a special insider risk management event.
Blurred Lines: Navigating the Convergence of Internal and External Threats, featuring Kevin Mandia of Mandiant, Google Cloud and Brad Maiorino of RTX.
RSVP
DTEX is
different:
Patent-protected privacy
by design
Proven scalability up to 800,000 users in a single implementation
DTEX i3
Delivering Trusted Insider Intelligence and Investigations Support
DTEX i3 enables enterprise and federal entities to uplift their insider risk capability maturity to detect and prevent insider risks from materializing into data loss events. The team offers a comprehensive set of insider risk services, including investigation support and insider risk assessments, and publishes regular counter-insider risk research.
2 NEXT-GENERATION PLATFORMS
DTEX InTERCEPT™
Next-gen Insider Risk Management and Behavioral DLP
Detect, deter, and disrupt insider risks before they become threats.
Explore InterceptDTEX PULSE™
Privacy-centric Workforce Cyber Intelligence
Harmonize employee privacy, performance, and well-being to support digital transformation.
Explore PulseStrategic Partnerships
A proven leader in the eyes of top industry analysts
Security leaders can use this Best Practices for Insider Risk Management report to build a successful program.
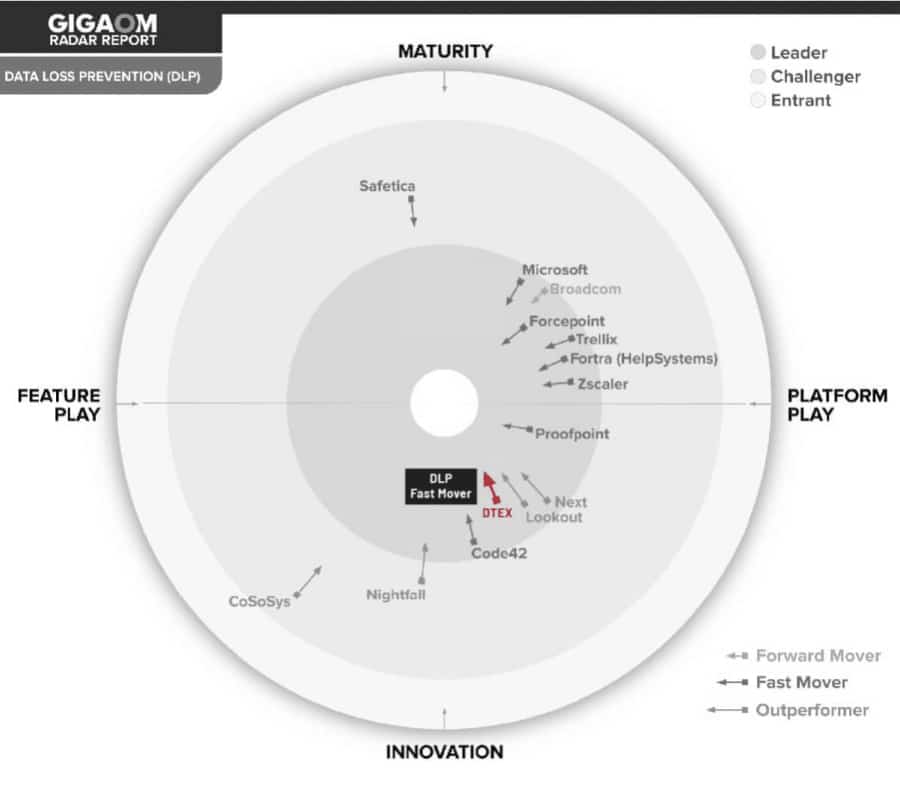
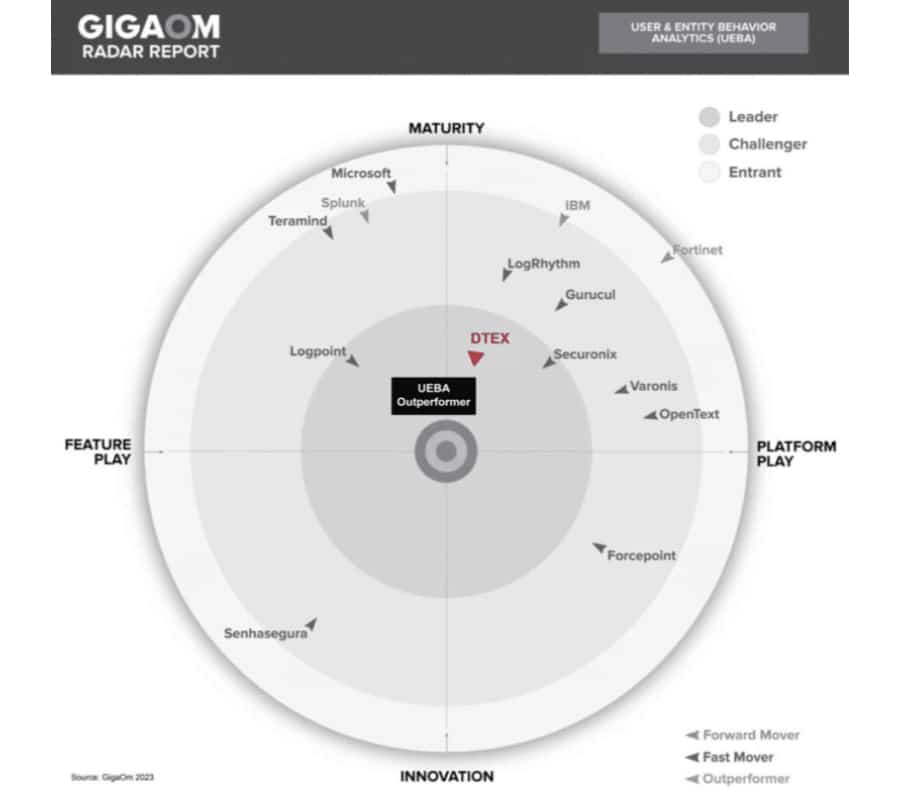
READ REPORT >THE MARKET LEADER IN BOTH DLP & UEBA
PROTECTING DATA AND PRIVACY REQUIRES A HOLISTIC AND PROACTIVE APPROACH.
Are you ready for a solution that works? Talk to us about mitigating insider risk, "left of boom," while cultivating a trusted workforce.
Gartner, Market Guide for Insider Risk Management Solutions, 18 April 2022, Jonathan Care, et. al. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.