What is Workforce Cyber Intelligence & Security?
Workforce Cyber Intelligence & Security is a new approach to enterprise data collection and analysis that focuses on understanding how, when, why, where and for how long employees and third parties interact with data, machines, applications, and their peers as they perform their job responsibilities to create a safer, smarter, and more secure enterprise.

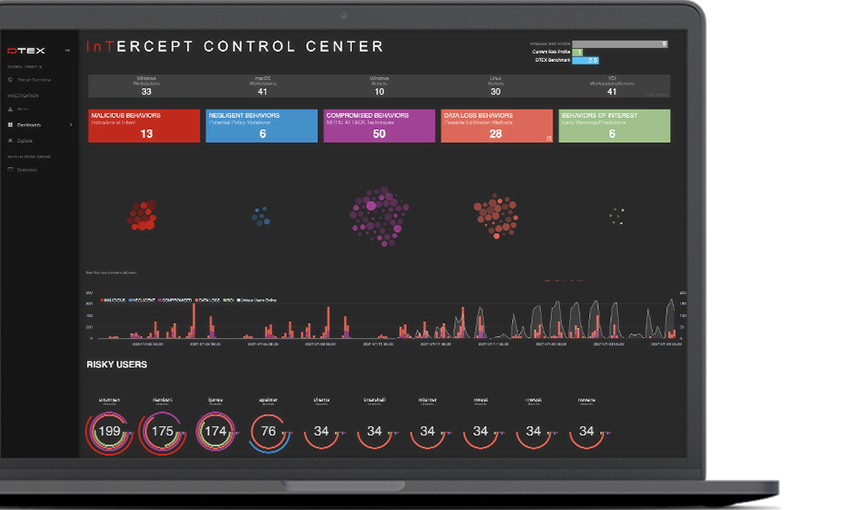
Protect your data. Respect your workforce.
Workforce Cyber Intelligence & Security is designed for today’s modern, distributed workforce model. It provides complete visibility into user and account activity – keeping all data anonymous to protect privacy, and only shining a light on abnormal or inefficient behaviors that indicate risks and areas for operational improvement.
The Three Motivations Behind Workforce Cyber Intelligence
Workforce Cyber Intelligence & Security Use Cases
By collecting and analyzing employee and third-party interactions with data, machines, and applications, Workforce Cyber Intelligence & Security supports a wide range of use cases:
Supporting Employee Wellness
Workforce Cyber Intelligence data can help organizations identify employees at risk of burn-out.
Optimizing Asset and License Utilization
Workforce Cyber Intelligence reveals why employees are using enterprise assets to help IT and procurement teams understand what’s working and what’s not.
Protection from Insider Threats
Identify patterns of behavior to prevent threats before they become realized risks.
Remote Worker Security
Protect WFH employees beyond corporate firewalls or network proxies.
Employee Engagement
Workforce Cyber Intelligence informs conversations about individual performance, professional development, and growth strategies.
Informing Financial and Operational Planning
Measure team performance to aid planning.
Data Loss Prevention
Understand malicious intent long before traditional DLP measures are triggered.
GDPR Compliance
Anonymize data to satisfy GDPR requirements.
Reducing Legal Liability
Identify the personal online activities that put the enterprise at risk – while protecting employee privacy.
Monitoring Employees
Enable monitoring possible without violating trust or privacy.
The Latest On Workforce Cyber Intelligence

Protect & Respect: 7 Endpoint DLP Capabilities that Empower the Virtual Workforce
How do you protect your organization against data loss, while enabling your workforce to be productive and showing respect for…
Read More
DTEX Insider Threat Mitigation Guide
Guidelines for evaluating Insider Threat Mitigation technology solutions and considerations for building an effective Insider Threat Detection and Response Program…
Read More
SANS Product Review: Smart Enterprise Visibility with DTEX InTERCEPT
Download this report from SANS for an assessment of how DTEX InTERCEPT can help your organization achieve its security objectives.
Read More
