Australia’s Department of Home Affairs has hosted its first Cyber and Infrastructure Conference, providing industry professionals insights to champion organizational security and resilience.
Held in Sydney on 25 March, the inaugural event featured a number of expert speakers, a panel Q&A and a live hypothetical exercise on managing security risk.
Home Affairs Secretary Michael Pezzullo AO set the tone early in his opening address, when he cautioned that a cyber incident, akin in hostility to what we might see in physical warfare, could occur in the “not too distant future.”
“This is not a script for a fictional future action thriller. It is a cold, hard risk, for which we have to be prepared,” he said.
The recent spate of cyber attacks on critical infrastructure organizations has demonstrated the need to provide a coordinated response to risk management. This is particularly true for insider risk. Creating an insider risk program that puts the human first is going to be a key priority moving forward in protecting the critical organizations that underpin our way of life.
A Human-Centric Approach to Risk
One of the biggest takeaways at the conference was the need to change perceptions on cybersecurity and, in particular, insider risk.
This was a key topic during a panel discussion between Min Livanidis (Amazon Web Services), Leanne Close (Risk 2 Solution Group), John Yates (Scentre Group), Mike Gallacher (Ports Australia) and Brianna Casey (Foodbank).
It is becoming increasingly accepted that humans are the number one cause of most cyber security incidents. But that’s not to say most security incidents are a result of insider threats.
The reality is most human-led security incidents are a result of non-malicious behavior. MITRE Corporation defines non-malicious as an insider who does not seek to cause harm.
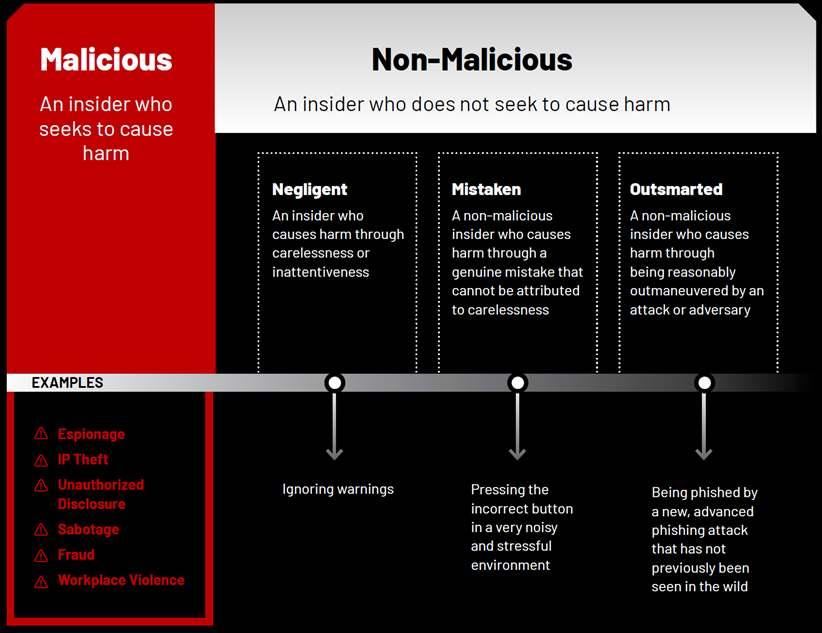
While all insider threats were once an insider risk, not all insider risks go on to become an insider threat. With this understanding comes the opportunity to change the narrative to foster a culture of support, not suspicion.
In practice, this means moving away from militarized language, such as ‘insider threat’ (which only alienates and disenchants employees) towards enabling language, such as ‘proactive risk mitigation’ (which seeks to empower and support people). Insider risk leaders can, and should, consider the nuance of language in their communications – both internal and external. Whether it’s simple day-to-day communications with employees or the media, or in security or HR policy creation, language can make all the difference in fostering a culture where employees can, and want, to be active participants of an insider risk program. Our 2023 Insider Risk Investigations Report dedicates an entire chapter on communication and includes practical tools, including an Insider Risk Resolution Decision Tree and Communications Framework, to help you change the narrative to create an inclusive risk-aware culture.
Critical infrastructure will increasingly be at the heart of national and international life. As the security landscape continues to evolve, now is the time for organizations to revisit their security strategy and, in particular, the language and culture they adopt to mitigate insider risk.
To learn more about the insider risk landscape and recommendations for proactive risk mitigation, download our 2023 Insider Risk Investigations Report.

