Insider Threat & Data Loss Protection for Servers
DTEX InTERCEPT protects cloud, on-premises, and virtual servers from data breaches, insider threats, and outsider infiltration with unparalleled visibility, detection and scalability. InTERCEPT provides real-time visibility to all server activity as it relates to a user, application and system, applying advanced analytics to discern legitimate activity from malicious “Indicators of Intent” including those commonly associated with data loss such as reconnaissance, obfuscation, and circumvention activities. This delivers accurate awareness and the ability to pinpoint threats early in the kill chain to identify risks before exfiltration attempts.
Download Now: Comprehensive Server Visibility & Protection with DTEX InTERCEPT
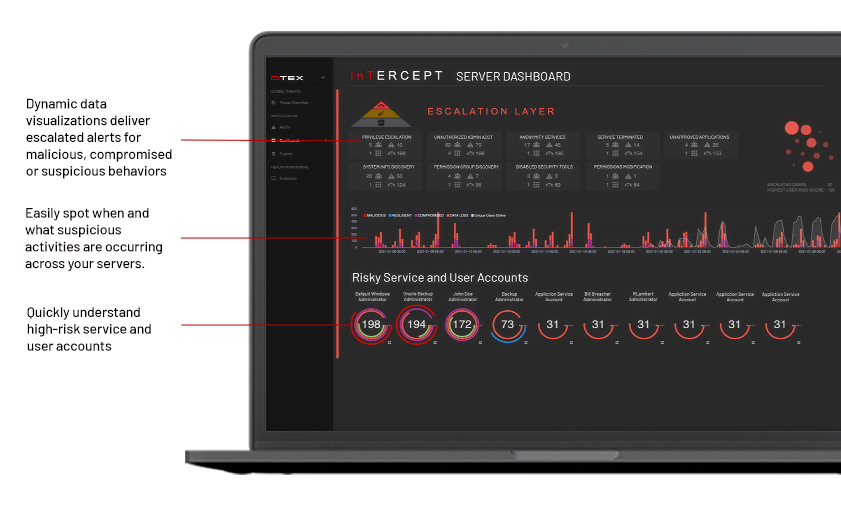
DTEX InTERCEPT – Continuous Server Monitoring @ Scale
DTEX InTERCEPT delivers unmatched visibility to see and stop attacks targeting server infrastructures and trusted software packages that traditional cyber defenses miss. Only DTEX’s patent-pending DMAP+ technology drives intelligent meta-data collection and activity correlation to identify privileged account misuse, unauthorized use of administrative tools, unusual application updates and behavior, systems configuration changes, domain fronting, and more.
Download Now: DTEX Exclusive SolarWinds Report & Best Practices Guidance

Behavior-centric Data Protection & File Lineage Activity Awareness
All Data Loss is an Inside Job
The vast majority of security threats follow a pattern of activity during an attack, and server-infiltration via administrative and superuser accounts or hidden inside packaged applications are no exception. In order to fully understand any incident, visibility into the entire kill chain — not just one or two steps — is imperative. This is because the earlier phases of the kill chain hold the answers to some of the most important questions.

The latest on Workforce Cyber Intelligence

Protect & Respect: 7 Endpoint DLP Capabilities that Empower the Virtual Workforce
How do you protect your organization against data loss, while enabling your workforce to be productive and showing respect for…
Read More
DTEX Insider Threat Mitigation Guide
Guidelines for evaluating Insider Threat Mitigation technology solutions and considerations for building an effective Insider Threat Detection and Response Program…
Read More
SANS Product Review: Smart Enterprise Visibility with DTEX InTERCEPT
Download this report from SANS for an assessment of how DTEX InTERCEPT can help your organization achieve its security objectives.
Read More
