In a previous post we discussed why companies need a multi-national strategy when building their Insider Risk Management (IRM) program. Briefly, it’s far too easy for organizations to be tripped up by the regulatory landscape. For each jurisdiction you need to know what data you can capture, what steps you can take, and what you need to report. In this post we’ll present some key points to consider when implementing a strategy.
Start with a Privacy Impact Assessment
A Privacy Impact Assessment (PIA) is an analysis of how personally identifiable information is collected, used, shared, and maintained. Some countries require organizations to conduct a PIA before implementing an IRM solution. PIAs help identify privacy risks, anticipate problems, and evaluate IRM solutions. A PIA should be conducted at the start of an IRM project to help shape the project implementation strategy and determine the most appropriate configuration for the monitoring technology.
Treat Each Country Individually
While there is broad commonality in the IRM compliance requirements between many countries, it’s best to configure monitoring systems for the specific legal requirements of each country. It may also be tempting to adopt policies appropriate to the country with the strictest privacy laws and apply this across all countries. This can backfire when different countries may have contradictory requirements. For example, it is illegal in France to ban the private use of work email. In Germany, this is a common practice. Non-compliance in some countries can also lead to criminal liability.
Focus on Your Acceptable Use Policies
An Acceptable Use Policy (AUP), also known as a Fair Use Policy, is a set of rules for how employees may use company owned assets. They inform employees of the expected standards of use and the potential consequences of infringement. To meet the privacy requirements of most countries, an AUP should define what sanctions will be applied if a user breaches the AUP, making it clear that monitoring may be used to ensure compliance.
In some countries it may be illegal to monitor employees (or to use evidence from monitoring) to reprimand or dismiss an employee unless an AUP has been well communicated to staff. In countries with well-established data protection laws, organizations must provide information about the processing of personal data, including what type of data is collected, who has access to the data, and under what circumstances monitoring may occur.
Avoid Surveillance-centric Solutions
User Activity Monitoring (UAM) solutions allow organizations to measure application usage and intensity, work hours, and other metrics to measure productivity and provide early warnings of employee burnout. They also monitor and log all user actions. This can include keystroke logging, screenshot captures, keyword monitoring, browser and search recording, and video recording of sessions.
UAM is required in U.S. federal agencies to comply with Executive Order 13587, the National Insider Threat Policy and Minimum Standards and Committee on National Security Systems Directive (CNSSD) 504. Organizations must also use UAM carefully to comply with privacy regulations like the EU’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
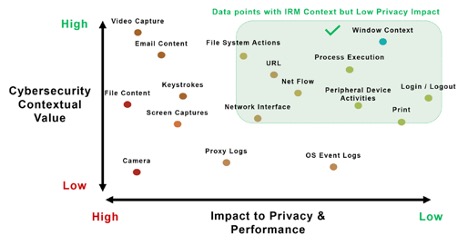
A better approach is to select technologies that minimize the data an organization needs to collect and eliminates collecting intrusive data sources which are unnecessary for improving security. As shown in the figure, by targeting high risk events, teams can manage insider risk without infringing on the privacy of individuals.
Building a multi-national IRM program takes planning to avoid running afoul of local regulations. There is more guidance available in our white paper: Insider Risk Management & Employee Privacy: Guidance for Multinational Organizations. The report also does a deep dive on IRM programs and GDPR. Download it now.


