Enterprise Visibility, Protection, and Privacy
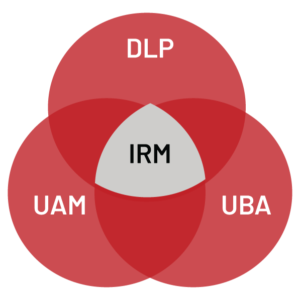 Insider Risk Management solutions have evolved from the convergence of specific attributes taken from Endpoint DLP, User Activity Monitoring (UAM) and User Behavior Analytics (UBA).
Insider Risk Management solutions have evolved from the convergence of specific attributes taken from Endpoint DLP, User Activity Monitoring (UAM) and User Behavior Analytics (UBA).
Importantly, IRM solutions leverage a metadata approach combined with advanced behavioral analysis to arrive at the same outcomes as the Insider Threat Surveillance solutions (i.e., successful prosecution of insider threats). However, some key benefits of the IRM approach are the ability to identify risks and threats without impacting privacy, endpoint performance, and, most importantly, the capability to proactively remediate insider incidents before they actually happen.
AI-Driven Insights and Investigations
Insider risks are a human challenge that require an understanding of behavior through data-driven science. AI-assisted insider risk investigations provide quick insight and an interpretation of user intent to identify and respond to insider risks with greater speed and effectiveness. For analysts, this means having the critical behavioral insights they need, when they need them, to stop insider risks from becoming insider threats.
Insider Threat Surveillance vs. Insider Risk Intelligence
Insider Threat Surveillance tools have evolved from the “Employee Monitoring” software category and have been traditionally deployed to watch targeted high-risk endpoints or for employees with prior negative conduct or suspicious history. These solutions rely on invasive capabilities to react to insider threat activities including computer screen recording, conversation content scanning, file content scanning, email content scanning, and keystroke logging.
Detect, Deter, Disrupt Risky User Behavior
Global Scalability with Dynamic Reporting
Unlike intrusive employee surveillance capabilities that are system resource and network bandwidth intensive by nature, requiring larger than normal processing power from the endpoint device and additional cloud storage, Insider Risk Management offers the ability to readily scale to hundreds of thousands of endpoints with continuous visibility in near real-time. This means out-of-the-box automated reports and dashboards containing intuitive and pivotable visualizations that are easy to understand and actionable within hours of install.
The latest on Insider Risk Management

Insider Risk vs. Insider Threat: What's the Difference?
Earlier this year we published our 2023 Insider Risk Investigations Report and took care to ask the question, what…
Read More
2023 Cost Of Insider Risks Global Report
Featuring first-time insights on how organizations are funding and governing insider risk programs.
Read More
Insider Risk Management vs. Insider Threat Surveillance
Organizations must understand the difference between Insider Risk Management and Insider Threat Surveillance to gain intelligence from their workforce.
Read More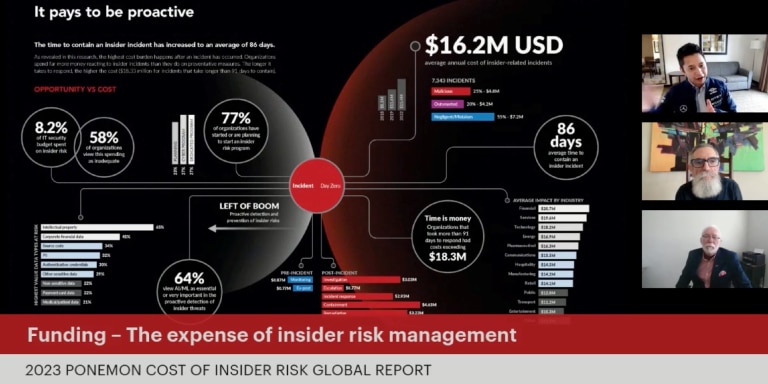
Conversations from the Inside, Ep. 3: Slashing the $16.2M Cost of Insider Risk
The highly anticipated 2023 Cost of Insider Risks Global Report by Ponemon Institute is here, featuring first-time analysis on how…
Read More

