Cyber Sensors Don’t Capture Human Intent
Noisy Alerts Only Cause Confusion & Frustration
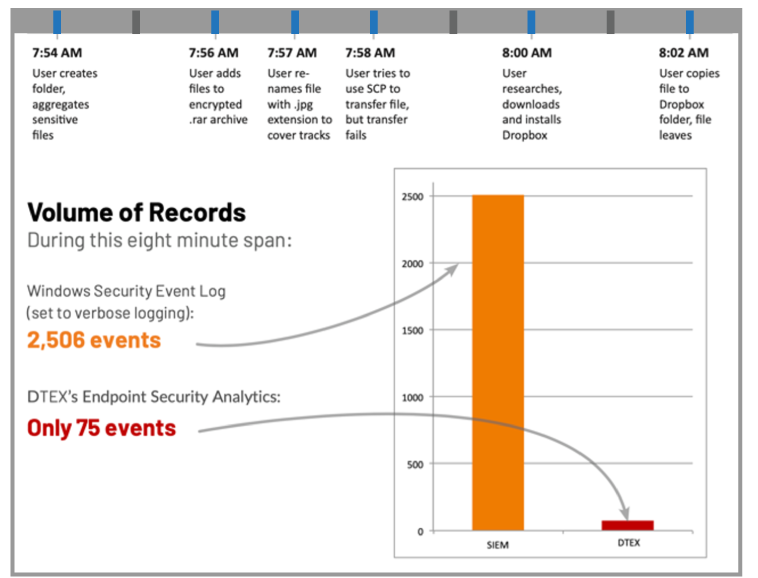
First-generation User Behavior Analytics (UBA) solutions rely solely on interpreting log files and Windows® events. That’s why they miss abnormal and suspicious user activity on the endpoint—like renaming files and other obfuscation techniques.
In fact, most malicious actions look like legitimate business activities—downloading files, copying and pasting data, using screenshots, compressing files, and sharing sensitive information. Without historical and behavioral context, you can’t know when an action is a precursor to an insider’s malicious action or user account takeover by an external actor.

A Single, Noise-free Human Telemetry Signal
Reduce Events by 80% for Faster Evaluation
DTEX InTERCEPT complements SIEM systems to produce a consolidated and transparent view of user activity and behavioral telemetry using a lightweight, cloud-native platform that scales to hundreds of thousands of endpoints and servers in hours with zero impact on user productivity and endpoint performance.
These ‘Indicators of Intent’ provide customers with a better, more contextually rich understanding of how user activity is influencing what’s happening in their environment and if those behaviors are creating risks to data, users and operational processes.
Download the DTEX for Splunk ES solution brief to learn more.
The Latest On Workforce Cyber Intelligence

Protect & Respect: 7 Endpoint DLP Capabilities that Empower the Virtual Workforce
How do you protect your organization against data loss, while enabling your workforce to be productive and showing respect for…
Read More
DTEX Insider Threat Mitigation Guide
Guidelines for evaluating Insider Threat Mitigation technology solutions and considerations for building an effective Insider Threat Detection and Response Program…
Read More
SANS Product Review: Smart Enterprise Visibility with DTEX InTERCEPT
Download this report from SANS for an assessment of how DTEX InTERCEPT can help your organization achieve its security objectives.
Read More

