Making an effort to balance privacy and security is vital for organizations who want to thrive in the new normal. As the findings of our 2021 State of Workforce Privacy and Risk Report showed, more than half (63%) of companies surveyed believe it’s important to protect employee privacy, yet less than half (47%) say they are effective in doing so.
Security should not come at the expense of privacy, yet many companies and enterprises can only achieve internal visibility in an intrusive manner, thus threatening employee morale and trust. Why? Because they think they have no other choice as they need to identify insider threats, prevent data loss, and secure the remote workforce. Good news, privacy and security can co-exist and be better together.
DTEX Workforce Cyber Intelligence and Security solutions leverage pseudonymization techniques to remove data elements that do not comply with GDPR and other privacy regulations. At DTEX, we have always put user privacy first, holding multiple patents on pseudonymization and the promise to our customers and their users to never collect data from intrusive sources.
The DTEX data pseudonymization technique provides customers with a level of visibility needed to detect insider threats alongside maximum protection for privacy of employees and other users. This tactic ensures that privacy laws, both national and international, are adhered to and employee privacy is respected. The metadata collected is stripped of personal identifiable information without affecting the underlying risk model or the ability to investigate suspicious behavior. Combined with advanced user behavior analysis, automatically identifying sudden changes in behavior that indicate insider threats or external risks such as hacker activity, DTEX provides visibility for companies and enterprises to achieve both security and privacy goals without compromising the other.
How do we do it? DTEX’s patented method for processing anonymized data includes obtaining an activity record and generating an anonymization dictionary. This involves detecting a set of data points, assigning a “new” identity to the data and generating an anonymization identified for each data point within the nameless identity. With the anonymization dictionary, the activity record can be obtained and stored in a way that conceals a user’s identity including their username, email address, domain address, IP address, host name, company name, etc.
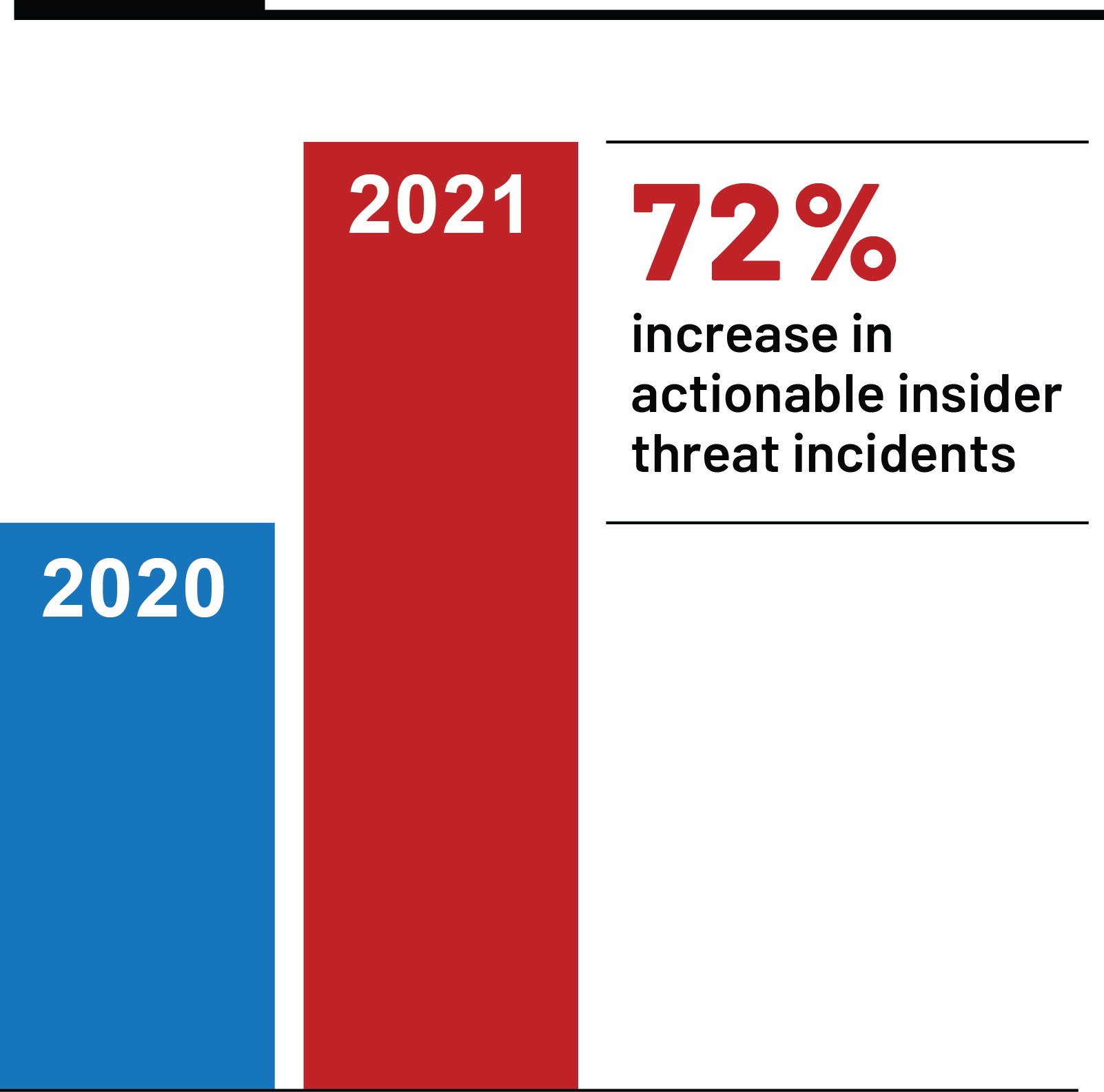
It’s no surprise that companies are now more open to devoting resources to workforce security solutions and insider threat monitoring, given that our 2022 Insider Risk Report showed a +300% year-over-year increase in employees utilizing corporate assets for non-work activities and a 72% year-over-year increase in actionable insider threat incidents. With this rise in protecting against insider threats, companies don’t need to infringe upon employee privacy. This can be achieved by seeking out solutions that completely anonymize data and prioritize privacy and security together.
We encourage you to contact our experts today to learn more about insider risk management and how DTEX can help secure your workforce.

